
By BY MARIA CRAMER
Zia Chishti resigned from the artificial-intelligence company he founded after a former employee accused him of sexual misconduct.
Published: November 19, 2021 at 03:27PM
from NYT Technology https://ift.tt/3oNDZFY
via IFTTT


By BY MARIA CRAMER
Zia Chishti resigned from the artificial-intelligence company he founded after a former employee accused him of sexual misconduct.
Published: November 19, 2021 at 03:27PM
from NYT Technology https://ift.tt/3oNDZFY
via IFTTT
One of the more common ways cybercriminals cash out access to bank accounts involves draining the victim’s funds via Zelle, a “peer-to-peer” (P2P) payment service used by many financial institutions that allows customers to quickly send cash to friends and family. Naturally, a great deal of phishing schemes that precede these bank account takeovers begin with a spoofed text message from the target’s bank warning about a suspicious Zelle transfer. What follows is a deep dive into how this increasingly clever Zelle fraud scam typically works, and what victims can do about it.
Last week’s story warned that scammers are blasting out text messages about suspicious bank transfers as a pretext for immediately calling and scamming anyone who responds via text. Here’s what one of those scam messages looks like:
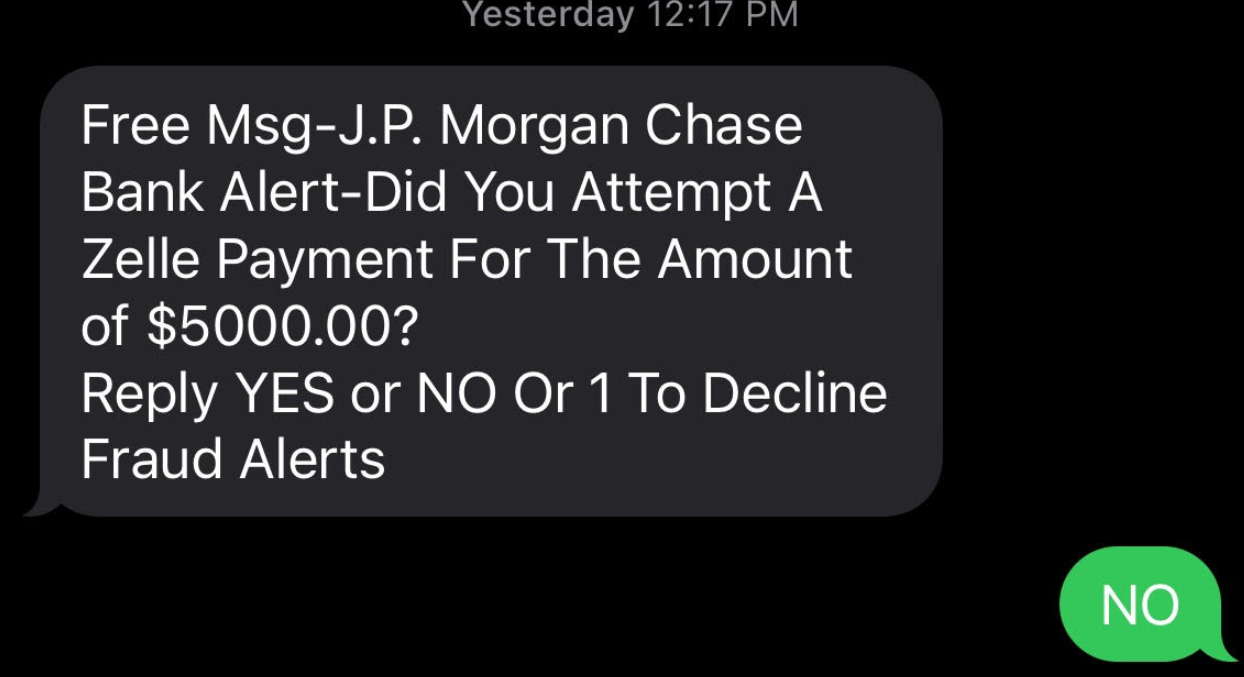
Anyone who responds “yes,” “no” or at all will very soon after receive a phone call from a scammer pretending to be from the financial institution’s fraud department. The caller’s number will be spoofed so that it appears to be coming from the victim’s bank.
To verify the identity of the customer, the fraudster asks for their online banking username, and then tells the customer to read back a passcode sent via text or email. In reality, the fraudster initiates a transaction — such as the “forgot password” feature on the financial institution’s site — which is what generates the 2-step authentication passcode delivered to the member.
Ken Otsuka is a senior risk consultant at CUNA Mutual Group, an insurance company that provides financial services to credit unions. Otsuka said a phone fraudster typically will say something like, “Before I get into the details, I need to verify that I’m speaking to the right person. What’s your username?”
“In the background, they’re using the username with the forgot password feature, and that’s going to generate one of these two-factor authentication passcodes,” Otsuka said. “Then the fraudster will say, ‘I’m going to send you the password and you’re going to read it back to me over the phone.’”
 The fraudster then uses the code to complete the password reset process, and then changes the victim’s online banking password. The fraudster then uses Zelle to transfer the victim’s funds to others.
The fraudster then uses the code to complete the password reset process, and then changes the victim’s online banking password. The fraudster then uses Zelle to transfer the victim’s funds to others.
An important aspect of this scam is that the fraudsters never even need to know or phish the victim’s password. By sharing their username and reading back the one-time code sent to them via email, the victim is allowing the fraudster to reset their online banking password.
Otsuka said in far too many account takeover cases, the victim has never even heard of Zelle, nor did they realize they could move money that way.
“The thing is, many credit unions offer it by default as part of online banking,” Otsuka said. “Members don’t have to request to use Zelle. It’s just there, and with a lot of members targeted in these scams, although they’d legitimately enrolled in online banking, they’d never used Zelle before.” [Curious if your financial institution uses Zelle? Check out their partner list here].
Otsuka said credit unions offering other peer-to-peer banking products have also been targeted, but that fraudsters prefer to target Zelle due to the speed of the payments.
“The fraud losses can escalate quickly due to the sheer number of members that can be targeted on a single day over the course of consecutive days,” Otsuka said.
To combat this scam Zelle introduced out-of-band authentication with transaction details. This involves sending the member a text containing the details of a Zelle transfer – payee and dollar amount – that is initiated by the member. The member must authorize the transfer by replying to the text.
Unfortunately, Otsuka said, the scammers are defeating this layered security control as well.
“The fraudsters follow the same tactics except they may keep the members on the phone after getting their username and 2-step authentication passcode to login to the accounts,” he said. “The fraudster tells the member they will receive a text containing details of a Zelle transfer and the member must authorize the transaction under the guise that it is for reversing the fraudulent debit card transaction(s).”
In this scenario, the fraudster actually enters a Zelle transfer that triggers the following text to the member, which the member is asked to authorize: For example:
“Send $200 Zelle payment to Boris Badenov? Reply YES to send, NO to cancel. ABC Credit Union . STOP to end all messages.”
“My team has consulted with several credit unions that rolled Zelle out or our planning to introduce Zelle,” Otsuka said. “We found that several credit unions were hit with the scam the same month they rolled it out.”
The upshot of all this is that many financial institutions will claim they’re not required to reimburse the customer for financial losses related to these voice phishing schemes. Bob Sullivan, a veteran journalist who writes about fraud and consumer issues, says in many cases banks are giving customers incorrect and self-serving opinions after the thefts.
“Consumers — many who never ever realized they had a Zelle account – then call their banks, expecting they’ll be covered by credit-card-like protections, only to face disappointment and in some cases, financial ruin,” Sullivan wrote in a recent Substack post. “Consumers who suffer unauthorized transactions are entitled to Regulation E protection, and banks are required to refund the stolen money. This isn’t a controversial opinion, and it was recently affirmed by the CFPB here. If you are reading this story and fighting with your bank, start by providing that link to the financial institution.”
“If a criminal initiates a Zelle transfer — even if the criminal manipulates a victim into sharing login credentials — that fraud is covered by Regulation E, and banks should restore the stolen funds,” Sullivan said. “If a consumer initiates the transfer under false pretenses, the case for redress is more weak.”
Sullivan notes that the Consumer Financial Protection Bureau (CFPB) recently announced it was conducting a probe into companies operating payments systems in the United States, with a special focus on platforms that offer fast, person-to-person payments.
“Consumers expect certain assurances when dealing with companies that move their money,” the CFPB said in its Oct. 21 notice. “They expect to be protected from fraud and payments made in error, for their data and privacy to be protected and not shared without their consent, to have responsive customer service, and to be treated equally under relevant law. The orders seek to understand the robustness with which payment platforms prioritize consumer protection under law.”
Anyone interested in letting the CFPB know about a fraud scam that abused a P2P payment platform like Zelle, Cashapp, or Venmo, for example, should send an email describing the incident to BigTechPaymentsInquiry@cfpb.gov. Be sure to include Docket No. CFPB-2021-0017 in the subject line of the message.
In the meantime, remember the mantra: Hang up, Look Up, and Call Back. If you receive a call from someone warning about fraud, hang up. If you believe the call might be legitimate, look up the number of the organization supposedly calling you, and call them back.
from Krebs on Security https://ift.tt/3xcZO5S
via IFTTT

By BY DAVID MCCABE
Jonathan Kanter, who was confirmed by the Senate earlier this week as the assistant attorney general for antitrust, has been a longtime behind-the-scenes player in building arguments against tech giants.
Published: November 19, 2021 at 02:48PM
from NYT Technology https://ift.tt/3qUywA4
via IFTTT
The brand-new Pixel phones are $50 off, and there are discounts on Nest security cameras and smart speakers.
from Gear Latest https://ift.tt/3DzX3xV
via IFTTT
Security leaders can be treated as partners supporting the business and share accountability by establishing relationships with business stakeholders.
from Dark Reading https://ift.tt/3HE6HSn
via IFTTT
Among other things, the pair pretended to be Proud Boys volunteers and sent in a fake video and emails to Republican lawmakers purporting to show Democratic Party attempts to subvert the 2020 presidential elections.
from Dark Reading https://ift.tt/3x3FUKp
via IFTTT

Si ayer veíamos como Google Chat ya nos permite marcar un mensaje como no leído ahora vemos como Mensajes de Google, la otra aplicación de mensajería de la compañía, prepara importantes mejoras en su próxima versión.
El código fuente de su última actualización nos da pistas sobre sus dos próximas novedades. Mensajes e Google se prepara para mejorar la compatibilidad con las reacciones de iMessage y para mostrarnos si es el cumpleaños de la persona con la que estamos chateando.

By BY ERIN GRIFFITH
Defense lawyers are expected to argue that the founder of Theranos, the blood-testing start-up, failed but did not commit fraud.
Published: November 19, 2021 at 12:34PM
from NYT Technology https://ift.tt/30FJL4K
via IFTTT

(adsbygoogle = window.adsbygoogle || []).push({});
Dependency Combobulator es un conjunto de herramientas de código abierto para combatir los ataques de confusión/sustitución de dependencias. Es decir, aquellos ataques que aprovechan un repositorio público o privado de proyectos de software para confundir al gestor de paquetes y colar paquetes que serían supuestas dependencias pero que van dirigidos a realizar algún tipo de ataque.
Apiiro lanzó Dependency Combobulator precisamente para poder luchar contra esto. Un kit de herramientas capaz de detectar y prevenir estos ataques. Estos ataques han sido descubiertos recientemente, y han aumentado como vector de ataque en la actualidad. Es decir, con este kit podrás evitar este tipo de engaños de dependencias que terminan siendo paquetes maliciosos (en vez de instalar la dependencia correcta que se debería instalar para el software que el gestor de paquetes está instalando).
(adsbygoogle = window.adsbygoogle || []).push({});
En estos casos, los usuarios no son conscientes, se fían del gestor de paquetes que es el que automatiza el trabajo de las dependencias. Sin embargo, estarían autorizando código malicioso sin saberlo. Ahí es donde Dependency Combobulator se vuelve interesante, para evaluar diferentes fuentes como GitHub, JFrog Artifactory, etc.
Esta herramienta está desarrollada en lenguaje de programación Python, y usa un motor heurístico que funciona en un modelo de paquete abstracto, lo que proporciona fácil extensibilidad. Además de la flexibilidad, también puede llevar a los profesionales de la seguridad a tomar mejores decisiones. Puede integrarse fácilmente, y se lanza de forma automática.
“A raíz de la decisión del investigador de seguridad Alex Birsan de comprometer los ecosistemas mantenidos por Apple, Microsoft y PayPal a principios de este año, la industria experimentó un brote de ataques similares a la cadena de suministro”, dijo Moshe Zioni , vicepresidente de investigación de seguridad de Apiiro . “Estábamos ansiosos por responder creando un conjunto de herramientas que puede mitigar amenazas similares y ser lo suficientemente flexible y extensible para combatir las futuras oleadas de ataques de confusión de dependencia. Abordar este vector de ataque es esencial para que las organizaciones aseguren con éxito sus cadenas de suministro de software «.
from Linux Adictos https://ift.tt/2Z5njkH
via IFTTT

Tras los numerosos cambios de aspecto que ha ido sufriendo la Play Store en los móviles Android, Google se ha decidido a revitalizar el diseño de la tienda de aplicaciones también en la versión web: el nuevo aspecto está ya disponible en territorios como Corea del Sur y Taiwán. Y tú también puedes probarlo.
Acceder a todas las apps y juegos desde un dispositivo Android acostumbra a ser tan sencillo como abrir la tienda Google Play y navegar por sus innumerables propuestas. No sólo eso, dicha tienda dispone de una manera secundaria de instalar aplicaciones: a distancia y desde cualquier navegador web. ¿Acostumbras a descargar las apps en tu móvil desde el ordenador? Pues se avecinan notables cambios.