
By Nico Grant
Wiz’s chief executive said the company walked away from a “humbling offer” and would pursue an initial public offering instead.
Published: July 22, 2024 at 06:00PM
from NYT Technology https://ift.tt/ky7KW9r
via IFTTT


By Nico Grant
Wiz’s chief executive said the company walked away from a “humbling offer” and would pursue an initial public offering instead.
Published: July 22, 2024 at 06:00PM
from NYT Technology https://ift.tt/ky7KW9r
via IFTTT
By Steve Lohr
A.I.’s math problem reflects how much the new technology is a break with computing’s past.
Published: July 22, 2024 at 06:00PM
from NYT Technology https://ift.tt/GtY5In8
via IFTTT

By Nico Grant
Google’s parent company narrowly topped revenue and profit expectations, driven by its search engine, while growth in YouTube ad sales fell short.
Published: July 23, 2024 at 02:40PM
from NYT Technology https://ift.tt/T6oVMZf
via IFTTT
The Chinese company in charge of handing out domain names ending in “.top” has been given until mid-August 2024 to show that it has put in place systems for managing phishing reports and suspending abusive domains, or else forfeit its license to sell domains. The warning comes amid the release of new findings that .top was the most common suffix in phishing websites over the past year, second only to domains ending in “.com.”

Image: Shutterstock.
On July 16, the Internet Corporation for Assigned Names and Numbers (ICANN) sent a letter to the owners of the .top domain registry. ICANN has filed hundreds of enforcement actions against domain registrars over the years, but this is thought to be the first in which ICANN has singled out a domain registry responsible for maintaining an entire top-level domain (TLD).
Among other reasons, the missive chided the registry for failing to respond to reports about phishing attacks involving .top domains.
“Based on the information and records gathered through several weeks, it was determined that .TOP Registry does not have a process in place to promptly, comprehensively, and reasonably investigate and act on reports of DNS Abuse,” the ICANN letter reads (PDF).
ICANN’s warning redacted the name of the recipient, but records show the .top registry is operated by a Chinese entity called Jiangsu Bangning Science & Technology Co. Ltd. Representatives for the company have not responded to requests for comment.
Domains ending in .top were represented prominently in a new phishing report released today by the Interisle Consulting Group, which sources phishing data from several places, including the Anti-Phishing Working Group (APWG), OpenPhish, PhishTank, and Spamhaus.
Interisle’s newest study examined nearly two million phishing attacks in the last year, and found that phishing sites accounted for more than four percent of all new .top domains between May 2023 and April 2024. Interisle said .top has roughly 2.76 million domains in its stable, and that more than 117,000 of those were phishing sites in the past year.
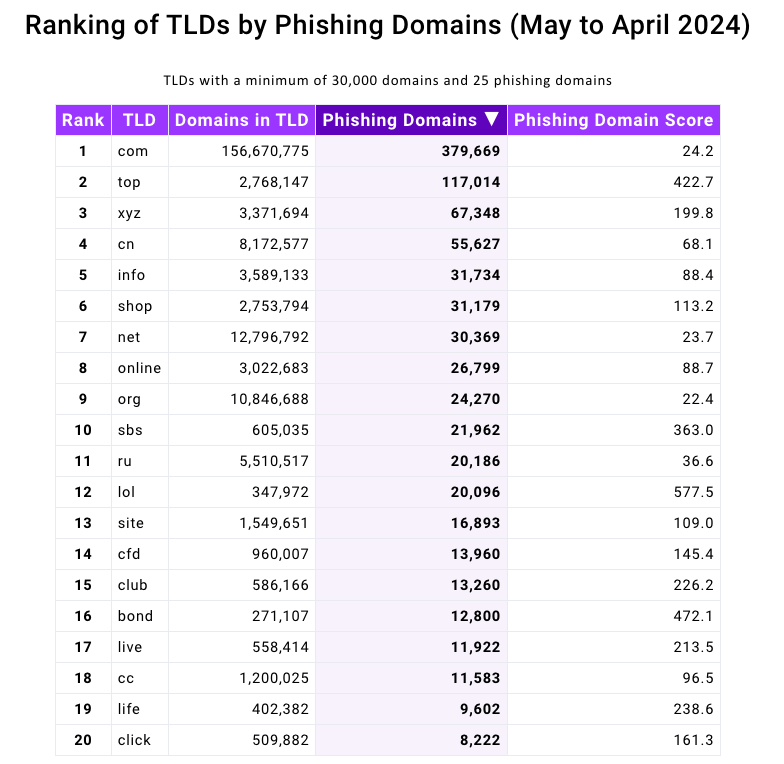
Source: Interisle Consulting Group.
ICANN said its review was based on information collected and studied about .top domains over the past few weeks. But the fact that high volumes of phishing sites are being registered through Jiangsu Bangning Science & Technology Co Ltd. is hardly a new trend.
For example, more than 10 years ago the same Chinese registrar was the fourth most common source of phishing websites, as tracked by the APWG. Bear in mind that the APWG report excerpted below was published more than a year before Jiangsu Bangning received ICANN approval to introduce and administer the new .top registry.
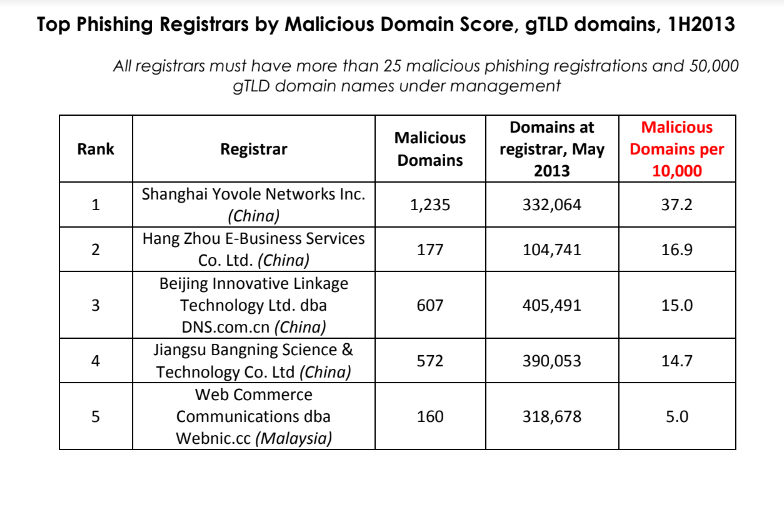
Source: APWG phishing report from 2013, two years before .top came into being.
A fascinating new wrinkle in the phishing landscape is the growth in scam pages hosted via the InterPlanetary File System (IPFS), a decentralized data storage and delivery network that is based on peer-to-peer networking. According to Interisle, the use of IPFS to host and launch phishing attacks — which can make phishing sites more difficult to take down — increased a staggering 1,300 percent, to roughly 19,000 phishing sites reported in the last year.
Last year’s report from Interisle found that domain names ending in “.us” — the top-level domain for the United States — were among the most prevalent in phishing scams. While .us domains are not even on the Top 20 list of this year’s study, “.com” maintained its perennial #1 spot as the largest source of phishing domains overall.
A year ago, the phishiest domain registrar by far was Freenom, a now-defunct registrar that handed out free domains in several country-code TLDs, including .tk, .ml, .ga and .cf. Freenom went out of business after being sued by Meta, which alleged Freenom ignored abuse complaints while monetizing traffic to abusive domains.
Following Freenom’s demise, phishers quickly migrated to other new low-cost TLDs and to services that allow anonymous, free domain registrations — particularly subdomain services. For example, Interisle found phishing attacks involving websites created on Google’s blogspot.com skyrocketed last year more than 230 percent. Other subdomain services that saw a substantial growth in domains registered by phishers include weebly.com, github.io, wix.com, and ChangeIP, the report notes.
Interisle Consulting partner Dave Piscitello said ICANN could easily send similar warning letters to at least a half-dozen other top-level domain registries, noting that spammers and phishers tend to cycle through the same TLDs periodically — including .xyz, .info, .support and .lol, all of which saw considerably more business from phishers after Freenom’s implosion.
Piscitello said domain registrars and registries could significantly reduce the number of phishing sites registered through their services just by flagging customers who try to register huge volumes of domains at once. Their study found that at least 27% of the domains used for phishing were registered in bulk — i.e. the same registrant paid for hundreds or thousands of domains in quick succession.
The report includes a case study in which a phisher this year registered 17,562 domains over the course of an eight-hour period — roughly 38 domains per minute — using .lol domains that were all composed of random letters.
ICANN tries to resolve contract disputes privately with the registry and registrar community, and experts say the nonprofit organization usually only publishes enforcement letters when the recipient is ignoring its private notices. Indeed, ICANN’s letter notes Jiangsu Bangning didn’t even open its emailed notifications. It also cited the registry for falling behind in its ICANN membership fees.
With that in mind, a review of ICANN’s public enforcement activity suggests two trends: One is that there have been far fewer public compliance and enforcement actions in recent years — even as the number of new TLDs has expanded dramatically.
The second is that in a majority of cases, the failure of a registry or registrar to pay its annual ICANN membership fees was cited as a reason for a warning letter. A review of nearly two dozen enforcement letters ICANN has sent to domain registrars since 2022 shows that failure to pay dues was cited as a reason (or the reason) for the violation at least 75 percent of the time.
Piscitello, a former ICANN board member, said nearly all breach notices sent out while he was at ICANN were because the registrar owed money.
“I think the rest is just lipstick to suggest that ICANN’s on top of DNS Abuse,” Piscitello said.
KrebsOnSecurity has sought comment from ICANN and will update this story if they respond.
from Krebs on Security https://ift.tt/QwWRuxK
via IFTTT

By Mike Isaac
The chief executive of Meta said in an open letter that it was important that the technology was not controlled by a handful of giant companies — including his own.
Published: July 23, 2024 at 09:21AM
from NYT Technology https://ift.tt/7UyORFd
via IFTTT

El navegador Chrome se diferencia de Chromium en el uso de los logotipos de Google
La historia de las cookies de terceros está lejos de acabar. Tras muchos años usándolas para recoger todo tipo de información, al menos en la Comunidad Europea se obligó a los sitios webs a informar de su uso. Más recientemente, la misma CE ha obligado a las páginas a informar claramente de su uso y a ofrecer un botón, también claro, para rechazarlas. Entre medias, Google ha estado planeando eliminar las cookies de terceros de Chrome, pero parece haber dado marcha atrás.
En un principio, Google tenía programado eliminar las cookies de terceros en 2025, pero ayer publicó una entrada en su blog en la que explica que se centrarán en la elección del usuario. Explicado de otro modo, en vez de eliminar completamente las cookies de terceros, la compañía del buscador introducirá «una nueva experiencia en Chrome» que se ha diseñado para permitir que los usuarios realicen «una elección informada» aplicable a todo el uso web que realicemos.
En 2020, Google dijo que eliminaría las cookies de terceros de Chrome en 2022, pero esa fecha se ha retrasado varias veces, en parte por las preocupaciones de los anunciantes y en parte por problemas de regulación. Recientemente lanzó una actualización en Chrome con Privacy Sandbox, lo que recogía los temas que nos interesan, las páginas web podían leer el historial y, en base a eso, ofrecer publicidad relacionada. En cualquier caso, nada de esto funcionará tan bien como las cookies de terceros.
Por otra parte, la CE y el Reino Unido no han dado el visto bueno a la eliminación de cookies de terceros por esta nueva idea de Google. El motivo, que Privacy Sandbox podría limitar la competencia en publicidad digital.
Google seguirá trabajando en Privacy Sandbox, pero en estos momentos las cookies de terceros no tienen fecha de caducidad.
Las «cookies» parecen recibir el nombre del cuento de Hansel y Gretel. En España, lo que dejan los hermanos son migas de pan, y las dejan en el suelo para poder seguir el rastro hasta casa. Las cookies de terceros van consiguiendo información para marcar algo más que un camino; saben exactamente cómo somos y nuestros intereses.
Hay cookies de terceros mejores que otras. Por ejemplo, hay un tipo que usa analíticas para recoger información. Esas son las típicas que hay en casi cualquier sitio web, y se usan para saber lo que interesa de nuestra página. Luego hay otras que relacionan sitios web o servicios. ¿Alguna vez habéis estado mirando zapatillas por la red y al entrar a Amazon habéis visto publicidad de eso mismo? Así funciona todo esto. Las cookies que, por ejemplo, recuerdan si hemos elegido un tema claro u oscuro son cookies propias, y esas no tienen nada que ver con todo esto.
El problema es que… son un problema. Se introducen en nuestro navegador, en nuestro hardware. Otro problema es encontrar una solución entre que los anunciantes puedan seguir mostrando publicidad relevante y respetar la privacidad del usuario. Es un problema tan difícil de resolver que Google no lo ha conseguido en cuatro años.
De momento, poco se sabe de la elección informada que propone Google para su Chrome. Y sin saber nada, uno sólo puede especular. Si alguien lee un texto que pone «Vamos a recoger información del uso que haces e Internet para mostrarte publicidad que te pueda interesar», la primera parte nos echará para atrás.
No sé cómo lo implementarán, pero desde mi punto de vista debe haber un incentivo para que aceptemos un mensaje parecido al anterior.
Y para el que le preocupe todo esto, hay maneras para impedir que nos radiografíen digitalmente. Por ejemplo:
Y si no, nada. A seguir con las cookies de terceros, que parece que les queda cuerda para rato.
from Linux Adictos https://ift.tt/shbkwLU
via IFTTT
[New Episodes] Culture clashes and brewing rivalries test a teen football player from South Los Angeles when he’s recruited to the Beverly Hills High School team.
from New On Netflix USA https://ift.tt/JuiAUBV
via IFTTT

By Steve Lohr
A.I.’s math problem reflects how much the new technology is a break with computing’s past.
Published: July 23, 2024 at 01:00AM
from NYT Technology https://ift.tt/GtY5In8
via IFTTT