Jimmy Carr refutes the idea that you can’t joke about anything these days with his edgy takes on gun control, religion, cancel culture and consent.
from New On Netflix USA https://ift.tt/1BcyqHJ
via IFTTT

Jimmy Carr refutes the idea that you can’t joke about anything these days with his edgy takes on gun control, religion, cancel culture and consent.
from New On Netflix USA https://ift.tt/1BcyqHJ
via IFTTT

For nearly a dozen years, residents of South Carolina have been kept in the dark by state and federal investigators over who was responsible for hacking into the state’s revenue department in 2012 and stealing tax and bank account information for 3.6 million people. The answer may no longer be a mystery: KrebsOnSecurity found compelling clues suggesting the intrusion was carried out by the same Russian hacking crew that stole of millions of payment card records from big box retailers like Home Depot and Target in the years that followed.
Questions about who stole tax and financial data on roughly three quarters of all South Carolina residents came to the fore last week at the confirmation hearing of Mark Keel, who was appointed in 2011 by Gov. Nikki Haley to head the state’s law enforcement division. If approved, this would Keel’s third six-year term in that role.
The Associated Press reports that Keel was careful not to release many details about the breach at his hearing, telling lawmakers he knows who did it but that he wasn’t ready to name anyone.
“I think the fact that we didn’t come up with a whole lot of people’s information that got breached is a testament to the work that people have done on this case,” Keel asserted.
A ten-year retrospective published in 2022 by The Post and Courier in Columbia, S.C. said investigators determined the breach began on Aug. 13, 2012, after a state IT contractor clicked a malicious link in an email. State officials said they found out about the hack from federal law enforcement on October 10, 2012.
KrebsOnSecurity examined posts across dozens of cybercrime forums around that time, and found only one instance of someone selling large volumes of tax data in the year surrounding the breach date.
On Oct. 7, 2012 — three days before South Carolina officials say they first learned of the intrusion — a notorious cybercriminal who goes by the handle “Rescator” advertised the sale of “a database of the tax department of one of the states.”
“Bank account information, SSN and all other information,” Rescator’s sales thread on the Russian-language crime forum Embargo read. “If you purchase the entire database, I will give you access to it.”
A week later, Rescator posted a similar offer on the exclusive Russian forum Mazafaka, saying he was selling information from a U.S. state tax database, without naming the state. Rescator said the data exposed included employer, name, address, phone, taxable income, tax refund amount, and bank account number.
“There is a lot of information, I am ready to sell the entire database, with access to the database, and in parts,” Rescator told Mazafaka members. “There is also information on corporate taxpayers.”
On Oct. 26, 2012, the state announced the breach publicly. State officials said they were working with investigators from the U.S. Secret Service and digital forensics experts from Mandiant, which produced an incident report (PDF) that was later published by South Carolina Dept. of Revenue. KrebsOnSecurity sought comment from the Secret Service, South Carolina prosecutors, and Mr. Keel’s office. This story will be updated if any of them respond.
On Nov. 18, 2012, Rescator told fellow denizens of the forum Verified he was selling a database of 65,000 records with bank account information from several smaller, regional financial institutions. Rescator’s sales thread on Verified listed more than a dozen database fields, including account number, name, address, phone, tax ID, date of birth, employer and occupation.
Asked to provide more context about the database for sale, Rescator told forum members the database included financial records related to tax filings of a U.S. state. Rescator added that there was a second database of around 80,000 corporations that included social security numbers, names and addresses, but no financial information.
The AP says South Carolina paid $12 million to Experian for identity theft protection and credit monitoring for its residents after the breach.
“At the time, it was one of the largest breaches in U.S. history but has since been surpassed greatly by hacks to Equifax, Yahoo, Home Depot, Target and PlayStation,” the AP’s Jeffrey Collins wrote.
As it happens, Rescator’s criminal hacking crew was directly responsible for the 2013 breach at Target and the 2014 hack of Home Depot. The Target intrusion saw Rescator’s cybercrime shops selling roughly 40 million stolen payment cards, and 56 million cards from Home Depot customers.
Who is Rescator? On Dec. 14, 2023, KrebsOnSecurity published the results of a 10-year investigation into the identity of Rescator, a.k.a. Mikhail Borisovich Shefel, a 36-year-old who lives in Moscow and who recently changed his last name to Lenin.
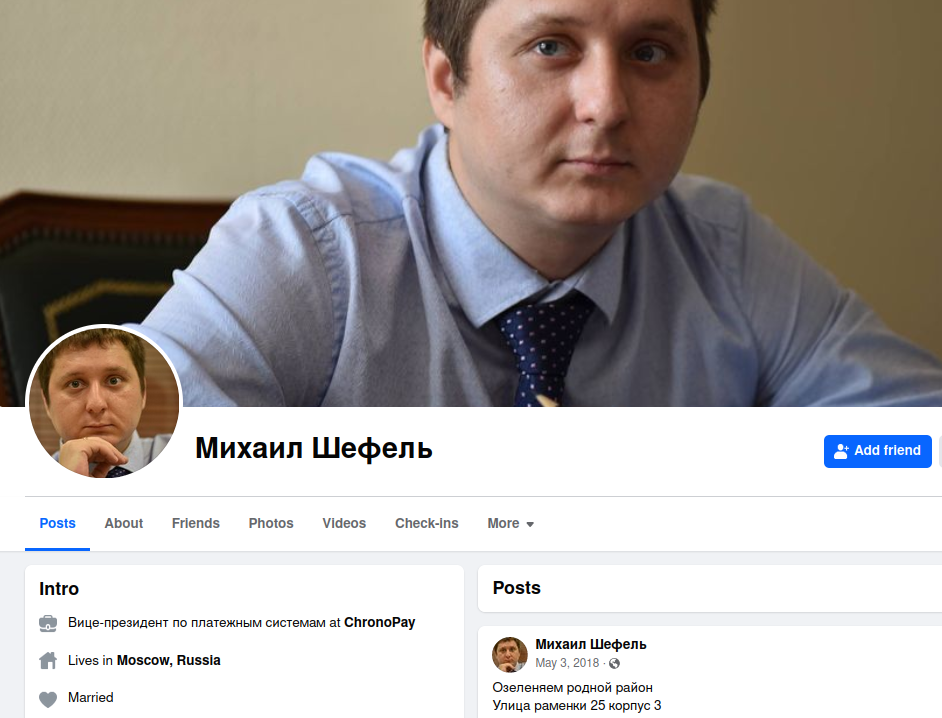
Mr. Keel’s assertion that somehow the efforts of South Carolina officials following the breach may have lessened its impact on citizens seems unlikely. The stolen tax and financial data appears to have been sold openly on cybercrime forums by one of the Russian underground’s most aggressive and successful hacking crews.
While there are no indications from reviewing forum posts that Rescator ever sold the data, his sales threads came at a time when the incidence of tax refund fraud was skyrocketing.
Tax-related identity theft occurs when someone uses a stolen identity and Social Security number (SSN) to file a tax return in that person’s name claiming a fraudulent refund. Victims usually first learn of the crime after having their returns rejected because scammers beat them to it. Even those who are not required to file a return can be victims of refund fraud, as can those who are not actually owed a refund from the U.S. Internal Revenue Service (IRS).
According to a 2013 report from the Treasury Inspector General’s office, the IRS issued nearly $4 billion in bogus tax refunds in 2012, and more than $5.8 billion in 2013. The money largely was sent to people who stole SSNs and other information on U.S. citizens, and then filed fraudulent tax returns on those individuals claiming a large refund but at a different address.
It remains unclear why Shefel has never been officially implicated in the breaches at Target, Home Depot, or in South Carolina. It may be that Shefel has been indicted, and that those indictments remain sealed for some reason. Perhaps prosecutors were hoping Shefel would decide to leave Russia, at which point it would be easier to apprehend him if he believed no one was looking for him.
But all signs are that Shefel is deeply rooted in Russia, and has no plans to leave. In January 2024, authorities in Australia, the United States and the U.K. levied financial sanctions against 33-year-old Russian man Aleksandr Ermakov for allegedly stealing data on 10 million customers of the Australian health insurance giant Medibank.
A week after those sanctions were put in place, KrebsOnSecurity published a deep dive on Ermakov, which found that he co-ran a Moscow-based IT security consulting business along with Mikhail Shefel called Shtazi-IT.
A Google-translated version of Shtazi dot ru. Image: Archive.org.
from Krebs on Security https://ift.tt/1YKriF6
via IFTTT

Hace un tiempo desde que escribí un artículo explicando la base para poder usar yt-dlp, lo que es el sucesor del famoso y ya descontinuado youtube-dl. Lo cierto es que funciona muy bien y yo ya no uso otra cosa ni aunque tengan interfaces más bonitas. Cumple con lo que espero y me tiene cubierto. Incluso lo he estado usando para ver vídeos de páginas web que no funcionan si tengo activado el bloqueo de cookies de terceros, pero hay algo mejor.
El tema sería más o menos así: voy a una página que me pide que tenga todas las cookies activadas para funcionar correctamente, leo una noticia que tiene un vídeo y ese vídeo no funciona, tiro de yt-dlp, que puede descargar los vídeos incluso de este tipo de enlaces, y cuando termina veo el vídeo y lo elimino. Como explicaba, hay algo mejor, y es usar yt-dlp en combinación con MPV, un reproductor todoterreno que es la base de otros muchos como Haruna de KDE.
El secreto está en aprenderse un comando, o crearse un script para facilitar las cosas. El comando sería así:
yt-dlp -o - "ENLACE" | mpv -
De lo anterior:
Tras presionar Intro, empezará a descargar. Veremos muchos errores y avisos, pero también el vídeo.
Como en su día con las aplicaciones web, también podemos crear un script en bash para automatizarlo, pero en este caso será mucho más corto y sencillo. Quedaría así:
#!/bin/bash echo "YTB Introduce enlace al contenido multimedia:" read enlace echo "¿Qué reproductor quieres usar?:" read reproductor yt-dlp -o - "$enlace" | $reproductor -
De lo anterior, la primera línea es sólo un nombre, luego pide la entrada de un enlace, un reproductor y finalmente lanza el comando, que de esta manera no tendremos que recordar. Para abrirlo podemos usar ./nombre-del-archivo que hayamos usado tras darle permisos de ejecución. Es un script sencillo que no gestiona errores. Debido a su sencillez, si se introduce mal enlace o reproductor mostrará un error y finalizará.
Esto puede servir también para ver cualquier vídeo de YouTube sin descargarlo, y para cualquier uso que uno pueda imaginar siempre y cuando lo que pretenda sea usar yt-dlp junto a otro reproductor compatible – VLC es compatible, pero va peor – sin descargar el contenido.
.barra {display: flex;justify-content: flex-end;height: 25px; background-color: #333;border-radius: 5px 5px 0 0;}.rojo, .naranja, .verde{width: 12px;height: 12px; position: relative;border-radius: 50%;top: 7px; margin: 0 3px;}.rojo{background-color: rgb(248, 82, 82); margin-right: 7px;}.naranja{background-color: rgb(252, 186, 63);}.verde{background-color: rgb(17, 187, 17);}.terminal{background-color: black !important; border-radius: 5px !important;}pre{font-family:monospace !important; padding: 0 10px 10px; line-height: 1.5em; overflow: auto; background-color: black !important; color: #0EE80E !important}
from Linux Adictos https://ift.tt/rAkW2jl
via IFTTT

By Paul Mozur and David E. Sanger
Microsoft plans to invest $1.5 billion in G42, an Emirati company with ties to China, as Washington and Beijing maneuver to secure tech influence in the Gulf.
Published: April 15, 2024 at 10:00PM
from NYT Technology https://ift.tt/phTU28q
via IFTTT
PAHO presents key recommendations to increase equitable access to health at G20 event in Brazil
Cristina Mitchell
from PAHO/WHO | Pan American Health Organization https://ift.tt/Bg9dJNi
via IFTTT

By Sapna Maheshwari and Mike Isaac
Instagram is testing a program that offers its top influencers the ability to interact with their followers over direct messages using a chatbot.
Published: April 15, 2024 at 10:19AM
from NYT Technology https://ift.tt/nzVf7Rg
via IFTTT

By Kevin Roose
Which A.I. system writes the best computer code or generates the most realistic image? Right now, there’s no easy way to answer those questions.
Published: April 15, 2024 at 09:14AM
from NYT Technology https://ift.tt/lb3aCqH
via IFTTT
The U.S. government is warning that smart locks securing entry to an estimated 50,000 dwellings nationwide contain hard-coded credentials that can be used to remotely open any of the locks. The lock’s maker Chirp Systems remains unresponsive, even though it was first notified about the critical weakness in March 2021. Meanwhile, Chirp’s parent company, RealPage, Inc., is being sued by multiple U.S. states for allegedly colluding with landlords to illegally raise rents.
On March 7, 2024, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) warned about a remotely exploitable vulnerability with “low attack complexity” in Chirp Systems smart locks.
“Chirp Access improperly stores credentials within its source code, potentially exposing sensitive information to unauthorized access,” CISA’s alert warned, assigning the bug a CVSS (badness) rating of 9.1 (out of a possible 10). “Chirp Systems has not responded to requests to work with CISA to mitigate this vulnerability.”
Matt Brown, the researcher CISA credits with reporting the flaw, is a senior systems development engineer at Amazon Web Services. Brown said he discovered the weakness and reported it to Chirp in March 2021, after the company that manages his apartment building started using Chirp smart locks and told everyone to install Chirp’s app to get in and out of their apartments.
“I use Android, which has a pretty simple workflow for downloading and decompiling the APK apps,” Brown told KrebsOnSecurity. “Given that I am pretty picky about what I trust on my devices, I downloaded Chirp and after decompiling, found that they were storing passwords and private key strings in a file.”
Using those hard-coded credentials, Brown found he could then connect to an application programming interface (API) that Chirp uses which is managed by smart lock vendor August.com, and use that enumerate and remotely lock or unlock any door in any building that uses the technology.
Brown said when he complained to his leasing office, they sold him a small $50 key fob that uses Near-Field Communications (NFC) to toggle the lock when he brings the fob close to his front door. But he said the fob doesn’t eliminate the ability for anyone to remotely unlock his front door using the exposed credentials and the Chirp mobile app.

A smart lock enabled with Chirp. Image: Camdenliving.com
Also, the fobs pass the credentials to his front door over the air in plain text, meaning someone could clone the fob just by bumping against him with a smartphone app made to read and write NFC tags.
Neither August nor Chirp Systems responded to requests for comment. It’s unclear exactly how many apartments and other residences are using the vulnerable Chirp locks, but multiple articles about the company from 2020 state that approximately 50,000 units use Chirp smart locks with August’s API.
Roughly a year before Brown reported the flaw to Chirp Systems, the company was bought by RealPage, a firm founded in 1998 as a developer of multifamily property management and data analytics software. In 2021, RealPage was acquired by the private equity giant Thoma Bravo.
Brown said the exposure he found in Chirp’s products is “an obvious flaw that is super easy to fix.”
“It’s just a matter of them being motivated to do it,” he said. “But they’re part of a private equity company now, so they’re not answerable to anybody. It’s too bad, because it’s not like residents of [the affected] properties have another choice. It’s either agree to use the app or move.”
In October 2022, an investigation by ProPublica examined RealPage’s dominance in the rent-setting software market, and that it found “uses a mysterious algorithm to help landlords push the highest possible rents on tenants.”
“For tenants, the system upends the practice of negotiating with apartment building staff,” ProPublic found. “RealPage discourages bargaining with renters and has even recommended that landlords in some cases accept a lower occupancy rate in order to raise rents and make more money. One of the algorithm’s developers told ProPublica that leasing agents had ‘too much empathy’ compared to computer generated pricing.”
Last year, the U.S. Department of Justice threw its weight behind a massive lawsuit filed by dozens of tenants who are accusing the $9 billion apartment software company of helping landlords collude to inflate rents.
In February 2024, attorneys general for Arizona and the District of Columbia sued RealPage, alleging RealPage’s software helped create a rental monopoly in their states.
from Krebs on Security https://ift.tt/t4b2C86
via IFTTT
Whether you’re pushing your kid down the street or running on a trail, we have a stroller for you.
from Gear Latest https://ift.tt/8B190r2
via IFTTT
Whether you’re into esports or casual fragging, these are the greatest gaming mice we’ve tested.
from Gear Latest https://ift.tt/tApHOP5
via IFTTT