
By Lauren Hirsch and Don Clark
While Intel has struggled in recent years, other chipmakers are thriving because of a boom in demand.
Published: September 20, 2024 at 05:41PM
from NYT Technology https://ift.tt/CpKfMT6
via IFTTT


By Lauren Hirsch and Don Clark
While Intel has struggled in recent years, other chipmakers are thriving because of a boom in demand.
Published: September 20, 2024 at 05:41PM
from NYT Technology https://ift.tt/CpKfMT6
via IFTTT

By David McCabe
As the government wraps up its case, it has built a picture of how Google has become dominant among companies that buy and sell ads online.
Published: September 20, 2024 at 02:25PM
from NYT Technology https://ift.tt/T9MvuHn
via IFTTT
PAHO and Africa CDC strengthen collaboration to address access to essential medicines and vaccines
Cristina Mitchell
from PAHO/WHO | Pan American Health Organization https://ift.tt/Mgf3luP
via IFTTT
Visiting the hotel where his parents met during the Vietnam War, an engineer finds its twisting halls alive with restless memories of the past.
from New On Netflix USA https://ift.tt/h4xzuRp
via IFTTT
[Episodes Removed] Embark on a delightful journey through the culinary traditions of China and uncover the stories of the people who create and cherish its dishes.
from New On Netflix USA https://ift.tt/wvlG2Cs
via IFTTT
After years of estrangement, Khanyi Adesina returns home to fight for her family’s business empire as it threatens to collapse under corruption.
from New On Netflix USA https://ift.tt/n97Swqz
via IFTTT
Emotions run high when three estranged sisters reunite in a cramped New York City apartment to watch over their ailing father during his final days.
from New On Netflix USA https://ift.tt/HT3Uyv5
via IFTTT
An ambitious young woman launches a powerful modeling agency determined to change lives — but power and love are not for the faint of heart.
from New On Netflix USA https://ift.tt/RScFftB
via IFTTT

Hace unas horas, en la tarde/noche de ayer en el territorio español, llegó Zorin OS 17.2. No es una actualización mayor de las que cambian el primer número, pero muchos de los cambios serán de los llamativos, de los que se ven. Y es que en esta nueva versión se han mejorado apartados como la apariencia, refinando la experiencia de una de las distribuciones favoritas para los usuarios de Windows que hacen el switch.
El kernel ha pasado a ser el de Ubuntu 24.04, la última LTS que llegó en abril de 2024. Esto ha hecho que el núcleo pase a ser Linux 6.8, entre otras cosas. Además, han aprovechado el momento para actualizar las aplicaciones, como una suite de ofimática que ahora está en la serie 24.8. Lo que sigue es la lista detallada con las novedades más destacadas.
Los usuarios que ya estuvieran en Zorin OS 17 pueden actualizar desde el mismo sistema operativo. Para nuevas instalaciones, las imágenes actualizadas están disponibles aquí. Recordamos que esta distribución ofrece una opción de pago o Pro por 49.99€ y otra para la educación, además de la Core que sería la gratuita.
from Linux Adictos https://ift.tt/mUqwV7G
via IFTTT
Many GitHub users this week received a novel phishing email warning of critical security holes in their code. Those who clicked the link for details were asked to distinguish themselves from bots by pressing a combination of keyboard keys that causes Microsoft Windows to download password-stealing malware. While it’s unlikely that many programmers fell for this scam, it’s notable because less targeted versions of it are likely to be far more successful against the average Windows user.
A reader named Chris shared an email he received this week that spoofed GitHub’s security team and warned: “Hey there! We have detected a security vulnerability in your repository. Please contact us at https://github-scanner%5B.%5Dcom to get more information on how to fix this issue.”
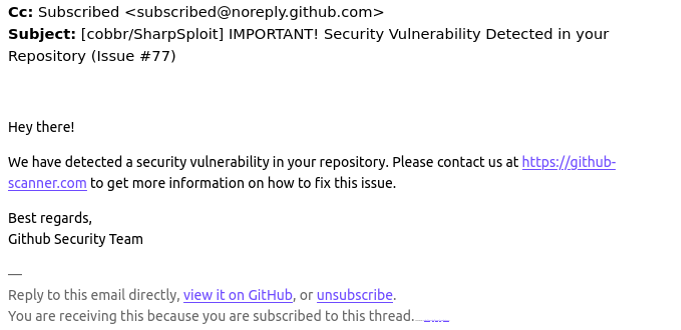
Visiting that link generates a web page that asks the visitor to “Verify You Are Human” by solving an unusual CAPTCHA.
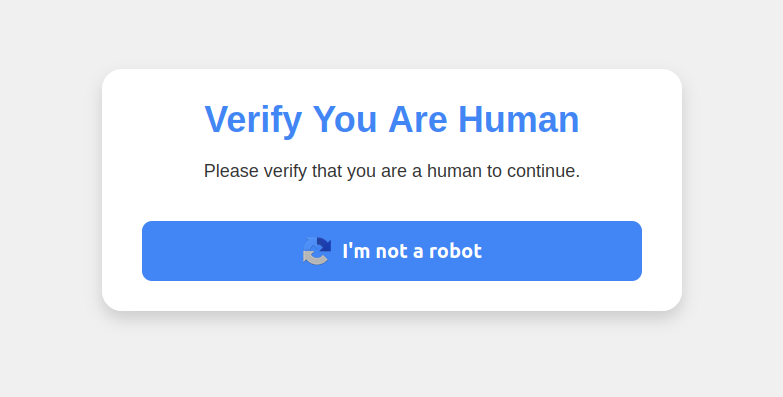
This malware attack pretends to be a CAPTCHA intended to separate humans from bots.
Clicking the “I’m not a robot” button generates a pop-up message asking the user to take three sequential steps to prove their humanity. Step 1 involves simultaneously pressing the keyboard key with the Windows icon and the letter “R,” which opens a Windows “Run” prompt that will execute any specified program that is already installed on the system.
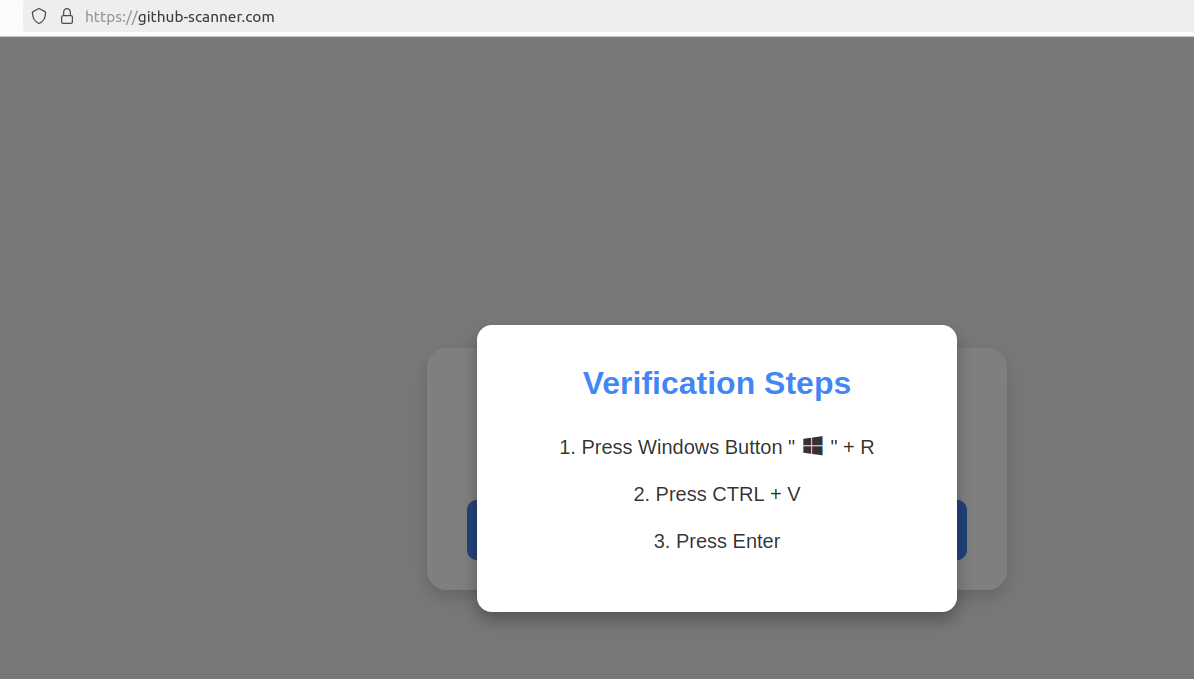
Executing this series of keypresses prompts the built-in Windows Powershell to download password-stealing malware.
Step 2 asks the user to press the “Control” key and the letter “V” at the same time, which pastes malicious code from the site’s virtual clipboard.
Step 3 — pressing the “Enter” key — causes Windows to launch a PowerShell command, and then fetch and execute a malicious file from github-scanner[.]com called “l6e.exe.”
PowerShell is a powerful, cross-platform automation tool built into Windows that is designed to make it simpler for administrators to automate tasks on a PC or across multiple computers on the same network.
According to an analysis at the malware scanning service Virustotal.com, the malicious file downloaded by the pasted text is called Lumma Stealer, and it’s designed to snarf any credentials stored on the victim’s PC.
This phishing campaign may not have fooled many programmers, who no doubt natively understand that pressing the Windows and “R” keys will open up a “Run” prompt, or that Ctrl-V will dump the contents of the clipboard.
But I bet the same approach would work just fine to trick some of my less tech-savvy friends and relatives into running malware on their PCs. I’d also bet none of these people have ever heard of PowerShell, let alone had occasion to intentionally launch a PowerShell terminal.
Given those realities, it would be nice if there were a simple way to disable or at least heavily restrict PowerShell for normal end users for whom it could become more of a liability.
However, Microsoft strongly advises against nixing PowerShell because some core system processes and tasks may not function properly without it. What’s more, doing so requires tinkering with sensitive settings in the Windows registry, which can be a dicey undertaking even for the learned.
Still, it wouldn’t hurt to share this article with the Windows users in your life who fit the less-savvy profile. Because this particular scam has a great deal of room for growth and creativity.
from Krebs on Security https://ift.tt/mD2MjSG
via IFTTT