Wired reported this week that a 19-year-old working for Elon Musk‘s so-called Department of Government Efficiency (DOGE) was given access to sensitive US government systems even though his past association with cybercrime communities should have precluded him from gaining the necessary security clearances to do so. As today’s story explores, the DOGE teen is a former denizen of ‘The Com,’ an archipelago of Discord and Telegram chat channels that function as a kind of distributed cybercriminal social network for facilitating instant collaboration.
Since President Trump’s second inauguration, Musk’s DOGE team has gained access to a truly staggering amount of personal and sensitive data on American citizens, moving quickly to seize control over databases at the U.S. Treasury, the Office of Personnel Management, the Department of Education, and the Department of Health and Human Resources, among others.
Wired first reported on Feb. 2 that one of the young technologists on Musk’s crew is a 19-year-old high school graduate named Edward Coristine, who reportedly goes by the nickname “Big Balls” online. One of the companies Coristine founded, Tesla.Sexy LLC, was set up in 2021, when he would have been around 16 years old.
“Tesla.Sexy LLC controls dozens of web domains, including at least two Russian-registered domains,” Wired reported. “One of those domains, which is still active, offers a service called Helfie, which is an AI bot for Discord servers targeting the Russian market. While the operation of a Russian website would not violate US sanctions preventing Americans doing business with Russian companies, it could potentially be a factor in a security clearance review.”
Mr. Coristine has not responded to requests for comment. In a follow-up story this week, Wired found that someone using a Telegram handle tied to Coristine solicited a DDoS-for-hire service in 2022, and that he worked for a short time at a company that specializes in protecting customers from DDoS attacks.

A profile photo from Coristine’s WhatsApp account.
Internet routing records show that Coristine runs an Internet service provider called Packetware (AS400495). Also known as “DiamondCDN,” Packetware currently hosts tesla[.]sexy and diamondcdn[.]com, among other domains.
DiamondCDN was advertised and claimed by someone who used the nickname “Rivage” on several Com-based Discord channels over the years. A review of chat logs from some of those channels show other members frequently referred to Rivage as “Edward.”
From late 2020 to late 2024, Rivage’s conversations would show up in multiple Com chat servers that are closely monitored by security companies. In November 2022, Rivage could be seen requesting recommendations for a reliable and powerful DDoS-for-hire service.
Rivage made that request in the cybercrime channel “Dstat,” a core Com hub where users could buy and sell attack services. Dstat’s website dstat[.]cc was seized in 2024 as part of “Operation PowerOFF,” an international law enforcement action against DDoS services.
Coristine’s LinkedIn profile said that in 2022 he worked at an anti-DDoS company called Path Networks, which Wired generously described as a “network monitoring firm known for hiring reformed blackhat hackers.” Wired wrote:
“At Path Network, Coristine worked as a systems engineer from April to June of 2022, according to his now-deleted LinkedIn résumé. Path has at times listed as employees Eric Taylor, also known as Cosmo the God, a well-known former cybercriminal and member of the hacker group UGNazis, as well as Matthew Flannery, an Australian convicted hacker whom police allege was a member of the hacker group LulzSec. It’s unclear whether Coristine worked at Path concurrently with those hackers, and WIRED found no evidence that either Coristine or other Path employees engaged in illegal activity while at the company.”
The founder of Path is a young man named Marshal Webb. I wrote about Webb back in 2016, in a story about a DDoS defense company he co-founded called BackConnect Security LLC. On September 20, 2016, KrebsOnSecurity published data showing that the company had a history of hijacking Internet address space that belonged to others.
Less than 24 hours after that story ran, KrebsOnSecurity.com was hit with the biggest DDoS attack the Internet had ever seen at the time. That sustained attack kept this site offline for nearly 4 days.
The other founder of BackConnect Security LLC was Tucker Preston, a Georgia man who pleaded guilty in 2020 to paying a DDoS-for-hire service to launch attacks against others.
The aforementioned Path employee Eric Taylor pleaded guilty in 2017 to charges including an attack on our home in 2013. Taylor was among several men involved in making a false report to my local police department about a supposed hostage situation at our residence in Virginia. In response, a heavily-armed police force surrounded my home and put me in handcuffs at gunpoint before the police realized it was all a dangerous hoax known as “swatting.”
CosmoTheGod rocketed to Internet infamy in 2013 when he and a number of other hackers set up the Web site exposed[dot]su, which “doxed” dozens of public officials and celebrities by publishing the address, Social Security numbers and other personal information on the former First Lady Michelle Obama, the then-director of the FBI and the U.S. attorney general, among others. The group also swatted many of the people they doxed.
Wired noted that Coristine only worked at Path for a few months in 2022, but the story didn’t mention why his tenure was so short. A screenshot shared on the website pathtruths.com includes a snippet of conversations in June 2022 between Path employees discussing Coristine’s firing.
According to that record, Path founder Marshal Webb dismissed Coristine for making it known that one of its technicians was a Canadian man named Curtis Gervais who was convicted in 2017 of perpetrating dozens of swatting attacks and fake bomb threats — including at least two attempts against our home in 2014.
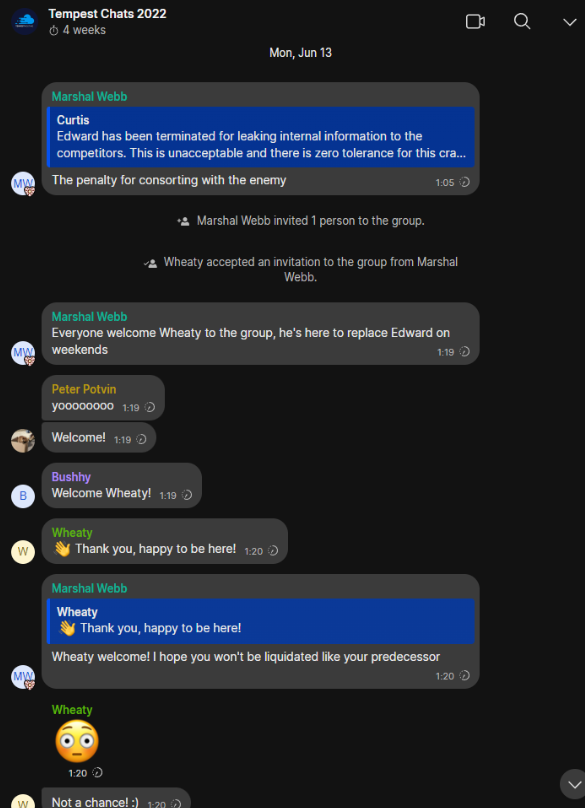
A snippet of text from an internal Path chat room, wherein members discuss the reason for Coristine’s termination: Allegedly, leaking internal company information. Source: Pathtruths.com.
On May 11, 2024, Rivage posted on a Discord channel for a DDoS protection service that is chiefly marketed to members of The Com. Rivage expressed frustration with his time spent on Com-based communities, suggesting that its profitability had been oversold.
“I don’t think there’s a lot of money to be made in the com,” Rivage lamented. “I’m not buying Heztner [servers] to set up some com VPN.”
Rivage largely stopped posting messages on Com channels after that. Wired reports that Coristine subsequently spent three months last summer working at Neuralink, Elon Musk’s brain implant startup.
The trouble with all this is that even if someone sincerely intends to exit The Com after years of consorting with cybercriminals, they are often still subject to personal attacks, harassment and hacking long after they have left the scene.
That’s because a huge part of Com culture involves harassing, swatting and hacking other members of the community. These internecine attacks are often for financial gain, but just as frequently they are perpetrated by cybercrime groups to exact retribution from or assert dominance over rival gangs.
Experts say it is extremely difficult for former members of violent street gangs to gain a security clearance needed to view sensitive or classified information held by the U.S. government. That’s because ex-gang members are highly susceptible to extortion and coercion from current members of the same gang, and that alone presents an unacceptable security risk for intelligence agencies.
And make no mistake: The Com is the English-language cybercriminal hacking equivalent of a violent street gang. KrebsOnSecurity has published numerous stories detailing how feuds within the community periodically spill over into real-world violence.
When Coristine’s name surfaced in Wired‘s report this week, members of The Com immediately took notice. In the following segment from a February 5, 2025 chat in a Com-affiliated hosting provider, members criticized Rivage’s skills, and discussed harassing his family and notifying authorities about incriminating accusations that may or may not be true.
2025-02-05 16:29:44 UTC vperked#0 they got this nigga on indiatimes man
2025-02-05 16:29:46 UTC alexaloo#0 Their cropping is worse than AI could have done
2025-02-05 16:29:48 UTC hebeatsme#0 bro who is that
2025-02-05 16:29:53 UTC hebeatsme#0 yalla re talking about
2025-02-05 16:29:56 UTC xewdy#0 edward
2025-02-05 16:29:56 UTC .yarrb#0 rivagew
2025-02-05 16:29:57 UTC vperked#0 Rivarge
2025-02-05 16:29:57 UTC xewdy#0 diamondcdm
2025-02-05 16:29:59 UTC vperked#0 i cant spell it
2025-02-05 16:30:00 UTC hebeatsme#0 rivage
2025-02-05 16:30:08 UTC .yarrb#0 yes
2025-02-05 16:30:14 UTC hebeatsme#0 i have him added
2025-02-05 16:30:20 UTC hebeatsme#0 hes on discord still
2025-02-05 16:30:47 UTC .yarrb#0 hes focused on stroking zaddy elon
2025-02-05 16:30:47 UTC vperked#0 https://ift.tt/GfZ1kjR
2025-02-05 16:30:50 UTC vperked#0 no fucking way
2025-02-05 16:30:53 UTC vperked#0 they even made a wiki for him
2025-02-05 16:30:55 UTC vperked#0 LOOOL
2025-02-05 16:31:05 UTC hebeatsme#0 no way
2025-02-05 16:31:08 UTC hebeatsme#0 hes not a good dev either
2025-02-05 16:31:14 UTC hebeatsme#0 like????
2025-02-05 16:31:22 UTC hebeatsme#0 has to be fake
2025-02-05 16:31:24 UTC xewdy#0 and theyre saying ts
2025-02-05 16:31:29 UTC xewdy#0 like ok bro
2025-02-05 16:31:51 UTC .yarrb#0 now i wanna know what all the other devs are like…
2025-02-05 16:32:00 UTC vperked#0 “`Coristine used the moniker “bigballs” on LinkedIn and @Edwardbigballer on Twitter, according to The Daily Dot.[“`
2025-02-05 16:32:05 UTC vperked#0 LOL
2025-02-05 16:32:06 UTC hebeatsme#0 lmfaooo
2025-02-05 16:32:07 UTC vperked#0 bro
2025-02-05 16:32:10 UTC hebeatsme#0 bro
2025-02-05 16:32:17 UTC hebeatsme#0 has to be fake right
2025-02-05 16:32:22 UTC .yarrb#0 does it mention Rivage?
2025-02-05 16:32:23 UTC xewdy#0 He previously worked for NeuraLink, a brain computer interface company led by Elon Musk
2025-02-05 16:32:26 UTC xewdy#0 bro what
2025-02-05 16:32:27 UTC alexaloo#0 I think your current occupation gives you a good insight of what probably goes on
2025-02-05 16:32:29 UTC hebeatsme#0 bullshit man
2025-02-05 16:32:33 UTC xewdy#0 this nigga got hella secrets
2025-02-05 16:32:37 UTC hebeatsme#0 rivage couldnt print hello world
2025-02-05 16:32:42 UTC hebeatsme#0 if his life was on the line
2025-02-05 16:32:50 UTC xewdy#0 nigga worked for neuralink
2025-02-05 16:32:54 UTC hebeatsme#0 bullshit
2025-02-05 16:33:06 UTC Nashville Dispatch ##0000 ||@PD Ping||
2025-02-05 16:33:07 UTC hebeatsme#0 must have killed all those test pigs with some bugs
2025-02-05 16:33:24 UTC hebeatsme#0 ur telling me the rivage who failed to start a company
2025-02-05 16:33:28 UTC hebeatsme#0 https://cdn.camp
2025-02-05 16:33:32 UTC hebeatsme#0 who didnt pay for servers
2025-02-05 16:33:34 UTC hebeatsme#0 ?
2025-02-05 16:33:42 UTC hebeatsme#0 was too cheap
2025-02-05 16:33:44 UTC vperked#0 yes
2025-02-05 16:33:50 UTC hebeatsme#0 like??
2025-02-05 16:33:53 UTC hebeatsme#0 it aint adding up
2025-02-05 16:33:56 UTC alexaloo#0 He just needed to find his calling idiot.
2025-02-05 16:33:58 UTC alexaloo#0 He found it.
2025-02-05 16:33:59 UTC hebeatsme#0 bro
2025-02-05 16:34:01 UTC alexaloo#0 Cope in a river dude
2025-02-05 16:34:04 UTC hebeatsme#0 he cant make good money right
2025-02-05 16:34:08 UTC hebeatsme#0 doge is about efficiency
2025-02-05 16:34:11 UTC hebeatsme#0 he should make $1/he
2025-02-05 16:34:15 UTC hebeatsme#0 $1/hr
2025-02-05 16:34:25 UTC hebeatsme#0 and be whipped for better code
2025-02-05 16:34:26 UTC vperked#0 prolly makes more than us
2025-02-05 16:34:35 UTC vperked#0 with his dad too
2025-02-05 16:34:52 UTC hebeatsme#0 time to report him for fraud
2025-02-05 16:34:54 UTC hebeatsme#0 to donald trump
2025-02-05 16:35:04 UTC hebeatsme#0 rivage participated in sim swap hacks in 2018
2025-02-05 16:35:08 UTC hebeatsme#0 put that on his wiki
2025-02-05 16:35:10 UTC hebeatsme#0 thanks
2025-02-05 16:35:15 UTC hebeatsme#0 and in 2021
2025-02-05 16:35:17 UTC hebeatsme#0 thanks
2025-02-05 16:35:19 UTC chainofcommand#0 i dont think they’ll care tbh
Given the speed with which Musk’s DOGE team was allowed access to such critical government databases, it strains credulity that Coristine could have been properly cleared beforehand. After all, he’d recently been dismissed from a job for allegedly leaking internal company information to outsiders.
According to the national security adjudication guidelines (PDF) released by the Director of National Intelligence (DNI), eligibility determinations take into account a person’s stability, trustworthiness, reliability, discretion, character, honesty, judgement, and ability to protect classified information.
The DNI policy further states that “eligibility for covered individuals shall be granted only when facts and circumstances indicate that eligibility is clearly consistent with the national security interests of the United States, and any doubt shall be resolved in favor of national security.”
On Thursday, 25-year-old DOGE staff member Marko Elez resigned after being linked to a deleted social media account that advocated racism and eugenics. Elez resigned after The Wall Street Journal asked the White House about his connection to the account.
“Just for the record, I was racist before it was cool,” the account posted in July. “You could not pay me to marry outside of my ethnicity,” the account wrote on X in September. “Normalize Indian hate,” the account wrote the same month, in reference to a post noting the prevalence of people from India in Silicon Valley.
Elez’s resignation came a day after the Department of Justice agreed to limit the number of DOGE employees who have access to federal payment systems. The DOJ said access would be limited to two people, Elez and Tom Krause, the CEO of a company called Cloud Software Group.
Earlier today, Musk said he planned to rehire Elez after President Trump and Vice President JD Vance reportedly endorsed the idea. Speaking at The White House today, Trump said he wasn’t concerned about the security of personal information and other data accessed by DOGE, adding that he was “very proud of the job that this group of young people” are doing.
A White House official told Reuters on Wednesday that Musk and his engineers have appropriate security clearances and are operating in “full compliance with federal law, appropriate security clearances, and as employees of the relevant agencies, not as outside advisors or entities.”
NPR reports Trump added that his administration’s cost-cutting efforts would soon turn to the Education Department and the Pentagon, “where he suggested without evidence that there could be ‘trillions’ of dollars in wasted spending within the $6.75 trillion the federal government spent in fiscal year 2024.”
GOP leaders in the Republican-controlled House and Senate have largely shrugged about Musk’s ongoing efforts to seize control over federal databases, dismantle agencies mandated by Congress, freeze federal spending on a range of already-appropriated government programs, and threaten workers with layoffs.
Meanwhile, multiple parties have sued to stop DOGE’s activities. ABC News says a federal judge was to rule today on whether DOGE should be blocked from accessing Department of Labor records, following a lawsuit alleging Musk’s team sought to illegally access highly sensitive data, including medical information, from the federal government.
At least 13 state attorney general say they plan to file a lawsuit to stop DOGE from accessing federal payment systems containing Americans’ sensitive personal information, reports The Associated Press.
Reuters reported Thursday that the U.S. Treasury Department had agreed not to give Musk’s team access to its payment systems while a judge hearing arguments in a lawsuit by employee unions and retirees alleging Musk illegally searched those records.
Ars Technica writes that The Department of Education (DoE) was sued Friday by a California student association demanding an “immediate stop” to DOGE’s “unlawfully” digging through student loan data to potentially dismantle the DoE.
from Krebs on Security https://ift.tt/ijyuL8C
via IFTTT




