Forced to hide his steamy affair with a coworker, hopeless romantic Sri is heartbroken when his lover isn’t interested in a real relationship.
from New On Netflix USA https://ift.tt/YF6TmIQ
via IFTTT

Forced to hide his steamy affair with a coworker, hopeless romantic Sri is heartbroken when his lover isn’t interested in a real relationship.
from New On Netflix USA https://ift.tt/YF6TmIQ
via IFTTT

Tor es una red de túneles virtuales que permite a personas y grupos mejorar su privacidad y seguridad en Internet
(adsbygoogle = window.adsbygoogle || []).push({});
Se dio a conocer el lanzamiento de la nueva rama y versión del popular navegador «Tor Browser 12.0», en el que se ha realizado la transición a la rama Firefox 102 ESR. En esta nueva versión se destacan las compilaciones para dispositivos Apple con chips Apple Silicon, el soporte multilenguaje y mas.
El navegador está enfocado en brindar anonimato, seguridad y privacidad, todo el tráfico se redirige únicamente a través de la red Tor. Es imposible contactar directamente a través de la conexión de red regular del sistema actual, que no permite rastrear la dirección IP real del usuario (en el caso de un ataque al navegador, los atacantes pueden acceder a la configuración de red del sistema, por lo que productos como Whonix debe usarse para bloquear completamente posibles fugas).
(adsbygoogle = window.adsbygoogle || []).push({});
Esta nueva versión que se presenta, se movió a la base de código a las versiones de Firefox 102 ESR y la rama estable tor 0.4.7.12, ademas de que se proporcionan compilaciones multilingües, ya que en versiones anteriores del navegador se tenía que cargar una compilación separada para cada idioma, y ahora se proporciona una compilación universal, lo que le permite al usuario el poder cambiar de idioma sobre la marcha.
Para nuevas instalaciones en Tor Browser 12.0, el idioma correspondiente a la configuración regional establecida en el sistema se seleccionará automáticamente (el idioma se puede cambiar durante la operación), y al pasar de la rama 11.5.x, el idioma utilizado anteriormente en Tor Browser será seleccionado automáticamente (el conjunto multilingüe ocupa unos 105 MB).
Para los nuevos usuarios, Tor Browser 12.0 se actualizará automáticamente cuando se inicie para coincidir con el idioma de su sistema. Y si ha actualizado desde Tor Browser 11.5.8, el navegador intentará mantener el idioma de visualización elegido anteriormente.
De cualquier manera, ahora puede cambiar el idioma de visualización sin descargas adicionales a través del menú Idioma en la configuración general, pero aún así recomendamos que reinicie Tor Browser antes de que el cambio tenga efecto completo.
Naturalmente, agrupar varios idiomas en una sola descarga debería aumentar el tamaño del archivo del navegador Tor; somos muy conscientes de esto; sin embargo, hemos encontrado una manera de ahorrar eficiencia en otros lugares, lo que significa que la diferencia en el tamaño del archivo entre Tor Browser 11.5 y 12.0 es menor.
En la versión para Android, el modo HTTPS-Only está habilitado de forma predeterminada, en el que todas las solicitudes realizadas sin encriptación se redirigen automáticamente a variantes de página segura («http://» se reemplaza por «https://»). En las versiones de escritorio, se habilitó un modo similar en la última versión importante.
(adsbygoogle = window.adsbygoogle || []).push({});
Ademas cabe mencionar que en la versión de Android, se agregó la configuración «Priorizar sitios .onion» a la sección «Privacidad y seguridad», que proporciona reenvío automático a sitios cuando se intenta abrir sitios web que emiten el encabezado HTTP «Onion-Location» indicando la presencia de una variante del sitio en la red Tor.
Otra de las novedades que se destaca de la nueva versión, es la implementación mejorada del mecanismo de buzón que agrega relleno alrededor del contenido de la página web para bloquear la identificación por tamaño de ventana.
Tambien podremos encontrar que se agregó la capacidad de deshabilitar el formato de pantalla ancha para páginas confiables, se eliminaron los bordes de un solo píxel alrededor de los videos de pantalla completa y se eliminaron las posibles fugas de información.
De los demás cambios que se destacan de esta nueva version de Tor:
(adsbygoogle = window.adsbygoogle || []).push({});
Finalmente si estás interesado en poder conocer más al respecto sobre este nuevo lanzamiento puedes consultar los detalles en el siguiente enlace.
Para los interesados en poder probar la nueva version, deben saber que las compilaciones del navegador Tor están preparadas para Linux, Windows y macOS.
Se retrasa la formación de una nueva versión para Android.
from Linux Adictos https://ift.tt/6gj10yk
via IFTTT

A fiery young man clashes with an unflinching forest officer in a south Indian village where spirituality, fate and folklore rule the lands.
from New On Netflix USA https://ift.tt/zq2BKcn
via IFTTT

By BY KAREN WEISE AND DAVID MCCABE
The move by the commission signals an aggressive stance by federal regulators to thwart the expansion of the tech industry’s biggest companies.
Published: December 8, 2022 at 01:10PM
from NYT Technology https://ift.tt/xrTGioO
via IFTTT
Ransomware groups are constantly devising new methods for infecting victims and convincing them to pay up, but a couple of strategies tested recently seem especially devious. The first centers on targeting healthcare organizations that offer consultations over the Internet and sending them booby-trapped medical records for the “patient.” The other involves carefully editing email inboxes of public company executives to make it appear that some were involved in insider trading.

Alex Holden is founder of Hold Security, a Milwaukee-based cybersecurity firm. Holden’s team gained visibility into discussions among members of two different ransom groups: CLOP (a.k.a. “Cl0p” a.k.a. “TA505“), and a newer ransom group known as Venus.
Last month, the U.S. Department of Health and Human Services (HHS) warned that Venus ransomware attacks were targeting a number of U.S. healthcare organizations. First spotted in mid-August 2022, Venus is known for hacking into victims’ publicly-exposed Remote Desktop services to encrypt Windows devices.
Holden said the internal discussions among the Venus group members indicate this gang has no problem gaining access to victim organizations.
“The Venus group has problems getting paid,” Holden said. “They are targeting a lot of U.S. companies, but nobody wants to pay them.”
Which might explain why their latest scheme centers on trying to frame executives at public companies for insider trading charges. Venus indicated it recently had success with a method that involves carefully editing one or more email inbox files at a victim firm — to insert messages discussing plans to trade large volumes of the company’s stock based on non-public information.
“We imitate correspondence of the [CEO] with a certain insider who shares financial reports of his companies through which your victim allegedly trades in the stock market, which naturally is a criminal offense and — according to US federal laws [includes the possibility of up to] 20 years in prison,” one CLOP member wrote to an underling.
“You need to create this file and inject into the machine(s) like this so that metadata would say that they were created on his computer,” they continued. “One of my clients did it, I don’t know how. In addition to pst, you need to decompose several files into different places, so that metadata says the files are native from a certain date and time rather than created yesterday on an unknown machine.”
Holden said it’s not easy to plant emails into an inbox, but it can be done with Microsoft Outlook .pst files, which the attackers may also have access to if they’d already compromised a victim network.
“It’s not going to be forensically solid, but that’s not what they care about,” he said. “It still has the potential to be a huge scandal — at least for a while — when a victim is being threatened with the publication or release of these records.”
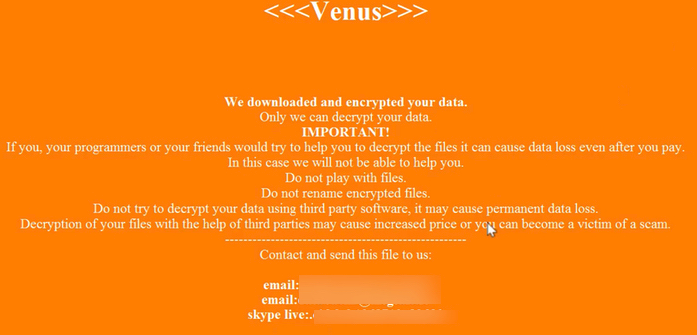
The Venus ransom group’s extortion note. Image: Tripwire.com
Holden said the CLOP ransomware gang has a different problem of late: Not enough victims. The intercepted CLOP communication seen by KrebsOnSecurity shows the group bragged about twice having success infiltrating new victims in the healthcare industry by sending them infected files disguised as ultrasound images or other medical documents for a patient seeking a remote consultation.
The CLOP members said one tried-and-true method of infecting healthcare providers involved gathering healthcare insurance and payment data to use in submitting requests for a remote consultation on a patient who has cirrhosis of the liver.
“Basically, they’re counting on doctors or nurses reviewing the patient’s chart and scans just before the appointment,” Holden said. “They initially discussed going in with cardiovascular issues, but decided cirrhosis or fibrosis of the liver would be more likely to be diagnosable remotely from existing test results and scans.”
While CLOP as a money making collective is a fairly young organization, security experts say CLOP members hail from a group of Threat Actors (TA) known as “TA505,” which MITRE’s ATT&CK database says is a financially motivated cybercrime group that has been active since at least 2014. “This group is known for frequently changing malware and driving global trends in criminal malware distribution,” MITRE assessed.
In April, 2021, KrebsOnSecurity detailed how CLOP helped pioneer another innovation aimed at pushing more victims into paying an extortion demand: Emailing the ransomware victim’s customers and partners directly and warning that their data would be leaked to the dark web unless they can convince the victim firm to pay up.
Security firm Tripwire points out that the HHS advisory on Venus says multiple threat actor groups are likely distributing the Venus ransomware. Tripwire’s tips for all organizations on avoiding ransomware attacks include:
While the above tips are important and useful, one critical area of ransomware preparedness overlooked by too many organizations is the need to develop — and then periodically rehearse — a plan for how everyone in the organization should respond in the event of a ransomware or data ransom incident. Drilling this breach response plan is key because it helps expose weaknesses in those plans that could be exploited by the intruders.
As noted in last year’s story Don’t Wanna Pay Ransom Gangs? Test Your Backups, experts say the biggest reason ransomware targets and/or their insurance providers still pay when they already have reliable backups of their systems and data is that nobody at the victim organization bothered to test in advance how long this data restoration process might take.
“Suddenly the victim notices they have a couple of petabytes of data to restore over the Internet, and they realize that even with their fast connections it’s going to take three months to download all these backup files,” said Fabian Wosar, chief technology officer at Emsisoft. “A lot of IT teams never actually make even a back-of-the-napkin calculation of how long it would take them to restore from a data rate perspective.”
from Krebs on Security https://ift.tt/Ina7hV4
via IFTTT
Don’t keep calling home to a JavaScript server that closed its doors eight years ago!
from Naked Security https://ift.tt/YPz6wA9
via IFTTT
(adsbygoogle = window.adsbygoogle || []).push({});
Tres meses después de la anterior v20.7, ya tenemos aquí a Deepin 20.8. También está disponible como escritorio (DDE), pero lo que han anunciado hace unos instantes es una nueva actualización de punto del sistema operativo más importante en China, siempre y cuando estemos hablando de sistemas basados en Linux. Sus desarrolladores priorizan la estabilidad, por lo menos en parte, y por ello siguen basando su sistema operativo en la última versión LTS del kernel de Linux.
Aunque hay novedades en de todo un poco, suelen llamar la atención las nuevas funciones vistosas, y no hay nada más vistoso que una nueva aplicación en su totalidad. Deepin 20.8 ha presentado Deepin Home, una aplicación propia para agregar información. Entre lo que nos mostrará, se pueden recibir noticias de la comunidad en tiempo real, interactuar con otros, participar en cuestionarios, etc. Además, en el futuro podrán analizar mejor los reportes de bugs.
(adsbygoogle = window.adsbygoogle || []).push({});
Entre el resto de novedades, destaca (o no) que se sigue usando la última versión LTS de Linux, concreramente Linux 5.15.77. También relacionado con el kernel, se ha integrado UTCS, con lo que los dispositivos NVIDIA serán detectados automáticamente y se instalarán los drivers apropiados durante el proceso de instalación. Además, Deepin 20.8 incluye:
Deepin 20.8 ya se puedes descargar desde este enlace.
from Linux Adictos https://ift.tt/7ARpHoJ
via IFTTT
From monsters to kittens to strategy games, these sets will liven things up on nights when everyone is tired of screens.
from Gear Latest https://ift.tt/WLTeC35
via IFTTT
These favorites from the second half of the year teach us about Ukrainian and Chinese-American cuisines, cocktails, and sourdough loaves.
from Gear Latest https://ift.tt/8Zoe7OL
via IFTTT