A once-respected surgeon who’s lost his family and his memory gets a chance at redemption when he reconnects with someone from his forgotten past.
from New On Netflix USA https://ift.tt/V69Dmor
via IFTTT

A once-respected surgeon who’s lost his family and his memory gets a chance at redemption when he reconnects with someone from his forgotten past.
from New On Netflix USA https://ift.tt/V69Dmor
via IFTTT
From Wes Anderson comes an adaptation of Roald Dahl’s beloved story about a rich man who sets out to master an extraordinary skill to cheat at gambling.
from New On Netflix USA https://ift.tt/ldnO9CX
via IFTTT
The victim shaming site operated by the Snatch ransomware group is leaking data about its true online location and internal operations, as well as the Internet addresses of its visitors, KrebsOnSecurity has found. The leaked data suggest that Snatch is one of several ransomware groups using paid ads on Google.com to trick people into installing malware disguised as popular free software, such as Microsoft Teams, Adobe Reader, Mozilla Thunderbird, and Discord.
First spotted in 2018, the Snatch ransomware group has published data stolen from hundreds of organizations that refused to pay a ransom demand. Snatch publishes its stolen data at a website on the open Internet, and that content is mirrored on the Snatch team’s darknet site, which is only reachable using the global anonymity network Tor.
KrebsOnSecurity has learned that Snatch’s darknet site exposes its “server status” page, which includes information about the true Internet addresses of users accessing the website.
Refreshing this page every few seconds shows that the Snatch darknet site generates a decent amount of traffic, often attracting thousands of visitors each day. But by far the most frequent repeat visitors are coming from Internet addresses in Russia that either currently host Snatch’s clear web domain names or recently did.
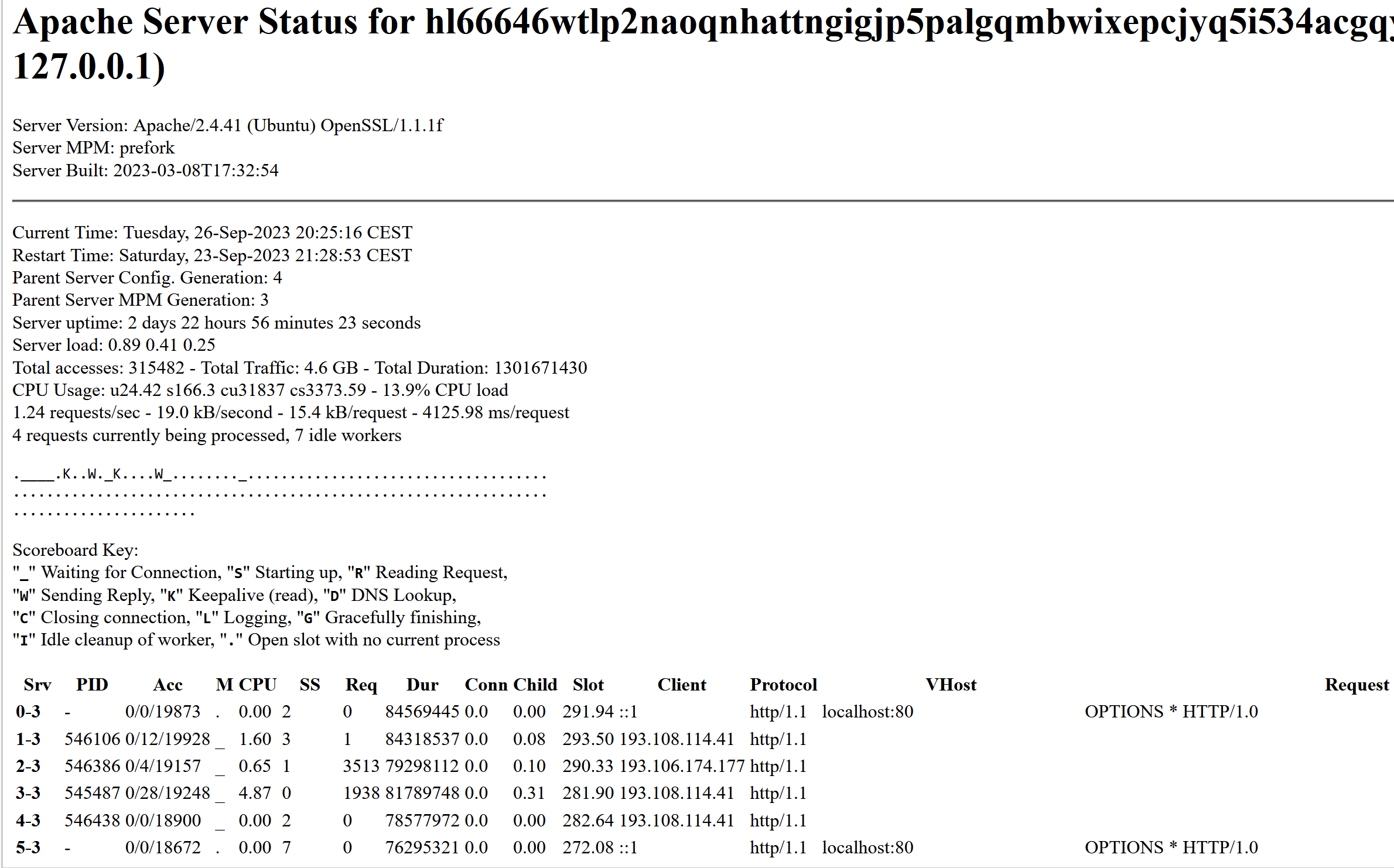
The Snatch ransomware gang’s victim shaming site on the darknet is leaking data about its visitors. This “server status” page says that Snatch’s website is on Central European Summer Time (CEST) and is powered by OpenSSL/1.1.1f, which is no longer supported by security updates.
Probably the most active Internet address accessing Snatch’s darknet site is 193.108.114[.]41, which is a server in Yekaterinburg, Russia that hosts several Snatch domains, including snatchteam[.]top, sntech2ch[.]top, dwhyj2[.]top and sn76930193ch[.]top. It could well be that this Internet address is showing up frequently because Snatch’s clear-web site features a toggle button at the top that lets visitors switch over to accessing the site via Tor.
Another Internet address that showed up frequently in the Snatch server status page was 194.168.175[.]226, currently assigned to Matrix Telekom in Russia. According to DomainTools.com, this address also hosts or else recently hosted the usual coterie of Snatch domains, as well as quite a few domains phishing known brands such as Amazon and Cashapp.
The Moscow Internet address 80.66.64[.]15 accessed the Snatch darknet site all day long, and that address also housed the appropriate Snatch clear-web domains. More interestingly, that address is home to multiple recent domains that appear confusingly similar to known software companies, including libreoff1ce[.]com and www-discord[.]com.
This is interesting because the phishing domains associated with the Snatch ransomware gang were all registered to the same Russian name — Mihail Kolesnikov, a name that is somewhat synonymous with recent phishing domains tied to malicious Google ads.
Kolesnikov could be a nod to a Russian general made famous during Boris Yeltsin’s reign. Either way, it’s clearly a pseudonym, but there are some other commonalities among these domains that may provide insight into how Snatch and other ransomware groups are sourcing their victims.
DomainTools says there are more than 1,300 current and former domain names registered to Mihail Kolesnikov between 2013 and July 2023. About half of the domains appear to be older websites advertising female escort services in major cities around the United States (e.g. the now-defunct pittsburghcitygirls[.]com).
The other half of the Kolesnikov websites are far more recent phishing domains mostly ending in “.top” and “.app” that appear designed to mimic the domains of major software companies, including www-citrix[.]top, www-microsofteams[.]top, www-fortinet[.]top, ibreoffice[.]top, www-docker[.]top, www-basecamp[.]top, ccleaner-cdn[.]top, adobeusa[.]top, and http://www.real-vnc[.]top.
In August 2023, researchers with Trustwave Spiderlabs said they encountered domains registered to Mihail Kolesnikov being used to disseminate the Rilide information stealer trojan.
But it appears multiple crime groups may be using these domains to phish people and disseminate all kinds of information-stealing malware. In February 2023, Spamhaus warned of a huge surge in malicious ads that were hijacking search results in Google.com, and being used to distribute at least five different families of information stealing trojans, including AuroraStealer, IcedID/Bokbot, Meta Stealer, RedLine Stealer and Vidar.
For example, Spamhaus said victims of these malicious ads would search for Microsoft Teams in Google.com, and the search engine would often return a paid ad spoofing Microsoft or Microsoft Teams as the first result — above all other results. The malicious ad would include a logo for Microsoft and at first glance appear to be a safe and trusted place to download the Microsoft Teams client.
However, anyone who clicked on the result was whisked away instead to mlcrosofteams-us[.]top — yet another malicious domain registered to Mr. Kolesnikov. And while visitors to this website may believe they are only downloading the Microsoft Teams client, the installer file includes a copy of the IcedID malware, which is really good at stealing passwords and authentication tokens from the victim’s web browser.
The founder of the Swiss anti-abuse website abuse.ch told Spamhaus it is likely that some cybercriminals have started to sell “malvertising as a service” on the dark web, and that there is a great deal of demand for this service.
In other words, someone appears to have built a very profitable business churning out and promoting new software-themed phishing domains and selling that as a service to other cybercriminals. Or perhaps they are simply selling any stolen data (and any corporate access) to active and hungry ransomware group affiliates.
The tip about the exposed “server status” page on the Snatch darkweb site came from @htmalgae, the same security researcher who alerted KrebsOnSecurity earlier this month that the darknet victim shaming site run by the 8Base ransomware gang was inadvertently left in development mode.
That oversight revealed not only the true Internet address of the hidden 8Base site (in Russia, naturally), but also the identity of a programmer in Moldova who apparently helped to develop the 8Base code.
@htmalgae said the idea of a ransomware group’s victim shaming site leaking data that they did not intend to expose is deliciously ironic.
“This is a criminal group that shames others for not protecting user data,” @htmalgae said. “And here they are leaking their user data.”
All of the malware mentioned in this story is designed to run on Microsoft Windows devices. But Malwarebytes recently covered the emergence of a Mac-based information stealer trojan called AtomicStealer that was being advertised through malicious Google ads and domains that were confusingly similar to software brands.
Please be extra careful when you are searching online for popular software titles. Cracked, pirated copies of major software titles are a frequent source of infostealer infections, as are these rogue ads masquerading as search results. Make sure to double-check you are actually at the domain you believe you’re visiting *before* you download and install anything.
Stay tuned for Part II of this post, which includes a closer look at the Snatch ransomware group and their founder.
Further reading:
@HTMalgae’s list of the top Internet addresses seen accessing Snatch’s darknet site
Ars Technica: Until Further Notice Think Twice Before Using Google to Download Software
Bleeping Computer: Hackers Abuse Google Ads to Spread Malware in Legit Software
from Krebs on Security https://ift.tt/qXU93jR
via IFTTT
 El pasado 20 de septiembre llegó GNOME 45 con novedades como un nuevo indicador en Actividades entre sus novedades más destacadas. Lo próximo será GNOME 46, una versión de la que todavía no hay capturas por el mero hecho de que ni siquiera he empezado a desarrollarse. Lo que sí se ha publicado ya es su calendario, su hoja de ruta, por lo que ya sabemos qué pasará y cuándo.
El pasado 20 de septiembre llegó GNOME 45 con novedades como un nuevo indicador en Actividades entre sus novedades más destacadas. Lo próximo será GNOME 46, una versión de la que todavía no hay capturas por el mero hecho de que ni siquiera he empezado a desarrollarse. Lo que sí se ha publicado ya es su calendario, su hoja de ruta, por lo que ya sabemos qué pasará y cuándo.
No hay ninguna sorpresa sobre cuándo llegará la versión estable: en marzo de 2024. GNOME se pone de acuerdo con Fedora y Ubuntu y lanza dos versiones al año sobre un mes antes del lanzamiento de una nueva entrega de los dos sistemas operativos más populares en usar GNOME, de manera que éstos, salvo decisión propia, siempre usarán lo último. La fecha exacta será el miércoles 20 de marzo.
(adsbygoogle = window.adsbygoogle || []).push({});
El desarrollo de GNOME 46 empezará pronto, y se podrá probar en versión alfa ya en enero:
La mejor manera de probar todas las novedades es con GNOME OS Nightly. Es un pseudo-sistema operativo de GNOME que incluye mucho del proyecto, y se puede probar en nativo o en una máquina virtual. Para los que prefieran hacerlo en VM, se recomienda usar la versión flatpak de GNOME Boxes, hasta el punto de que no funciona en la versión de repositorios oficiales ni en ningún otro software de virtualización. Esto último es algo que no he podido comprobar, ya que hace mucho que me acostumbré a GNOME Boxes y no he probado GNOME OS en VirtualBox, ni mucho menos en el Hyper-V de Windows.
Sobre las novedades que traerá, en nuestro blog hermano Ubunlog, y aprovecho aquí para darle la bienvenida a mi compañero Diego, publicamos semanalmente artículos sobre todo lo relacionado a GNOME.
(adsbygoogle = window.adsbygoogle || []).push({});
from Linux Adictos https://ift.tt/Ilnb8GM
via IFTTT

The Docuent Foundation suele lanzar las nuevas versiones de su suite de ofimática los jueves, o por lo menos las más nuevas. Que nos entreguen algo en un día diferente y para las ramas que se conocen como «fresh» (la más nueva) y «still» (la que tiene más correcciones) no suelen ser buenas noticias, y ayer martes, menos de dos semanas después de 7.6.1, lanzaron LibreOffice 7.6.2 y 7.5.7 para corregir un fallo de seguridad que han considerado lo suficientemente grave como para adelantar sus planes.
El fallo de seguridad que han tenido que atajar ha sido el CVE-2023-4863, cuya descripción explica que «El desbordamiento del búfer de montón en WebP en Google Chrome anterior a 116.0.5845.187 permitía a un atacante remoto realizar una escritura en memoria fuera de los límites a través de una página HTML manipulada«. En el enlace anterior se menciona Chromium, pero el problema está en la librería libwebp que se usa en otro mucho software.
(adsbygoogle = window.adsbygoogle || []).push({});
LibreOffice 7.6.2 y 7.5.7 también corrigen otros bugs y regresiones y todos los parches ya están disponibles. The Document Foundation anima a todos los usuarios de LibreOffice a que actualicemos lo más pronto posible.
La lista completa de cambios está recogida en las publicaciones de LibreOffice 7.6.2 RC1 y 7.5.7 RC1., con 54 y 14 bugs respectivamente. No hay nada sobre las RC2 porque, como ya se ha explicado, han tenido que adelantar los lanzamientos para corregir el fallo que se considera de prioridad alta.
Las dos nuevas versiones ya están disponibles para descargar desde su página web oficial. Desde allí, los usuarios de Linux podemos descargar paquetes DEB y RPM, pero también está ya en Flathub. El paquete snap, esos que Canonical aseguraban que se actualizarían tan pronto y que nos beneficiaríamos sobre todo por temas de seguridad, sigue en 7.6.1. A los repositorios de las diferentes distribuciones Linux debería llegar en las próximas horas.
(adsbygoogle = window.adsbygoogle || []).push({});
from Linux Adictos https://ift.tt/vXxj4n6
via IFTTT

By David Streitfeld
The chair of the Federal Trade Commission wants to disrupt Amazon, whose founder built a trillion-dollar firm by disrupting retail.
Published: September 27, 2023 at 03:00AM
from NYT Technology https://ift.tt/jopGf42
via IFTTT

By David Streitfeld
The chair of the Federal Trade Commission wants to disrupt Amazon, whose founder built a trillion-dollar firm by disrupting retail.
Published: September 27, 2023 at 03:00AM
from NYT Technology https://ift.tt/M3SLu0o
via IFTTT