
By MIKE ISAAC and KATIE BENNER
Dara Khosrowshahi, Uber’s chief executive, is paring back the company’s money-losing businesses.
Published: December 15, 2019 at 06:00PM
from NYT Technology https://ift.tt/2PrDdOv
via IFTTT


By MIKE ISAAC and KATIE BENNER
Dara Khosrowshahi, Uber’s chief executive, is paring back the company’s money-losing businesses.
Published: December 15, 2019 at 06:00PM
from NYT Technology https://ift.tt/2PrDdOv
via IFTTT

By CADE METZ
Researchers say computer systems are learning from lots and lots of digitized books and news articles that could bake old attitudes into new technology.
Published: November 10, 2019 at 06:00PM
from NYT Technology https://ift.tt/33DZ3De
via IFTTT

By ERIN GRIFFITH
StockX is one of several online marketplaces that have turned resales of shoes into a big — and highly valued — business.
Published: June 25, 2019 at 07:00PM
from NYT Technology https://ift.tt/31WyKYz
via IFTTT
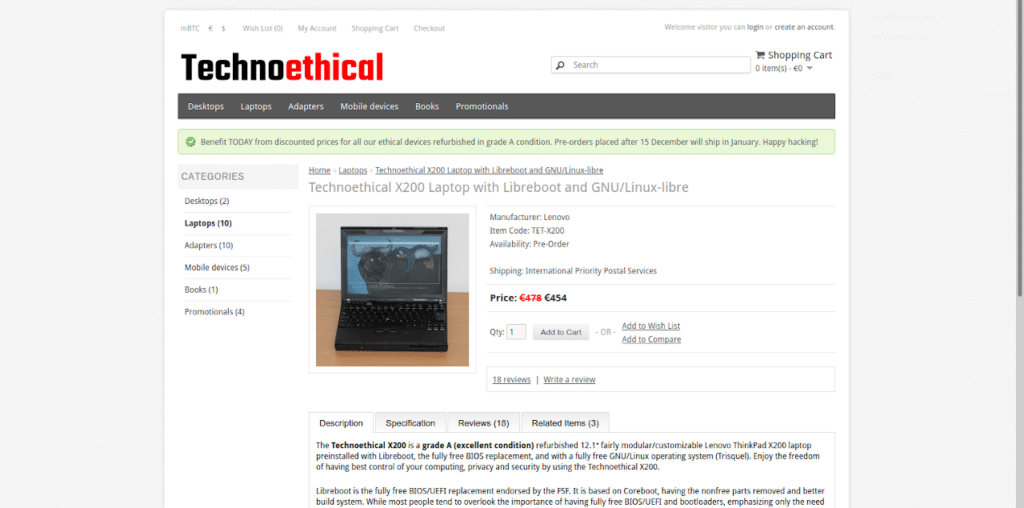
La lista de regalos de la Free Software Foundation incluye una notebook con componentes de hardware y software libre.
Se acercan las fiestas de fin de año. Y, como es habitual la Free Software Foundation publica su lista de recomendaciones de productos que cumplen con sus especificaciones. Si fuiste un niño bueno y no usaste productos privativos, esto es lo que puedes encontrarte debajo del arbolito
La página de la lista comienza con una recomendación:
(adsbygoogle = window.adsbygoogle || []).push({});
Cuando escoja un regalo este año, le instamos a que piense cuidadosamente sobre la elección que está haciendo. ¿Es ese asistente inteligente lo suficientemente inteligente como para respetar los derechos de su amigo o familiar? ¿Esa tableta realmente tiene en mente lo que más les conviene? ¿O ese brillante aparato tiene un costo mucho más alto que su precio?
Luego nos recuerda:
Cuando permitimos que el software propietario creado por Facebook, Amazon, Apple, Google y un sinnúmero de otras empresas se ocupen de nuestras tareas informáticas básicas, ponemos una enorme cantidad de poder en sus manos, poder que explotan libremente. Sólo mediante el uso de software libre, y de dispositivos que ejecutan software libre, podemos recuperar este poder.
El primero de los productos en realidad lo vas a tener que esperar hasta el año que viene. Se trata del Purism Librem 5, del que mis compañeros hablaron bastante en el blog.
(adsbygoogle = window.adsbygoogle || []).push({});
Este teléfono viene con un sistema operativo basado en Linux e interruptores físicos para el micrófono, GPS y conexiones Wi-Fi, De todas maneras se aclara que el microprocesador encargado de las comunicaciones telefónicas contiene software privativo. Se recomienda apagarlo cuando no se hacen llamadas o se envían mensajes.
La segunda opción que la lista de regalos nos ofrece en el apartado smartphones es un Galaxy S3 al que se le cambió el sistema operativo. En lugar del oficial viene con una variante de Android llamada Replicant. En cuanto la tienda de aplicaciones es F-Droid que incluye solo software libre.
De todas formas, se advierte que el procesador encargado de las comunicaciones incluye software privativo.
La primera vez que escribí sobre esta lista,me quejé de que consistía en productos fabricados para Windows a los que se les cambiaba el sistema operativo restringiendo su capacidad. Desde ese momento hasta ahora, la cantidad de hardware con Linux desde el origen aumentó considerablemente.
La oferta en materia de notebooks es el X200, un equipo de configuración variable que utiliza Libreboot para el arranque, y la distribución Linux sin componentes privativos Trisquel.
En caso de que estés buscando una computadora de escritorio, puedes darle una mirada a la Vikings D8. Se la describe como un robusto ordenador de sobremesa que se puede ampliar o reducir según sus necesidades, y que es capaz de hacer de todo, desde la simple navegación web y la reproducción de vídeo hasta tareas más exigentes como la compilación de código.
Las tiendas que la venden te dan la posibilidad de elegir diferentes configuraciones y puedes optar por el ya mencionado Trisquel como sistema operativo o alguna de las otras distribuciones Linux que no incluyen componentes privativos.
Además, si no quieres regalar hardware, en la página vas a encontrar muchos enlaces de libros, videos y discos sin DRM.
from Linux Adictos https://ift.tt/2PW4GXC
via IFTTT
As if the scourge of ransomware wasn’t bad enough already: Several prominent purveyors of ransomware have signaled they plan to start publishing data stolen from victims who refuse to pay up. To make matters worse, one ransomware gang has now created a public Web site identifying recent victim companies that have chosen to rebuild their operations instead of quietly acquiescing to their tormentors.

The message displayed at the top of the Maze Ransomware public shaming site.
Less than 48 hours ago, the cybercriminals behind the Maze Ransomware strain erected a Web site on the public Internet, and it currently lists the company names and corresponding Web sites for eight victims of their malware that have declined to pay a ransom demand.
“Represented here companies dont wish to cooperate with us, and trying to hide our successful attack on their resources,” the site explains in broken English. “Wait for their databases and private papers here. Follow the news!”
KrebsOnSecurity was able to verify that at least one of the companies listed on the site indeed recently suffered from a Maze ransomware infestation that has not yet been reported in the news media.
The information disclosed for each Maze victim includes the initial date of infection, several stolen Microsoft Office, text and PDF files, the total volume of files allegedly exfiltrated from victims (measured in Gigabytes), as well as the IP addresses and machine names of the servers infected by Maze.
As shocking as this new development may be to some, it’s not like the bad guys haven’t warned us this was coming.
“For years, ransomware developers and affiliates have been telling victims that they must pay the ransom or stolen data would be publicly released,” said Lawrence Abrams, founder of the computer security blog and victim assistance site BleepingComputer.com. “While it has been a well-known secret that ransomware actors snoop through victim’s data, and in many cases steal it before the data is encrypted, they never actually carried out their threats of releasing it.”
Abrams said that changed at the end of last month, when the crooks behind Maze Ransomware threatened Allied Universal that if they did not pay the ransom, they would release their files. When they did not receive a payment, they released 700MB worth of data on a hacking forum.
“Ransomware attacks are now data breaches,” Abrams said. “During ransomware attacks, some threat actors have told companies that they are familiar with internal company secrets after reading the company’s files. Even though this should be considered a data breach, many ransomware victims simply swept it under the rug in the hopes that nobody would ever find out. Now that ransomware operators are releasing victim’s data, this will need to change and companies will have to treat these attacks like data breaches.”
The move by Maze Ransomware comes just days after the cybercriminals responsible for managing the “Sodinokibi/rEvil” ransomware empire posted on a popular dark Web forum that they also plan to start using stolen files and data as public leverage to get victims to pay ransoms.
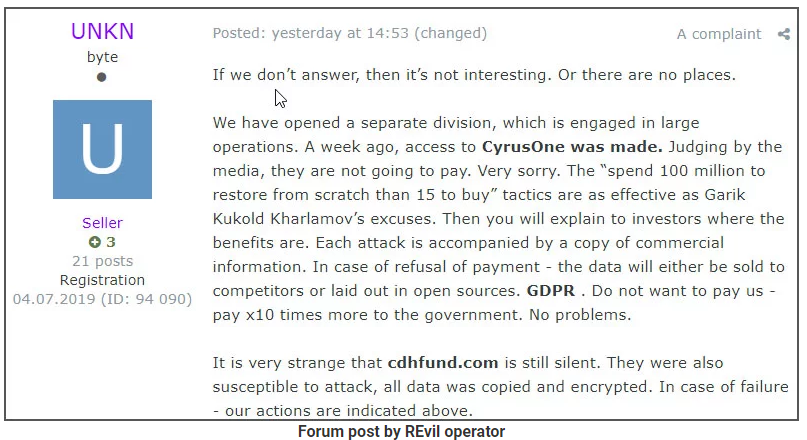
The leader of the Sodinokibi/rEvil ransomware gang promising to name and shame victims publicly in a recent cybercrime forum post. Image: BleepingComputer.
This is especially ghastly news for companies that may already face steep fines and other penalties for failing to report breaches and safeguard their customers’ data. For example, healthcare providers are required to report ransomware incidents to the U.S. Department of Health and Human Services, which often documents breaches involving lost or stolen healthcare data on its own site.
While these victims may be able to avoid reporting ransomware incidents if they can show forensic evidence demonstrating that patient data was never taken or accessed, sites like the one that Maze Ransomware has now erected could soon dramatically complicate these incidents.
from Krebs on Security https://ift.tt/34t660U
via IFTTT
Hace semanas, incluso meses, que la rueda mediática apunta a Samsung y a un Unpacked 2020 con el que los surcoreanos quieren sorprender a la crítica, empezando por una undécima iteración de la familia Galaxy S ciertamente más que filtrada en los medios, y poniendo el broche con la segunda generación de los Galaxy Fold y su diseño plegable. Se repite el cuento de cada fin de curso, con el
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
La entrada Deja volar tu imaginación con estos renders hiperrealistas del nuevo Samsung Galaxy S11 se publicó primero en Andro4all.
from Andro4all https://ift.tt/34nxhKB
via IFTTT
While far less common than breaches in other industry sectors, financial services breaches were more than twice as expensive, per record exposed, than the average for tech businesses.
from Dark Reading: https://ift.tt/2S4XQSB
via IFTTT
Keyfactor says it was able to break nearly 250,000 distinct RSA keys – many associated with routers, wireless access points, and other Internet-connected devices.
from Dark Reading: https://ift.tt/2Eqy577
via IFTTT
DNS amplification attacks continue to dominate distributed denial-of-service (DDoS) attacks, while mobile devices make up a larger share of traffic.
from Dark Reading: https://ift.tt/2M1lk7k
via IFTTT
Meanwhile, the mayor of the city of New Orleans says no ransom money demands were made as her city struggles to recover from a major ransomware attack launched last week.
from Dark Reading: https://ift.tt/2S0PECv
via IFTTT