Un estudio descubrió que las crías eran caníbales y comían los huevos sin eclosionar en el útero
from Tendencias – Digital Trends Español https://ift.tt/35CNcbE
via IFTTT

Un estudio descubrió que las crías eran caníbales y comían los huevos sin eclosionar en el útero
from Tendencias – Digital Trends Español https://ift.tt/35CNcbE
via IFTTT
Ideal para los comunicadores que graban podcasts o programas desde casa
from Tendencias – Digital Trends Español https://ift.tt/3nHOI25
via IFTTT
New research into the malware that set the stage for the megabreach at IT vendor SolarWinds shows the perpetrators spent months inside the company’s software development labs honing their attack before inserting malicious code into updates that SolarWinds then shipped to thousands of customers. More worrisome, the research suggests the insidious methods used by the intruders to subvert the company’s software development pipeline could be repurposed against many other major software providers.
In a blog post published Jan. 11, SolarWinds said the attackers first compromised its development environment on Sept. 4, 2019. Soon after, the attackers began testing code designed to surreptitiously inject backdoors into Orion, a suite of tools used by many Fortune 500 firms and a broad swath of the federal government to manage their internal networks.
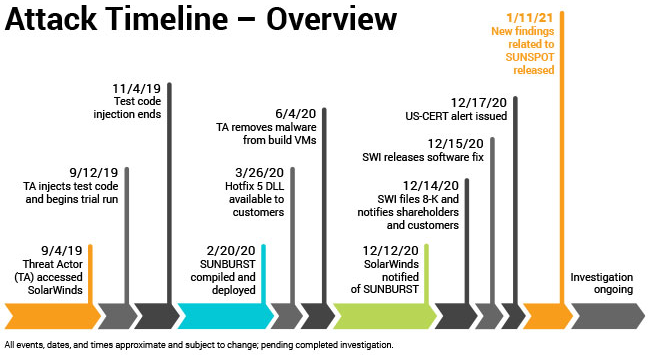
Image: SolarWinds.
According to SolarWinds and a technical analysis from CrowdStrike, the intruders were trying to work out whether their “Sunspot” malware — designed specifically for use in undermining SolarWinds’ software development process — could successfully insert their malicious “Sunburst” backdoor into Orion products without tripping any alarms or alerting Orion developers.
In October 2019, SolarWinds pushed an update to their Orion customers that contained the modified test code. By February 2020, the intruders had used Sunspot to inject the Sunburst backdoor into the Orion source code, which was then digitally signed by the company and propagated to customers via SolarWinds’ software update process.
Crowdstrike said Sunspot was written to be able to detect when it was installed on a SolarWinds developer system, and to lie in wait until specific Orion source code files were accessed by developers. This allowed the intruders to “replace source code files during the build process, before compilation,” Crowdstrike wrote.
The attackers also included safeguards to prevent the backdoor code lines from appearing in Orion software build logs, and checks to ensure that such tampering wouldn’t cause build errors.
“The design of SUNSPOT suggests [the malware] developers invested a lot of effort to ensure the code was properly inserted and remained undetected, and prioritized operational security to avoid revealing their presence in the build environment to SolarWinds developers,” CrowdStrike wrote.
A third malware strain — dubbed “Teardrop” by FireEye, the company that first disclosed the SolarWinds attack in December — was installed via the backdoored Orion updates on networks that the SolarWinds attackers wanted to plunder more deeply.
So far, the Teardrop malware has been found on several government networks, including the Commerce, Energy and Treasury departments, the Department of Justice and the Administrative Office of the U.S. Courts.
SolarWinds emphasized that while the Sunspot code was specifically designed to compromise the integrity of its software development process, that same process is likely common across the software industry.
“Our concern is that right now similar processes may exist in software development environments at other companies throughout the world,” said SolarWinds CEO Sudhakar Ramakrishna. “The severity and complexity of this attack has taught us that more effectively combatting similar attacks in the future will require an industry-wide approach as well as public-private partnerships that leverage the skills, insight, knowledge, and resources of all constituents.”
from Krebs on Security https://ift.tt/3i5sO81
via IFTTT

Hay varias formas de conectar el móvil a la televisión. Entre ellas, tenemos Google Cast, una tecnología algo desconocida, pero que sigue siendo interesante si queremos enviar contenido a nuestro televisor en unos pocos segundos.
Vamos a contarte al detalle qué es Google Cast y cómo puedes usarlo para proyectar el contenido que estás viendo en tu teléfono a tu televisión. De paso, te comentaremos el resto de funciones que se pueden realizar con Googel Cast.
Linking security budgets to breach-protection outcomes helps executives balance spending against risk and earns CISOs greater respect in the C-suite.
from Dark Reading: https://ift.tt/3sjkuGj
via IFTTT

By Nathaniel Popper
Bitcoin owners are getting rich because the cryptocurrency has soared. But what happens when you can’t access that wealth because you forgot the password to your digital wallet?
Published: January 11, 2021 at 06:00PM
from NYT Technology https://ift.tt/3buUpOu
via IFTTT

Uno de los nichos de mercado que encontramos dentro del mercado de los teléfonos móviles es el de los smartphones pensados para gamers. Tenemos modelos de distintas firmas que prometen explotar al máximo los juegos que descargamos y una de ellas, Nubia, tiene nuevo lanzamiento al a vista.
Se trata del heredero del Red Magic 5S que ya conocemos y que fue lanzado en la segunda mitad de 2020. Un terminal que el CEO de Nubia, Ni Fei, ha anunciado en Weibo con algunas pinceladas sobre sus características junto a un llamativo poster. Elementos a los que unen otras especificaciones facilitadas por Digital Chat Station. Continue reading
Demand for secure remote access has skyrocketed during the pandemic. Here Omdia profiles more secure alternatives to virtual private network (VPN) technology.
from Dark Reading: https://ift.tt/3oHzCLE
via IFTTT
Desde consolas de juegos, hasta dispositivos 4K UHD, tenemos los mejores reproductores Blu-ray disponibles.
from Tendencias – Digital Trends Español https://ift.tt/2Pb3Ckr
via IFTTT

Espiar WhatsApp sigue despertando interés, con recurrentes búsquedas en Google pese a que es una actividad completamente ilegal. Del mismo modo, aunque Google Play Store no permite este tipo de prácticas, hay aplicaciones que prometen “espiar” a los usuarios de WhatsApp, aunque ninguna de ellas hace lo que promete.
Hemos hecho algunas búsquedas en la tienda de aplicaciones, para tratar de encontrar esas aplicaciones que prometen rastrear, espiar y demás prácticas ilegales. Te contamos si funcionan, si no lo hacen, formas de espiar WhatsApp y consejos para evitar ser espiado.