The vulnerability could give attackers remote root access to the bike’s tablet, researchers report.
from Dark Reading: https://ift.tt/3cN0ypd
via IFTTT

The vulnerability could give attackers remote root access to the bike’s tablet, researchers report.
from Dark Reading: https://ift.tt/3cN0ypd
via IFTTT
Intelligent systems must include the right cybersecurity protections to prevent physical threats to operational technology.
from Dark Reading: https://ift.tt/3q8GJhG
via IFTTT
Oleg Koshkin was arrested in 2019 and faces a maximum penalty of 15 years in prison, the DoJ reports.
from Dark Reading: https://ift.tt/2S3soXd
via IFTTT
Living-off-the-land attacks pose significant risks to organizations and, on top of that, are difficult to detect. Learn the basics about how these attacks operate and ways to limit their damage.
from Dark Reading: https://ift.tt/35twbju
via IFTTT
Son varias las personalidades que han alzado la voz para que se respeten los derechos de la comunidad LGBTQ+.
from Digital Trends Español https://ift.tt/3pZB2Cx
via IFTTT

Durante el verano pasado conocimos que Google Maps comenzó a mostrar la ubicación de los semáforos en sus mapas, pero como era de esperar solo fue lanzada en Estados Unidos con la esperanza de que más pronto que tarde llegará a nuestro país.
Pues bien, ese día por fin ha llegado. Google Maps ya está mostrando los semáforos en España. Ahora al explorar sus maps podemos ver la ubicación de cada uno de los semáforos que hay en cada una de sus calles y carreteras.
There’s no way to anticipate every possible scenario, but the right approach to business continuity can help you respond effectively in any situation.
from Dark Reading: https://ift.tt/3gsMmUD
via IFTTT
Amazon’s big two-day sale event starts soon. Get prepped with our expert advice and the best discounts we’ve found so far.
from Gear Latest https://ift.tt/3gv4Aon
via IFTTT

WhatsApp permite opciones como cambiar la velocidad de las notas de voz, pero sigue sin dejar que las escuchemos antes de enviarlas a un contacto, por lo que no hay forma de saber qué hemos dicho exactamente en el audio antes de mandarlo. Por suerte, hay un sencillo truco para conseguir esto, mientras la app implementa (o no) esta función de forma oficial, como ya permiten rivales como Telegram.
Vamos a enseñarte cómo puedes oír las notas de voz de WhatsApp antes de enviarlas a tus contactos, ya que es un truco bastante sencillo, pero desconocido, que nos permite disfrutar de esta función, aunque WhatSapp no la incorpore de forma oficial.
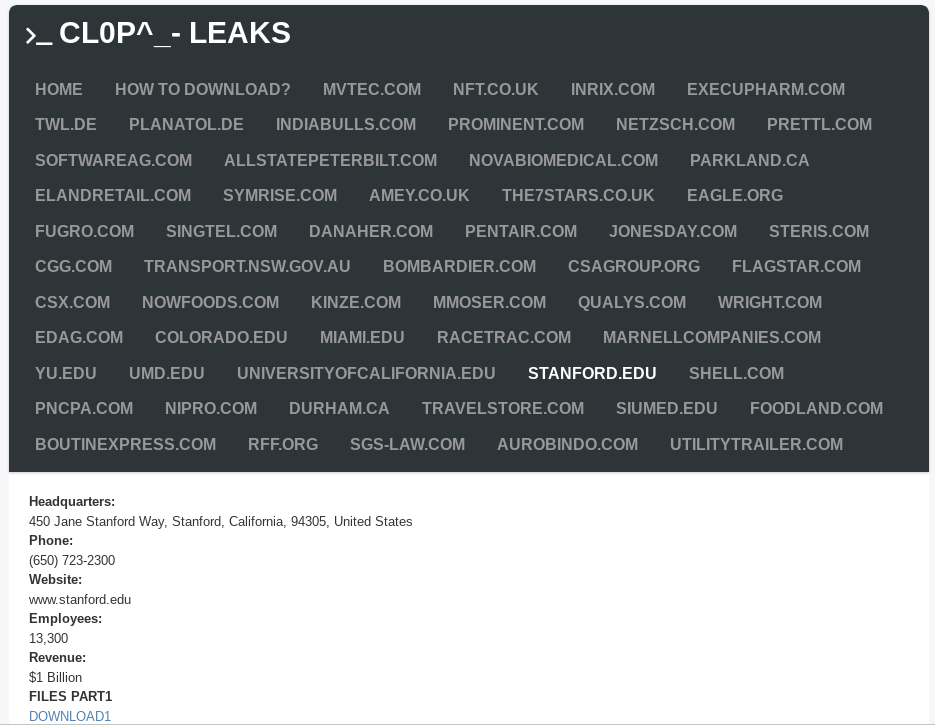
Authorities in Ukraine this week charged six people alleged to be part of the CLOP ransomware group, a cybercriminal gang said to have extorted more than half a billion dollars from victims. Some of CLOP’s victims this year alone include Stanford University Medical School, the University of California, and University of Maryland.

A still shot from a video showing Ukrainian police seizing a Tesla, one of many high-end vehicles seized in this week’s raids on the Clop gang.
According to a statement and videos released today, the Ukrainian Cyber Police charged six defendants with various computer crimes linked to the CLOP gang, and conducted 21 searches throughout the Kyiv region.
First debuting in early 2019, CLOP is one of several ransomware groups that hack into organizations, launch ransomware that encrypts files and servers, and then demand an extortion payment in return for a digital key needed to unlock access.
CLOP has been especially busy over the past six months exploiting four different zero-day vulnerabilities in File Transfer Appliance (FTA), a file sharing product made by California-based Accellion.
The CLOP gang seized on those flaws to deploy ransomware to a significant number of Accellion’s FTA customers, including U.S. grocery chain Krogers, the law firm Jones Day, security firm Qualys, and the Singaporean telecom giant Singtel.
Last year, CLOP adopted the practice of attempting to extract a second ransom demand from victims in exchange for a promise not to publish or sell any stolen data. Terabytes of documents and files stolen from victim organizations that have not paid a data ransom are now available for download from CLOP’s deep web site, including Stanford, UCLA and the University of Maryland.
CLOP’s victim shaming blog on the deep web.
It’s not clear how much this law enforcement operation by Ukrainian authorities will affect the overall operations of the CLOP group. Cybersecurity intelligence firm Intel 471 says the law enforcement raids in Ukraine were limited to the cash-out and money laundering side of CLOP’s business only.
“We do not believe that any core actors behind CLOP were apprehended, due to the fact that they are probably living in Russia,” Intel 471 concluded. “The overall impact to CLOP is expected to be minor although this law enforcement attention may result in the CLOP brand getting abandoned as we’ve recently seen with other ransomware groups like DarkSide and Babuk” [links added].
While CLOP as a moneymaking collective is fairly young organization, security experts say CLOP members hail from a group of Threat Actors (TA) known as “TA505,” which MITRE‘s ATT&CK database says is a financially motivated cybercrime group that has been active since at least 2014. “This group is known for frequently changing malware and driving global trends in criminal malware distribution,” MITRE assessed.
from Krebs on Security https://ift.tt/3ztQ1sJ
via IFTTT