The parents of a 19-year-old Connecticut honors student accused of taking part in a $243 million cryptocurrency heist in August were carjacked a week later — while out house-hunting in a brand new Lamborghini. Prosecutors say the couple was beaten and briefly kidnapped by six young men who traveled from Florida as part of a botched plan to hold the parents for ransom.

Image: ABC7NY. youtube.com/watch?v=xoiaGzwrunY
Late in the afternoon of Aug. 25, 2024 in Danbury, Ct., a married couple in their 50s pulled up to a gated community in a new Lamborghini Urus (investigators say the sports car still had temporary tags) when they were intentionally rear-ended by a Honda Civic.
A witness told police they saw three men exit a van that was following the Honda, and said the men began assaulting the couple and forcing them into the van. Local police officers spotted the van speeding from the scene and pursued it, only to find the vehicle crashed and abandoned a short distance away.
Inside the disabled van the police found the couple with their hands and feet bound in duct tape, the man visibly bruised after being assaulted with a baseball bat. Danbury police soon reported arresting six suspects in the kidnapping, all men aged 18-26 from Florida. They also recovered the abandoned Lamborghini from a wooded area.
A criminal complaint (PDF) filed on Sept. 24 against the six men does not name the victims, referring to them only as a married couple from Danbury with the initials R.C. and S.C. But prosecutors in Connecticut said they were targeted “because the co-conspirators believed the victims’ son had access to significant amounts of digital currency.”
What made the Miami men so convinced R.C. and S.C.’s son was loaded with cryptocurrency? Approximately one week earlier, on Aug. 19, a group of cybercriminals that allegedly included the couple’s son executed a sophisticated phone-based social engineering attack in which they stole $243 million worth of cryptocurrency from a victim in Washington, D.C.
That’s according to ZachXBT, a frequently cited crypto crime investigator who published a lengthy thread that broke down how the theft was carried out and ultimately exposed by the perpetrators themselves.
ZachXBT’s post included a screen recording of a Discord chat session made by one of the participants to the $243 million robbery, noting that two of the people involved managed to leak the username of the Microsoft Windows PCs they were using to participate in the chat.
One of the usernames leaked during the chat was Veer Chetal. According to ZachXBT, that name corresponds to a 19-year-old from Danbury who allegedly goes by the nickname “Wiz,” although in the leaked video footage he allegedly used the handle “Swag.” Swag was reportedly involved in executing the early stages of the crypto heist — gaining access to the victim’s Gmail and iCloud accounts.
A still shot from a video screenshare in which one of the participants on the Discord voice chat used the Windows username Veer Chetal. Image: x.com/zachxbt
The same day ZachXBT published his findings, a criminal indictment was issued in Washington D.C. charging two of the men he named as involved in the heist. Prosecutors allege Malone “Greavys” Lam, 20, of Miami and Los Angeles, and Jeandiel “Box” Serrano, 21, of Los Angeles conspired to steal and launder over $230 million in cryptocurrency from a victim in Washington, D.C. The indictment alleges Lam and Serrano were helped by other unnamed co-conspirators.
“Lam and Serrano then allegedly spent the laundered cryptocurrency proceeds on international travel, nightclubs, luxury automobiles, watches, jewelry, designer handbags, and rental homes in Los Angeles and Miami,” reads a press release from the U.S. Department of Justice.
By tracing the flow of funds stolen in the heist, ZachXBT concluded that Wiz received a large percentage from the theft, noting that “additional comfort [in naming him as involved] was gained as throughout multiple recordings accomplices refer to him as ‘Veer’ on audio and in chats.”
“A cluster of [cryptocurrency] addresses tied to both Box/Wiz received $41M+ from two exchanges over the past few weeks primarily flowing to luxury goods brokers to purchase cars, watches, jewelry, and designer clothes,” ZachXBT wrote.
KrebsOnSecurity sought comment from Veer Chetal, and from his parents — Radhika Chetal and Suchil Chetal. This story will be updated in the event that anyone representing the Chetal family responds. Veer Chetal has not been publicly charged with any crime.
According to a news brief published by a private Catholic high school in Danbury that Veer Chetal attended, in 2022 he successfully completed Harvard’s Future Lawyers Program, a “unique pre-professional program where students, guided by qualified Harvard undergraduate instructors, learn how to read and build a case, how to write position papers, and how to navigate a path to law school.” A November 2022 story at patch.com quoted Veer Chetal (class of 2024) crediting the Harvard program with his decision to pursue a career in law.
It remains unclear which Chetal family member acquired the 2023 Lamborghini Urus, which has a starting price of around $233,000. Sushil Chetal’s LinkedIn profile says he is a vice president at the investment bank Morgan Stanley.
It is clear that other alleged co-conspirators to the $243 million heist displayed a conspicuous consumption of wealth following the date of the heist. ZachXBT’s post chronicled Malone’s flashy lifestyle, in which he allegedly used the stolen money to purchase more than 10 vehicles, rent palatial properties, travel with friends on chartered jets, and spend between $250,000 and $500,000 a night at clubs in Los Angeles and Miami.
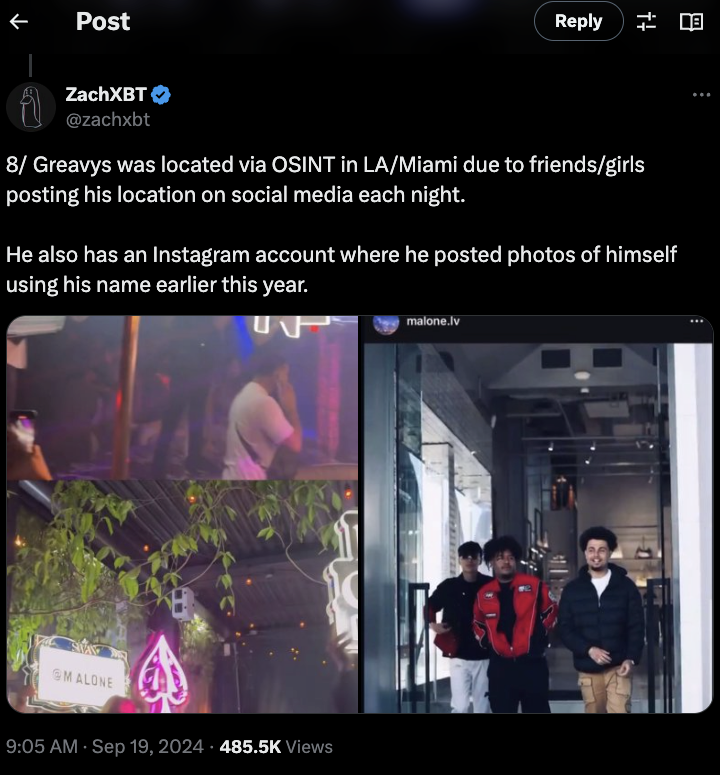
In the photo on the bottom right, Greavys/Lam is the individual on the left wearing shades. They are pictured leaving a luxury goods store. Image: x.com/zachxbt
WSVN-TV in Miami covered an FBI raid of a large rented Miami waterfront home around the time Malone and Serrano were arrested. The news station interviewed a neighbor of the home’s occupants, who reported a recent large party at the residence wherein the street was lined with high-end luxury vehicles — all of them with temporary paper tags.
ZachXBT unearthed a video showing a person identified as Wiz at a Miami nightclub earlier this year, wherein they could be seen dancing to the crowd’s chants while holding an illuminated sign with the message, “I win it all.”
It appears that all of the suspects in the cyber heist (and at least some of the alleged carjackers) are members of The Com, an archipelago of crime-focused chat communities which collectively functions as a kind of distributed cybercriminal social network that facilitates instant collaboration.
As documented in last month’s deep dive on top Com members, The Com is also a place where cybercriminals go to boast about their exploits and standing within the community, or to knock others down a peg or two. Prominent Com members are endlessly sniping over who pulled off the most impressive heists, or who has accumulated the biggest pile of stolen virtual currencies.
And as often as they extort and rob victims for financial gain, members of The Com are trying to wrest stolen money from their cybercriminal rivals — often in ways that spill over into physical violence in the real world.
One of the six Miami-area men arrested in the carjacking and extortion plot gone awry — Reynaldo “Rey” Diaz — was shot twice while parked in his bright yellow Corvette in Miami’s design district in 2022. In an interview with a local NBC television station, Diaz said he was probably targeted for the jewelry he was wearing, which he described as “pretty expensive.”
KrebsOnSecurity has learned Diaz also went by the alias “Pantic” on Telegram chat channels dedicated to stealing cryptocurrencies. Pantic was known for participating in several much smaller cyber heists in the past, and spending most of his cut on designer clothes and jewelry.
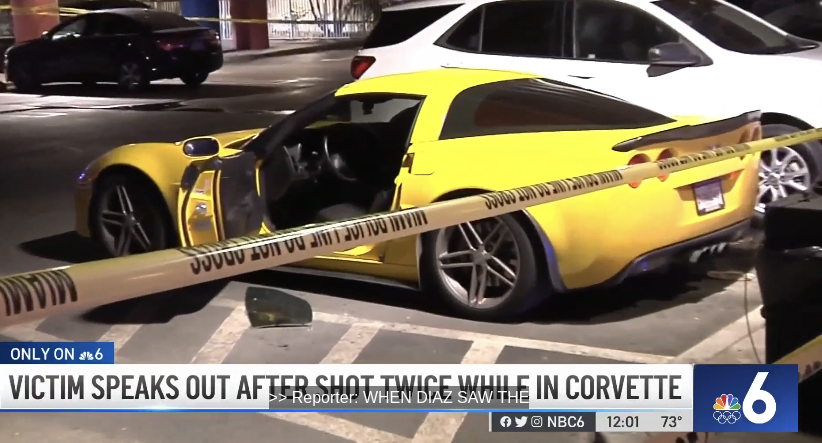
The Corvette that Diaz was sitting in when he was shot in 2022. Image: NBC 6, South Florida.
Earlier this year, Diaz was “doxed,” or publicly outed as Pantic, with his personal and family information posted on a harassment and extortion channel frequented by members of The Com. The reason cited for Pantic’s doxing was widely corroborated by multiple Com members: Pantic had inexplicably robbed two close friends at gunpoint, one of whom recently died of a drug overdose.
Government prosecutors say the brazen daylight carjacking was paid for and organized by 23-year-old Miami resident Angel “Chi Chi” Borrero. In 2022, Borrero was arrested in Miami for aggravated assault with a deadly weapon.
The six Miami men face charges including first-degree assault, kidnapping and reckless endangerment, and five of them are being held on a $1 million bond. One suspect is also charged with reckless driving, engaging police in pursuit and evading responsibility; his bond was set at $2 million. Lam and Serrano are each charged with conspiracy to commit wire fraud and conspiracy to launder money.
Cybercriminals hail from all walks of life and income levels, but some of the more accomplished cryptocurrency thieves also tend to be among the more privileged, and from relatively well-off families. In other words, these individuals aren’t stealing to put food on the table: They’re doing it so they can amass all the trappings of instant wealth, and so they can boast about their crimes to others on The Com.
There is also a penchant among this crowd to call attention to their activities in conspicuous ways that hasten their arrest and criminal charging. In many ways, the story arc of the young men allegedly involved in the $243 million heist tracks closely to that of Joel Ortiz, a valedictorian who was sentenced in 2019 to 10 years in prison for stealing more than $5 million in cryptocurrencies.
Ortiz famously posted videos of himself and co-conspirators chartering flights and partying it up at LA nightclubs, with scantily clad women waving giant placards bearing their “OG” usernames — highly-prized, single-letter social media accounts that they’d stolen or purchased stolen from others.
Ortiz earned the distinction of being the first person convicted of SIM-swapping, a crime that involves using mobile phone company insiders or compromised employee accounts to transfer a target’s phone number to a mobile device controlled by the attackers. From there, the attacker can intercept any password reset links, and any one-time passcodes sent via SMS or automated voice calls.
But as the mobile carriers seek to make their networks less hospitable to SIM-swappers, and as more financial platforms seek to harden user account security, today’s crypto thieves are finding they don’t need SIM-swaps to steal obscene amounts of cryptocurrency. Not when tricking people over the phone remains such an effective approach.
According to ZachXBT, the crooks responsible for the $243 million theft initially compromised the target’s personal accounts after calling them as Google Support and using a spoofed number. The attackers also spoofed a call from account support representatives at the cryptocurrency exchange Gemini, claiming the target’s account had been hacked.
From there the target was social engineered over the phone into resetting multi-factor authentication and sending Gemini funds to a compromised wallet. ZachXBT says the attackers also convinced the victim to use AnyDesk to share their screen, and in doing so the victim leaked their private keys.
from Krebs on Security https://ift.tt/8sHXIES
via IFTTT







