
Cryogenic Testing of the Webb Telescope’s Primary Mirror Segment




¿Quieres enviar canciones, documentos o fotos a tu reloj Wear OS desde el teléfono? ¿O disponer de un administrador de archivos con el que visualizar todas las carpetas del smartwatch? Pues NavExplorer es una excelente aplicación para ambas tareas: una vez instalada te permite transferir, cortar, copiar y hasta reproducir el contenido que hayas movido al reloj.
Los relojes inteligentes son cada vez más completos al tiempo que crecen en almacenamiento, en especial para las aplicaciones. Porque uno de sus puntos fuertes es, precisamente, la capacidad de instalar aplicaciones. Aunque puedes aprovechar el espacio para otras tareas, como guardar tu lista de canciones preferida. ¿Que la app de Wear OS se te queda corta? Siempre puedes confiar en NavExplorer.
Gearing up to shred the slopes or dive into the seas? These cameras are made for danger.
from Gear Latest https://ift.tt/33qvk06
via IFTTT
In February, KrebsOnSecurity wrote about a novel cybercrime service that helped attackers intercept the one-time passwords (OTPs) that many websites require as a second authentication factor in addition to passwords. That service quickly went offline, but new research reveals a number of competitors have since launched bot-based services that make it relatively easy for crooks to phish OTPs from targets.

An ad for the OTP interception service/bot “SMSRanger.”
Many websites now require users to supply both a password and a numeric code/OTP token sent via text message, or one generated by mobile apps like Authy and Google Authenticator. The idea is that even if the user’s password gets stolen, the attacker still can’t access the user’s account without that second factor — i.e. without access to the victim’s mobile device or phone number.
The OTP interception service featured earlier this year — Otp[.]agency — advertised a web-based bot designed to trick targets into giving up OTP tokens. The customer would enter a target’s phone number and name, and OTP Agency would initiate an automated phone call that alerts that person about unauthorized activity on their account.
The call would prompt the target to enter an OTP token generated by their phone’s mobile app (“for authentication purposes”), and that code would then get relayed back to the bad guy customers’ panel at the OTP Agency website.
OTP Agency took itself offline within hours of that story. But according to research from cyber intelligence firm Intel 471, multiple new OTP interception services have emerged to fill that void. And all of them operate via Telegram, a cloud-based instant messaging system.
“Intel 471 has seen an uptick in services on the cybercrime underground that allow attackers to intercept one-time password (OTP) tokens,” the company wrote in a blog post today. “Over the past few months, we’ve seen actors provide access to services that call victims, appear as a legitimate call from a specific bank and deceive victims into typing an OTP or other verification code into a mobile phone in order to capture and deliver the codes to the operator. Some services also target other popular social media platforms or financial services, providing email phishing and SIM swapping capabilities.”
Intel471 says one new Telegram OTP bot called “SMSRanger” is popular because it’s remarkably easy to use, and probably because of the many testimonials posted by customers who seem happy with its frequent rate of success in extracting OTP tokens when the attacker already has the target’s “fullz,” personal information such as Social Security number and date of birth. From their analysis:
“Those who pay for access can use the bot by entering commands similar to how bots are used on popular workforce collaboration tool Slack. A simple slash command allows a user to enable various ‘modes’ — scripts aimed as various services — that can target specific banks, as well as PayPal, Apple Pay, Google Pay, or a wireless carrier.
Once a target’s phone number has been entered, the bot does the rest of the work, ultimately granting access to whatever account has been targeted. Users claim that SMSRanger has an efficacy rate of about 80% if the victim answered the call and the full information (fullz) the user provided was accurate and updated.”
Another OTP interception service called SMS Buster requires a tad more effort from a customer, Intel 471 explains:
“The bot provides options to disguise a call to make it appear as a legitimate contact from a specific bank while letting the attackers choose to dial from any phone number. From there, an attacker could follow a script to trick a victim into providing sensitive details such as an ATM personal identification number (PIN), card verification value (CVV) and OTP, which could then be sent to an individual’s Telegram account. The bot, which was used by attackers targeting Canadian victims, gives users the chance to launch attacks in French and English.”
These services are springing up because they work and they’re profitable. And they’re profitable because far too many websites and services funnel users toward multi-factor authentication methods that can be intercepted, spoofed, or misdirected — like SMS-based one-time codes, or even app-generated OTP tokens.
The idea behind true “two-factor authentication” is that the user is required to present two out of three of the following: Something they have (mobile devices); something they know (passwords); or something they are (biometrics). For example, you present your credentials to a website, and the site prompts you to approve the login via a prompt that pops up on your registered mobile device. That is true two-factor authentication: Something you have, and something you know (and maybe also even something you are).
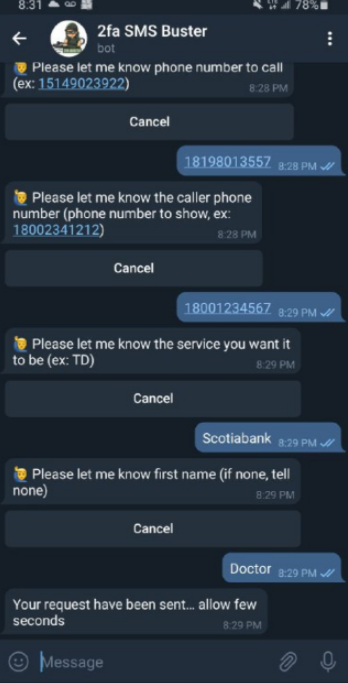
The 2fa SMS Buster bot on Telegram. Image: Intel 471.
In addition, these so-called “push notification” methods include important time-based contexts that add security: They happen directly after the user submits their credentials; and the opportunity to approve the push notification expires after a short period.
But in so many instances, what sites request is basically two things you know (a password and a one-time code) to be submitted through the same channel (a web browser). This is usually still better than no multi-factor authentication at all, but as these services show there are now plenty of options of circumventing this protection.
I hope these OTP interception services make clear that you should never provide any information in response to an unsolicited phone call. It doesn’t matter who claims to be calling: If you didn’t initiate the contact, hang up. Don’t put them on hold while you call your bank; the scammers can get around that, too. Just hang up. Then you can call your bank or whoever else you need.
Unfortunately, those most likely to fall for these OTP interception schemes are people who are less experienced with technology. If you’re the resident or family IT geek and have the ability to update or improve the multi-factor authentication profiles for your less tech-savvy friends and loved ones, that would be a fabulous way to show you care — and to help them head off a potential disaster at the hands of one of these bot services.
When was the last time you reviewed your multi-factor settings and options at the various websites entrusted with your most precious personal and financial information? It might be worth paying a visit to 2fa.directory (formerly twofactorauth[.]org) for a checkup.
from Krebs on Security https://ift.tt/39NlwlX
via IFTTT
The true story of British Intelligence whistleblower Katharine Gun, who leaked a top-secret NSA memo exposing a joint US-UK illegal spying operation.
from New On Netflix USA https://ift.tt/3ohXYhF
via IFTTT
Desperate and without documentation, a woman from Mexico moves into a rundown Cleveland boardinghouse. Then the unsettling cries and eerie visions begin.
from New On Netflix USA https://ift.tt/3zMomCp
via IFTTT
[New Episodes] After uncovering a magical locket that allows her to shrink in size, Polly and her friends set out on big adventures with petite power.
from New On Netflix USA https://ift.tt/35nFyR0
via IFTTT
[New Episodes] Hunter, author, cook and conservationist Steven Rinella treks into the world’s most remote, beautiful regions, bringing game meat from field to table.
from New On Netflix USA https://ift.tt/2X26nIv
via IFTTT

Hace justo un año, llegó al mercado el Withings ScanWatch, un atractivo reloj híbrido con aspecto clásico, pero con todas las prestaciones habituales que encontramos en los smartwatches. Ahora la compañía acaba de anunciar su sucesor, el Withings ScanWatch Horizon.
Esta nueva propuesta, que tiene un precio de, atención, 500 euros, conserva algunas características de su antecesor, incluyendo la capacidad de detectar la apnea del sueño analizando los niveles de oxígeno en sangre y la frecuencia cardíaca, así como el movimiento y la frecuencia respiratoria.
Careful—your Apple Pencil might actually replace your real pencils.
from Gear Latest https://ift.tt/2ZY1XnL
via IFTTT