The first step toward identifying and preventing mobile fraud threats is acknowledging that mobile security requires a unique solution.
from Dark Reading: https://ift.tt/2T6dhZ0
via IFTTT

The first step toward identifying and preventing mobile fraud threats is acknowledging that mobile security requires a unique solution.
from Dark Reading: https://ift.tt/2T6dhZ0
via IFTTT
If you bank online and choose weak or re-used passwords, there’s a decent chance your account could be pilfered by cyberthieves — even if your bank offers multi-factor authentication as part of its login process. This story is about how crooks increasingly are abusing third-party financial aggregation services like Mint, Plaid, Yodlee, YNAB and others to surveil and drain consumer accounts online.
Crooks are constantly probing bank Web sites for customer accounts protected by weak or recycled passwords. Most often, the attacker will use lists of email addresses and passwords stolen en masse from hacked sites and then try those same credentials to see if they permit online access to accounts at a range of banks.
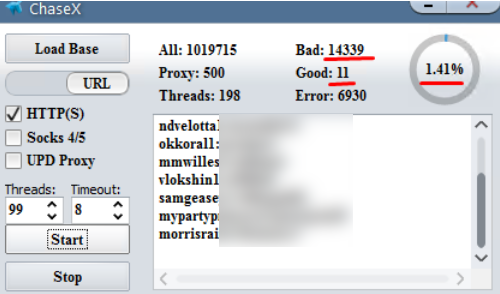
A screenshot of a password-checking tool being used to target Chase Bank customers who re-use passwords from other sites. Image: Hold Security.
From there, thieves can take the list of successful logins and feed them into apps that rely on application programming interfaces (API)s from one of several personal financial data aggregators which help users track their balances, budgets and spending across multiple banks.
A number of banks that do offer customers multi-factor authentication — such as a one-time code sent via text message or an app — have chosen to allow these aggregators the ability to view balances and recent transactions without requiring that the aggregator service supply that second factor. That’s according to Brian Costello, vice president of data strategy at Yodlee, one of the largest financial aggregator platforms.
Costello said while some banks have implemented processes which pass through multi-factor authentication (MFA) prompts when consumers wish to link aggregation services, many have not.
“Because we have become something of a known quantity with the banks, we’ve set up turning off MFA with many of them,” Costello said. “Many of them are substituting coming from a Yodlee IP or agent as a factor because banks have historically been relying on our security posture to help them out.”
Such reconnaissance helps lay the groundwork for further attacks: If the thieves are able to access a bank account via an aggregator service or API, they can view the customer’s balance(s) and decide which customers are worthy of further targeting.
This targeting can occur in at least one of two ways. The first involves spear phishing attacks to gain access to that second authentication factor, which can be made much more convincing once the attackers have access to specific details about the customer’s account — such as recent transactions or account numbers (even partial account numbers).
The second is through an unauthorized SIM swap, a form of fraud in which scammers bribe or trick employees at mobile phone stores into seizing control of the target’s phone number and diverting all texts and phone calls to the attacker’s mobile device.
But beyond targeting customers for outright account takeovers, the data available via financial aggregators enables a far more insidious type of fraud: The ability to link the target’s bank account(s) to other accounts that the attackers control.
That’s because PayPal, Zelle, and a number of other pure-play online financial institutions allow customers to link accounts by verifying the value of microdeposits. For example, if you wish to be able to transfer funds between PayPal and a bank account, the company will first send a couple of tiny deposits — a few cents, usually — to the account you wish to link. Only after verifying those exact amounts will the account-linking request be granted.
Alex Holden is founder and chief technology officer of Hold Security, a Milwaukee-based security consultancy. Holden and his team closely monitor the cybercrime forums, and he said the company has seen a number of cybercriminals discussing how the financial aggregators are useful for targeting potential victims.
Holden said it’s not uncommon for thieves in these communities to resell access to bank account balance and transaction information to other crooks who specialize in cashing out such information.
“The price for these details is often very cheap, just a fraction of the monetary value in the account, because they’re not selling ‘final’ access to the account,” Holden said. “If the account is active, hackers then can go to the next stage for 2FA phishing or social engineering, or linking the accounts with another.”
Currently, the major aggregators and/or applications that use those platforms store bank logins and interactively log in to consumer accounts to periodically sync transaction data. But most of the financial aggregator platforms are slowly shifting toward using the OAuth standard for logins, which can give banks a greater ability to enforce their own fraud detection and transaction scoring systems when aggregator systems and apps are initially linked to a bank account.
That’s according to Don Cardinal, managing director of the Financial Data Exchange (FDX), which is seeking to unite the financial industry around a common, interoperable, and royalty-free standard for secure consumer and business access to their financial data.
“This is where we’re going,” Cardinal said. “The way it works today, you the aggregator or app stores the credentials encrypted and presents them to the bank. What we’re moving to is [an account linking process] that interactively loads the bank’s Web site, you login there, and the site gives the aggregator an OAuth token. In that token granting process, all the bank’s fraud controls are then direct to the consumer.”
Alissa Knight, a senior analyst with the Aite Group, a financial and technology analyst firm, said such attacks highlight the need to get rid of passwords altogether. But until such time, she said, more consumers should take full advantage of the strongest multi-factor authentication option offered by their bank(s), and consider using a password manager, which helps users pick and remember strong and unique passwords for each Web site.
“This is just more empirical data around the fact that passwords just need to go away,” Knight said. “For now, all the standard precautions we’ve been giving consumers for years still stand: Pick strong passwords, avoid re-using passwords, and get a password manager.”
Some of the most popular password managers include 1Password, Dashlane, LastPass and Keepass. Wired.com recently published a worthwhile writeup which breaks down each of these based on price, features and usability.
from Krebs on Security https://ift.tt/2MEw78w
via IFTTT
Apple and Google have announced that they will limit the way audio recorded by their voice assistants, Siri and Google Assistant, are accessed internally by contractors.
from Naked Security https://ift.tt/2YNLPRe
via IFTTT
Receive any strange SMS text messages recently? If you live in the US, there’s a small chance you might have received an SMS with the following text in the last few days from someone called ‘j3ws3r on Twitter’: I’m here to warn the masses about SMS email gateways. Please look up how to disable it […]
from Naked Security https://ift.tt/2KurPO2
via IFTTT
Llevamos todo este 2019 hablando de móviles plegables, ya que este parecía ser el año en el que las compañías tradicionales lanzaran al mercado sus propios terminales plegables, anticipando un poco lo que podría depararnos el futuro. Y, pese a que hemos visto ya varios móviles plegables presentados y en el mercado, lo cierto es que no ha sido un camino de rosas. Samsung ha tenido que retrasar el lanzamiento
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
from Andro4all https://ift.tt/2M1c30p
via IFTTT
A las puertas del gran evento Unpacked de Nueva York en el que Samsung presentará los nuevos Galaxy Note10 y Note10+, la compañía continúa su ronda de anuncios de nuevos productos. Después de haber presentado la nueva Galaxy Tab S6, hoy la surcoreana presenta al mundo la segunda generación de su último reloj deportivo basado en TizenOS, el nuevo Samsung Galaxy Watch Active2. En su momento ya analizamos el Galaxy
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
from Andro4all https://ift.tt/2T6Boqs
via IFTTT

Fuente: Wikipedia
Para los que aún no lo sepan, la biblioteca Glibc (GNU Library C) es una biblioteca muy común empleada en tiempo de ejecución para el software escrito en lenguaje C. Este proyecto de GNU está bajo licencia LGPL y proporciona a los sistemas una serie de llamadas al sistema (syscalls) y otras funciones básicas definidas en ella. Casi todos los programas en lenguaje de programación C hacen uso de ella (incluido el propio kernel).
Está disponible para sistemas GNU basados en el núcleo Linux, aunque es muy portable para soportar varios sistemas y gran cantidad de hardware diferente. Otros sistemas como Kaiku, BeOS y Debian GNU con núcleo Hurd, kFreeBSD también están soportados por esta biblioteca tan importante. Si haces una búsqueda por tu distro, la encontrarás como libc en alguna de sus versiones.
(adsbygoogle = window.adsbygoogle || []).push({});
Pues bien, una vez presentada, debes saber que ahora se ha lanzado la versión glibc 2.30 con interesantes mejoras. Tras este lanzamiento del proyecto GNU C Library 2.30, las optimizaciones y nuevas características van desde soporte para Unicode 12.1 hasta otras mejoras algo más insignificantes. También destaca el soporte para el agrumento –preload para el linker dinámico para precargar objetos compartidos como alternativa a la variable de entorno LD_RELOAD.
Además de eso, tiene nuevas funciones en Linux como getgents64(), gettid(), y tgkill(). En cuanto al soporte POSIX propuesto, también hay novedades con funciones como pthread_cond_clockwait, pthread_mutex_clocklock, pthread_rwlock_clockrdlock, pthread_rwlock_clockwrlock y sem_clockwait. Incluso se ha optimizado el rendimiento para la arquitectura ARM y también concretamente para los procesadores ARM destinados a HPC denominados ThunderX2, se han corregido algunos errores de seguridad, etc.
Espero que para la próxima versión ahora en desarrollo, la 2.31, te pueda comentar muchas más novedades en LxA… Esa estará prevista para febrero de 2020, así que aún quedan unos meses para ver el resultado del desarrollo.
(adsbygoogle = window.adsbygoogle || []).push({});
Para más información – Sitio del proyecto
from Linux Adictos https://ift.tt/2M3Hnf4
via IFTTT
The new wearable from Samsung adds even more health-tracking features to better compete with the fitness-forward Apple Watch.
from Gear Latest https://ift.tt/2YqmwsR
via IFTTT
Hackers know vulnerable systems when they see them, and they also know this: Many government systems are decades old, running Windows 7 and even Windows XP.
from Dark Reading: https://ift.tt/2YIdK97
via IFTTT
What have seven security fixes in FileZilla got to do with 2014’s Heartbleed bug?
from Naked Security https://ift.tt/2GNk9Wi
via IFTTT