
By Stuart A. Thompson
The false claim, which has circulated in recent elections, is based on a misunderstanding of how votes are collected and reported.
Published: November 1, 2024 at 08:00PM
from NYT Technology https://ift.tt/WVrvSRh
via IFTTT


By Stuart A. Thompson
The false claim, which has circulated in recent elections, is based on a misunderstanding of how votes are collected and reported.
Published: November 1, 2024 at 08:00PM
from NYT Technology https://ift.tt/WVrvSRh
via IFTTT

By Kate Conger
The change, starting next Friday, lifts a dominant player in artificial intelligence over its chip-making rival, which has struggled to keep up.
Published: November 1, 2024 at 05:30PM
from NYT Technology https://ift.tt/m0il4gb
via IFTTT

By Kashmir Hill and Hang Do Thi Duc
I thought it would make me put glue on pizza, but instead it entertained my children and got me to finally paint my office. How could it transform our daily lives?
Published: November 1, 2024 at 04:07PM
from NYT Technology https://ift.tt/DBERKve
via IFTTT
A number of cybercriminal innovations are making it easier for scammers to cash in on your upcoming travel plans. This story examines a recent spear-phishing campaign that ensued when a California hotel had its booking.com credentials stolen. We’ll also explore an array of cybercrime services aimed at phishers who target hotels that rely on the world’s most visited travel website.
According to the market share website statista.com, booking.com is by far the Internet’s busiest travel service, with nearly 550 million visits in September. KrebsOnSecurity last week heard from a reader whose close friend received a targeted phishing message via SMS within minutes of making a reservation at a California hotel via booking.com.
The missive bore the name of the hotel and referenced details from their reservation, claiming that booking.com’s anti-fraud system required additional information about the customer before the reservation could be finalized.

The phishing SMS our reader’s friend received after making a reservation at booking.com in late October.
In an email to KrebsOnSecurity, booking.com confirmed one of its partners had suffered a security incident that allowed unauthorized access to customer booking information.
“Our security teams are currently investigating the incident you mentioned and can confirm that it was indeed a phishing attack targeting one of our accommodation partners, which unfortunately is not a new situation and quite common across industries,” booking.com replied. “Importantly, we want to clarify that there has been no compromise of Booking.com’s internal systems.”
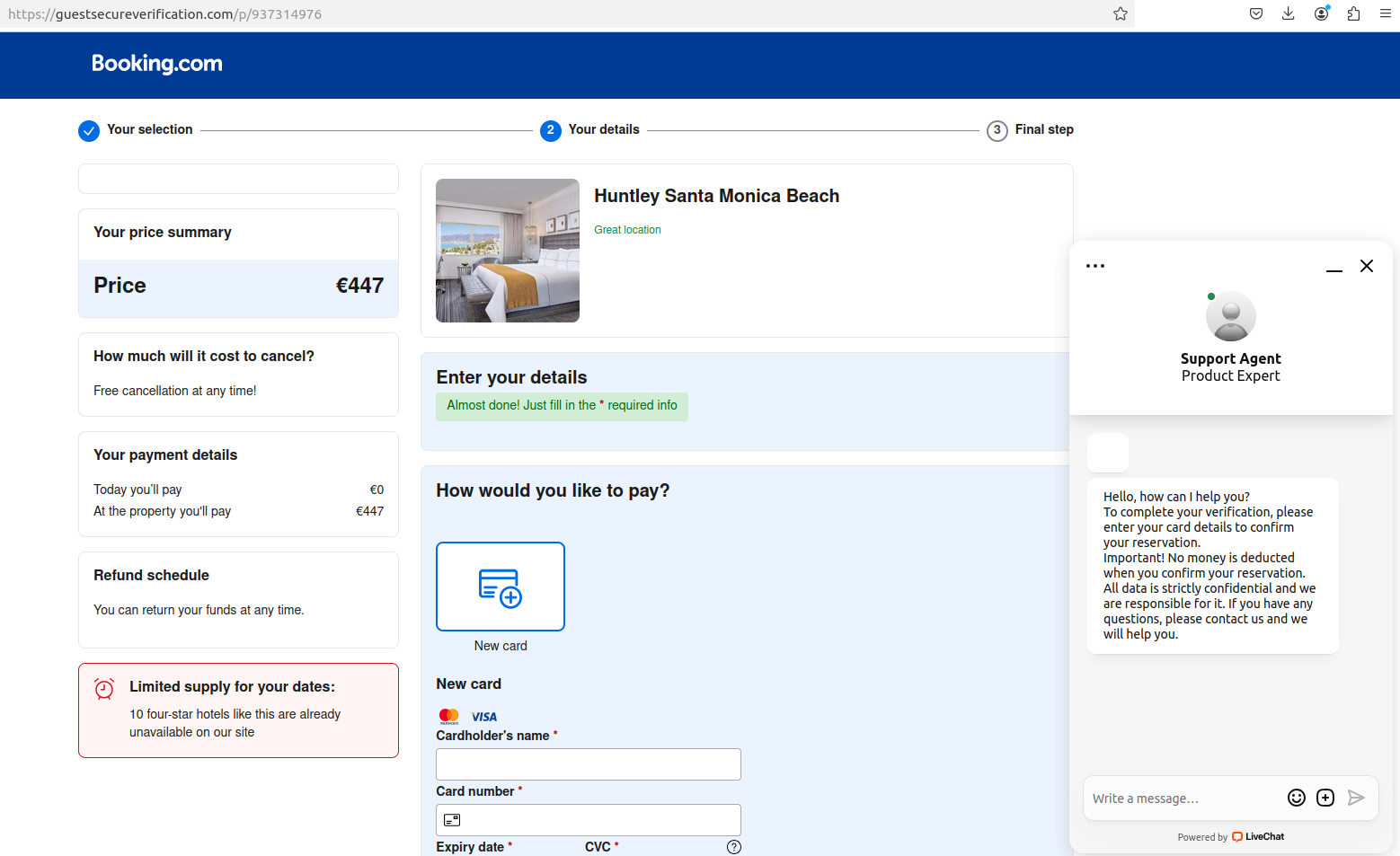
The phony booking.com website generated by visiting the link in the text message.
Booking.com said it now requires 2FA, which forces partners to provide a one-time passcode from a mobile authentication app (Pulse) in addition to a username and password.
“2FA is required and enforced, including for partners to access payment details from customers securely,” a booking.com spokesperson wrote. “That’s why the cybercriminals follow-up with messages to try and get customers to make payments outside of our platform.”
“That said, the phishing attacks stem from partners’ machines being compromised with malware, which has enabled them to also gain access to the partners’ accounts and to send the messages that your reader has flagged,” they continued.
It’s unclear, however, if the company’s 2FA requirement is enforced for all or just newer partners. Booking.com did not respond to questions about that, and its current account security advice urges customers to enable 2FA.
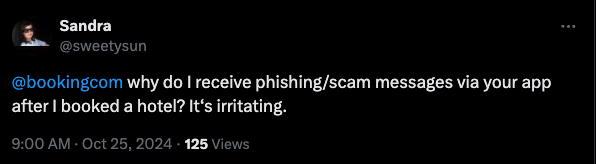
A scan of social media networks showed this is not an uncommon scam.
In November 2023, the security firm SecureWorks detailed how scammers targeted booking.com hospitality partners with data-stealing malware. SecureWorks said these attacks had been going on since at least March 2023.
“The hotel did not enable multi-factor authentication (MFA) on its Booking.com access, so logging into the account with the stolen credentials was easy,” SecureWorks said of the booking.com partner it investigated.
In June 2024, booking.com told the BBC that phishing attacks targeting travelers had increased 900 percent, and that thieves taking advantage of new artificial intelligence (AI) tools were the primary driver of this trend.
Booking.com told the BCC the company had started using AI to fight AI-based phishing attacks. Booking.com’s statement said their investments in that arena “blocked 85 million fraudulent reservations over more than 1.5 million phishing attempts in 2023.”
The domain name in the phony booking.com website sent via SMS to our reader’s friend — guestssecureverification[.]com — was registered to the email address ilotirabec207@gmail.com. According to DomainTools.com, this email address was used to register more than 700 other phishing domains in the past month alone.
Many of the 700+ domains appear to target hospitality companies, including platforms like booking.com and Airbnb. Others seem crafted to phish users of Shopify, Steam, and a variety of financial platforms. A full, defanged list of domains is available here.
A cursory review of recent posts across dozens of cybercrime forums monitored by the security firm Intel 471 shows there is a great demand for compromised booking.com accounts belonging to hotels and other partners.
One post last month on the Russian-language hacking forum BHF offered up to $5,000 for each hotel account. This seller claims to help people monetize hacked booking.com partners, apparently by using the stolen credentials to set up fraudulent listings.
A service advertised on the English-language crime community BreachForums in October courts phishers who may need help with certain aspects of their phishing campaigns targeting booking.com partners. Those include more than two million hotel email addresses, and services designed to help phishers organize large volumes of phished records. Customers can interact with the service via an automated Telegram bot.
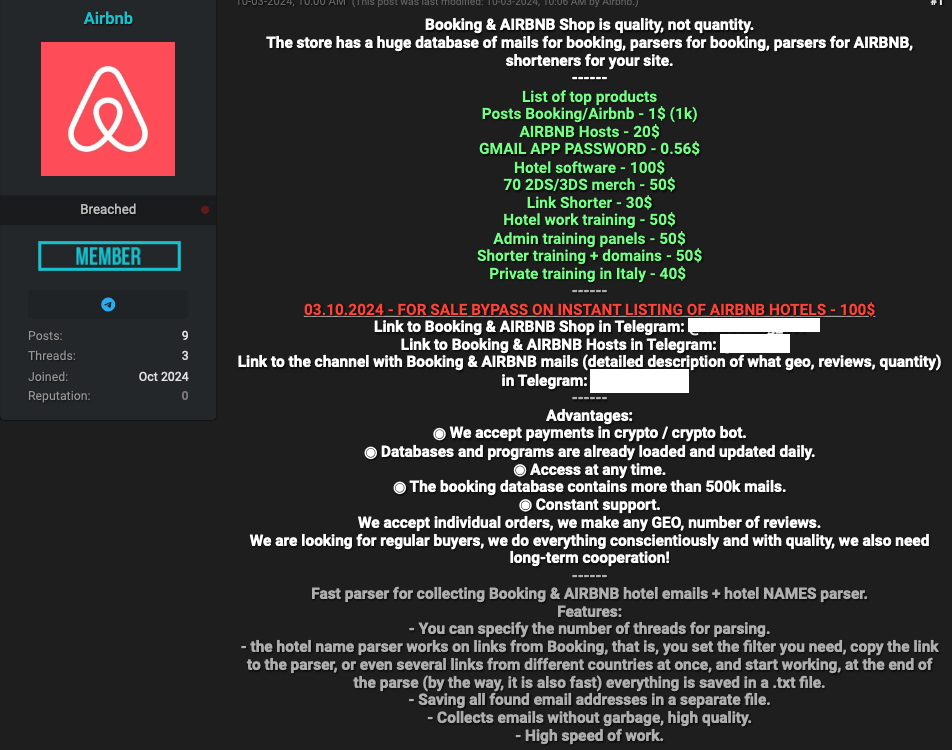
Some cybercriminals appear to have used compromised booking.com accounts to power their own travel agencies catering to fellow scammers, with up to 50 percent discounts on hotel reservations through booking.com. Others are selling ready-to-use “config” files designed to make it simple to conduct automated login attempts against booking.com administrator accounts.
SecureWorks found the phishers targeting booking.com partner hotels used malware to steal credentials. But today’s thieves can just as easily just visit crime bazaars online and purchase stolen credentials to cloud services that do not enforce 2FA for all accounts.
That is exactly what transpired over the past year with many customers of the cloud data storage giant Snowflake. In late 2023, cybercriminals figured out that while tons of companies had stashed enormous amounts of customer data at Snowflake, many of those customer accounts were not protected by 2FA.
Snowflake responded by making 2FA mandatory for all new customers. But that change came only after thieves used stolen credentials to siphon data from 160 companies — including AT&T, Lending Tree and TicketMaster.
from Krebs on Security https://ift.tt/9ZzSjpf
via IFTTT
PAHO to facilitate access to maternal vaccines to protect babies in the Americas from respiratory syncytial virus
Oscar Reyes
from PAHO/WHO | Pan American Health Organization https://ift.tt/MXfYny3
via IFTTT
Tuberculosis resurges as top infectious disease killer
Cristina Mitchell
from PAHO/WHO | Pan American Health Organization https://ift.tt/knJBqUf
via IFTTT

By Stuart A. Thompson
The gathering had nothing to do with the election. That didn’t stop conspiracy theorists from spreading falsehoods.
Published: November 1, 2024 at 10:22AM
from NYT Technology https://ift.tt/G6fw0Fe
via IFTTT

By Steven Lee Myers and Stuart A. Thompson
Though a larger coalition of fact checkers has disbanded, a team of students and researchers at the University of Washington in Seattle is still working to document how lies online threaten to undermine this year’s presidential race.
Published: November 1, 2024 at 10:22AM
from NYT Technology https://ift.tt/wtcqunY
via IFTTT

En la actualidad y durante mucho tiempo, Google ha sido y es el rey de las búsquedas por Internet. Algunos, como un servidor, lo usamos menos cuando nos enteramos del tema de la privacidad y cómo se las gastaba, pero somos una minoría. Cuando la compañía — Alphabet — se enteró de lo que podía hacer ChatGPT, se dice que internamente activaron el código rojo, y esa alarma tiene que estar ahora más presente que nunca tras el inicio de la disponibilidad general de ChatGPT Search.
Antes de continuar, me gustaría aclarar algo: ChatGPT Search no es lo mismo que SearchGPT. Lo segundo es un buscador impulsado por inteligencia artificial, lo que desde mi punto de vista será aún más peligroso para Google. ChatGPT Search no es más que una mejora de la función de búsqueda de GPT-4o. Desde esa cuarta versión mejorada, podemos pedirle que realice búsquedas, pero ahora que se ha implementado este Search, además de mostrar texto también muestra otro tipo de información, como imágenes, tarjetas o vídeos.
ChatGPT Search no está disponible para todos, no aún. Desde este 31 de octubre, pueden usarlo los suscriptores de Plus y Team, y también aquellos que llegaron a tiempo a la lista de espera de SearchGPT. También aparece en la aplicación móvil, por lo menos en mi caso, pero esto puede ser parte de un despliegue gradual como el que ya me dieron con la función de voz.
¿Y cómo funciona? Al principio, ChatGPT sólo admitía texto, y amplió sus capacidades con GPT-4o al admitir también imágenes. Más adelante, el clip que permitía adjuntar imágenes también permitió adjuntar archivos, y ahora además hay una bola del mundo que nos permitirá realizar esas búsquedas.
Como acabamos de explicar, esa bola del mundo no aparece en todos los escenarios. Yo la veo en la aplicación de mi móvil, pero no en chatgpt.com. Lo que sí veo es que si le pido que busque algo, ahora lo hace y añade esa información que no me facilitaba hasta hace unas horas. Como muestra, un botón, o unos gatitos verdes que es lo primero que se me ha ocurrido:

Lo que sí hay que tener en cuenta es que ChatGPT Search es parte de GPT-4o, y ese modelo no es gratuito como GPT4. Podemos realizar consultas, pero a los pocos mensajes usará la versión gratuita y perderá su capacidad de buscar. Se espera que sea diferente cuando SearchGPT llegue oficialmente. En ese momento Google sí tendrá motivos para preocuparse. Ahora mismo, mientras sea una función de pago o de uso limitado, puede estar tranquilo que seguirá con la corona del buscador favorito por la mayoría.
from Linux Adictos https://ift.tt/ESNnIpY
via IFTTT

No sé si es una sensación personal, pero creo que las aguas que se agitaron tras la compra de este popular programa por parte de Muse Group ya están totalmente calmadas. Si no es así, lo parece, y no le faltará mucho. Ya no hay noticias alarmantes sobre su uso, y las que hablaban de alternativas ya no hacen tanto ruido. Y es que esta semana ha llegado Audacity 3.7, una actualización mediana del editor de ondas, entre otras cosas, más popular de los que se pueden usar en Linux.
Aunque eso de etiquetar de mediano este lanzamiento es ser muy generoso por nuestra parte. Ellos no lo hacen. Aunque han facilitado una lista de cambios, la que tenéis a continuación, se podría resumir todo en que se han realizado correcciones de errores y mejoras de rendimiento.
Audacity 4.0 ya está en desarrollo, y entre sus novedades encontraremos una nueva interfaz de usuario. No hay imágenes, pero así lo han prometido. Próximamente habrá más información, pero de momento ya se puede descargar la AppImage de Audacity 3.7 desde el siguiente botón.
.boton {color: white; background-color: grey; padding: 20px; font-size: 2rem; text-decoration: none; border-radius: 10px; position: relative; top: 15px; border: 4px solid #555;}.boton:hover {box-shadow:1px 1px 2.5px black !important;}
from Linux Adictos https://ift.tt/qFsSVWx
via IFTTT