A teenager struggles in the face of societal inequities. But with support from her inner circle, her talent for engineering could open a path forward.
from New On Netflix USA https://ift.tt/6MPV3n5
via IFTTT

A teenager struggles in the face of societal inequities. But with support from her inner circle, her talent for engineering could open a path forward.
from New On Netflix USA https://ift.tt/6MPV3n5
via IFTTT
An unemployed construction worker goes to work for the real estate developer who evicted him, but his new position entails evicting other homeowners.
from New On Netflix USA https://ift.tt/q2vMoLH
via IFTTT

El artículo sobre el lanzamiento de WINE 8.21 empezó con la frase «Todos queremos a Wayland». Era una manera de expresar que es hacia donde se dirigen todos los proyectos y, a la postre, los usuarios. Pero lo cierto es que no todos quieren a Wayland. Aunque funcione bien en muchos escenarios, hay otros en los que trabaja algo peor, y de esto se han quejado los desarrolladores de PCSX2.
PCSX2 nos permite jugar a nuestras ISOs de juegos de PlayStation 2, y la verdad es que, gracias a sus muchos ajustes disponibles, sorprende lo bien que puede funcionar en un ordenador del montón, de la parte baja. Sus desarrolladores desactivaron el soporte por defecto para Wayland, y a finales de octubre publicaron información sobre esta decisión. Lo que puede pillar a muchos desprevenidos es que parte del enfado del proyecto tiene un culpable: GNOME.
GNOME empezó a usar Wayland por defecto en 2017, pero tardó un poco más en ser implementado por las distribuciones Linux. Por ejemplo, Ubuntu lo usó también con gráficas de NVIDIA en abril de 2022, y KDE empezará a usarlo por defecto en febrero de 2024. Hay años de diferencia entre el movimiento de un escritorio al del otro, pero de quien más se quejan los desarrolladores de PCSX2 es de GNOME.
En la descripción del cambio, lo primero que leemos es que «desactiva Wayland, que está super roto/con bugs en básicamente cualquier escenario. KDE no es tan buggy, GNOME es un completo desastre«. Entrando en los detalles, explican que la estúpida obsesión con el CSD en GNOME crea inconsistencia; la imposibilidad de posicionar ventanas hace que guardar la posición de las ventanas no sea posible; problemas con NVIDIA y algunos puntos más.
Hasta que se pongan las pilas, lo cual es poco probable, ya que se ha avanzado muy poco en la última década, mantenlo desactivado. Para los Flatpaks, los usuarios pueden volver a activarlo con flatseal si realmente quieren la experiencia de mierda.
NOTA: La traducción original no dice lo de las pilas. Usan la palabra «shit» (mierda), que aunque sea malsonante y esté con asteriscos, también se puede traducir como «cosas».
Esto no es un ataque sin cuartel contra Wayland ni GNOME. Sólo prefieren que las cosas mejoren, y el soporte sigue estando disponible, aunque hay que hacer el cambio manualmente. Entre las soluciones, proponen usar la versión flatpak y reactivar Wayland con Flatseal «si de verdad quieren la experiencia de mierda» o usar el runtime de KDE/Qt 6.6, entre otras cosas.
Yo soy un desarrollador de juguete, júnior, en pañales, y sé lo que puede costar adaptarse a lo nuevo cuando un software ya funciona. El cambio a Wayland es una tarea difícil, titánica desde mi punto de vista, y creo que los desarrolladores de PCSX2 tienen parte de razón.
Las distribuciones también tienen su parte de razón: hay que presionar para el cambio, o de lo contrario no tendrá lugar nunca. Por las palabras del comunicado, parece innegable que sobre todo GNOME tiene que ponerse las pilas, pero los de PCSX2 tienen que poner su granito de arena.
Yo he probado PCSX2 en KDE + Wayland y no he visto NINGÚN fallo, por lo menos en la AppImage (prefiero no compilar un programa como ese con tantas dependencias). Sí he visto fallos en otro emulador, el de PSP (PPSSPP) en el que bajo Wayland… pues eso, es una experiencia «crappy».
Así que, al final, creo que lo mejor va a ser que las diferentes distribuciones sigan permitiendo elegir entre X11 y Wayland como hasta ahora durante mucho más tiempo, y los usuarios debemos saber que existe esa posibilidad para, por ejemplo, entrar a X11 si queremos disfrutar de la mejor experiencia con PCSX2. Con el resto del software tocará cruzar los dedos y rezar para que nada nos deje colgados en el momento más inoportuno. Ahora que todos los escritorios quieren pasarse a Wayland, y que no está perfecto al 100%, es lo que toca. Eso o usar X11 siempre hasta que ya no sea una posibilidad.
from Linux Adictos https://ift.tt/LzxR7Am
via IFTTT

By Victor Mather
The company says it will start purging accounts, including services like Gmail and YouTube, that have been idle for two years or more.
Published: November 28, 2023 at 12:55PM
from NYT Technology https://ift.tt/siLAlot
via IFTTT

By Karen Weise
Amazon has been racing to shake off the perception that it is lagging in the push to take advantage of artificial intelligence.
Published: November 28, 2023 at 11:34AM
from NYT Technology https://ift.tt/4FUkA15
via IFTTT
The sale extravaganza may be over, but many of the same discounts are alive, including deals on office chairs and TCL TVs.
from Gear Latest https://ift.tt/e8vaTGq
via IFTTT
One of the cybercrime underground’s more active sellers of Social Security numbers, background and credit reports has been pulling data from hacked accounts at the U.S. consumer data broker USinfoSearch, KrebsOnSecurity has learned.
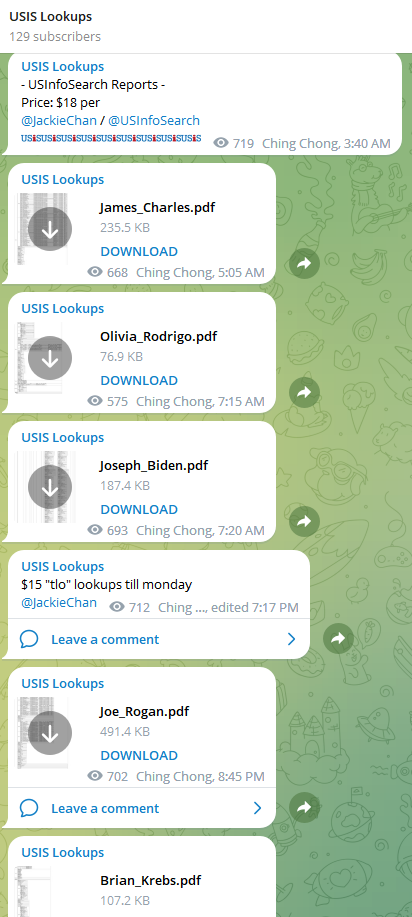 Since at least February 2023, a service advertised on Telegram called USiSLookups has operated an automated bot that allows anyone to look up the SSN or background report on virtually any American. For prices ranging from $8 to $40 and payable via virtual currency, the bot will return detailed consumer background reports automatically in just a few moments.
Since at least February 2023, a service advertised on Telegram called USiSLookups has operated an automated bot that allows anyone to look up the SSN or background report on virtually any American. For prices ranging from $8 to $40 and payable via virtual currency, the bot will return detailed consumer background reports automatically in just a few moments.
USiSLookups is the project of a cybercriminal who uses the nicknames JackieChan/USInfoSearch, and the Telegram channel for this service includes a small number of sample background reports, including that of President Joe Biden, and podcaster Joe Rogan. The data in those reports includes the subject’s date of birth, address, previous addresses, previous phone numbers and employers, known relatives and associates, and driver’s license information.
JackieChan’s service abuses the name and trademarks of Columbus, OH based data broker USinfoSearch, whose website says it provides “identity and background information to assist with risk management, fraud prevention, identity and age verification, skip tracing, and more.”
“We specialize in non-FCRA data from numerous proprietary sources to deliver the information you need, when you need it,” the company’s website explains. “Our services include API-based access for those integrating data into their product or application, as well as bulk and batch processing of records to suit every client.”
As luck would have it, my report was also listed in the Telegram channel for this identity fraud service, presumably as a teaser for would-be customers. On October 19, 2023, KrebsOnSecurity shared a copy of this file with the real USinfoSearch, along with a request for information about the provenance of the data.
USinfoSearch said it would investigate the report, which appears to have been obtained on or before June 30, 2023. On Nov. 9, 2023, Scott Hostettler, general manager of USinfoSearch parent Martin Data LLC shared a written statement about their investigation that suggested the ID theft service was trying to pass off someone else’s consumer data as coming from USinfoSearch:
Regarding the Telegram incident, we understand the importance of protecting sensitive information and upholding the trust of our users is our top priority. Any allegation that we have provided data to criminals is in direct opposition to our fundamental principles and the protective measures we have established and continually monitor to prevent any unauthorized disclosure. Because Martin Data has a reputation for high-quality data, thieves may steal data from other sources and then disguise it as ours. While we implement appropriate safeguards to guarantee that our data is only accessible by those who are legally permitted, unauthorized parties will continue to try to access our data. Thankfully, the requirements needed to pass our credentialing process is tough even for established honest companies.
USinfoSearch’s statement did not address any questions put to the company, such as whether it requires multi-factor authentication for customer accounts, or whether my report had actually come from USinfoSearch’s systems.
After much badgering, on Nov. 21 Hostettler acknowledged that the USinfoSearch identity fraud service on Telegram was in fact pulling data from an account belonging to a vetted USinfoSearch client.
“I do know 100% that my company did not give access to the group who created the bots, but they did gain access to a client,” Hostettler said of the Telegram-based identity fraud service. “I apologize for any inconvenience this has caused.”
Hostettler said USinfoSearch heavily vets any new potential clients, and that all users are required to undergo a background check and provide certain documents. Even so, he said, several fraudsters each month present themselves as credible business owners or C-level executives during the credentialing process, completing the application and providing the necessary documentation to open a new account.
“The level of skill and craftsmanship demonstrated in the creation of these supporting documents is incredible,” Hostettler said. “The numerous licenses provided appear to be exact replicas of the original document. Fortunately, I’ve discovered several methods of verification that do not rely solely on those documents to catch the fraudsters.”
“These people are unrelenting, and they act without regard for the consequences,” Hostettler continued. “After I deny their access, they will contact us again within the week using the same credentials. In the past, I’ve notified both the individual whose identity is being used fraudulently and the local police. Both are hesitant to act because nothing can be done to the offender if they are not apprehended. That is where most attention is needed.”
JackieChan is most active on Telegram channels focused on “SIM swapping,” which involves bribing or tricking mobile phone company employees into redirecting a target’s phone number to a device the attackers control. SIM swapping allows crooks to temporarily intercept the target’s text messages and phone calls, including any links or one-time codes for authentication that are delivered via SMS.
Reached on Telegram, JackieChan said most of his clients hail from the criminal SIM swapping world, and that the bulk of his customers use his service via an application programming interface (API) that allows customers to integrate the lookup service with other web-based services, databases, or applications.
“Sim channels is where I get most of my customers,” JackieChan told KrebsOnSecurity. “I’m averaging around 100 lookups per day on the [Telegram] bot, and around 400 per day on the API.”
JackieChan claims his USinfoSearch bot on Telegram abuses stolen credentials needed to access an API used by the real USinfoSearch, and that his service was powered by USinfoSearch account credentials that were stolen by malicious software tied to a botnet that he claims to have operated for some time.
This is not the first time USinfoSearch has had trouble with identity thieves masquerading as legitimate customers. In 2013, KrebsOnSecurity broke the news that an identity fraud service in the underground called “SuperGet[.]info” was reselling access to personal and financial data on more than 200 million Americans that was obtained via the big-three credit bureau Experian.
The consumer data resold by Superget was not obtained directly from Experian, but rather via USinfoSearch. At the time, USinfoSearch had a contractual agreement with a California company named Court Ventures, whereby customers of Court Ventures had access to the USinfoSearch data, and vice versa.
When Court Ventures was purchased by Experian in 2012, the proprietor of SuperGet — a Vietnamese hacker named Hieu Minh Ngo who had impersonated an American private investigator — was grandfathered in as a client. The U.S. Secret Service agent who oversaw Ngo’s capture, extradition, prosecution and rehabilitation told KrebsOnSecurity he’s unaware of any other cybercriminal who has caused more material financial harm to more Americans than Ngo.
JackieChan also sells access to hacked email accounts belonging to law enforcement personnel in the United States and abroad. Hacked police department emails can come in handy for ID thieves trying to pose as law enforcement officials who wish to purchase consumer data from platforms like USinfoSearch. Hence, Mr. Hostettler’s ongoing battle with fraudsters seeking access to his company’s service.
These police credentials are mainly marketed to criminals seeking fraudulent “Emergency Data Requests,” wherein crooks use compromised government and police department email accounts to rapidly obtain customer account data from mobile providers, ISPs and social media companies.
Normally, these companies will require law enforcement officials to supply a subpoena before turning over customer or user records. But EDRs allow police to bypass that process by attesting that the information sought is related to an urgent matter of life and death, such as an impending suicide or terrorist attack.

In response to an alarming increase in the volume of fraudulent EDRs, many service providers have chosen to require all EDRs be processed through a service called Kodex, which seeks to filter EDRs based on the reputation of the law enforcement entity requesting the information, and other attributes of the requestor.
For example, if you want to send an EDR to Coinbase or Twilio, you’ll first need to have valid law enforcement credentials and create an account at the Kodex online portal at these companies. However, Kodex may still throttle or block any requests from any accounts if they set off certain red flags.
Within their own separate Kodex portals, Twilio can’t see requests submitted to Coinbase, or vice versa. But each can see if a law enforcement entity or individual tied to one of their own requests has ever submitted a request to a different Kodex client, and then drill down further into other data about the submitter, such as Internet address(es) used, and the age of the requestor’s email address.
In August, JackieChan was advertising a working Kodex account for sale on the cybercrime channels, including redacted screenshots of the Kodex account dashboard as proof of access.
Kodex co-founder Matt Donahue told KrebsOnSecurity his company immediately detected that the law enforcement email address used to create the Kodex account pictured in JackieChan’s ad was likely stolen from a police officer in India. One big tipoff, Donahue said, was that the person creating the account did so using an Internet address in Brazil.
“There’s a lot of friction we can put in the way for illegitimate actors,” Donahue said. “We don’t let people use VPNs. In this case we let them in to honeypot them, and that’s how they got that screenshot. But nothing was allowed to be transmitted out from that account.”
Massive amounts of data about you and your personal history are available from USinfoSearch and dozens of other data brokers that acquire and sell “non-FCRA” data — i.e., consumer data that cannot be used for the purposes of determining one’s eligibility for credit, insurance, or employment.
Anyone who works in or adjacent to law enforcement is eligible to apply for access to these data brokers, which often market themselves to police departments and to “skip tracers,” essentially bounty hunters hired to locate others in real life — often on behalf of debt collectors, process servers or a bail bondsman.
There are tens of thousands of police jurisdictions around the world — including roughly 18,000 in the United States alone. And the harsh reality is that all it takes for hackers to apply for access to data brokers (and abuse the EDR process) is illicit access to a single police email account.
The trouble is, compromised credentials to law enforcement email accounts show up for sale with alarming frequency on the Telegram channels where JackieChan and their many clients reside. Indeed, Donahue said Kodex so far this year has identified attempted fake EDRs coming from compromised email accounts for police departments in India, Italy, Thailand and Turkey.
from Krebs on Security https://ift.tt/yGKwQzN
via IFTTT
Obsidian is an incredible writing and note-taking tool. Here’s why this cloud-less, offline app helps me stay organized and keep the ideas flowing.
from Gear Latest https://ift.tt/svtxgdp
via IFTTT
[Streaming Again] Looking to start anew, a widow retreats with her children to her aunt’s goat farm, where the ranch’s manager helps her navigate country life and loss.
from New On Netflix USA https://ift.tt/N6RnZPI
via IFTTT
Twenty of Korea’s hottest comedians come together to fiercely compete for a chance to host a Netflix show — delivering nonstop, zany laughter.
from New On Netflix USA https://ift.tt/DUipkqw
via IFTTT