Open source code continues its steady takeover of codebases, and organizations have made slight gains in eliminating out-of-date and vulnerable components.
from Dark Reading https://ift.tt/YczZ73U
via IFTTT

Open source code continues its steady takeover of codebases, and organizations have made slight gains in eliminating out-of-date and vulnerable components.
from Dark Reading https://ift.tt/YczZ73U
via IFTTT
The U.S. Department of Justice (DOJ) said today it seized the website and user database for RaidForums, an extremely popular English-language cybercrime forum that sold access to more than 10 billion consumer records stolen in some of the world’s largest data breaches since 2015. The DOJ also charged the alleged administrator of RaidForums — 21-year-old Diogo Santos Coelho, of Portugal — with six criminal counts, including conspiracy, access device fraud and aggravated identity theft.
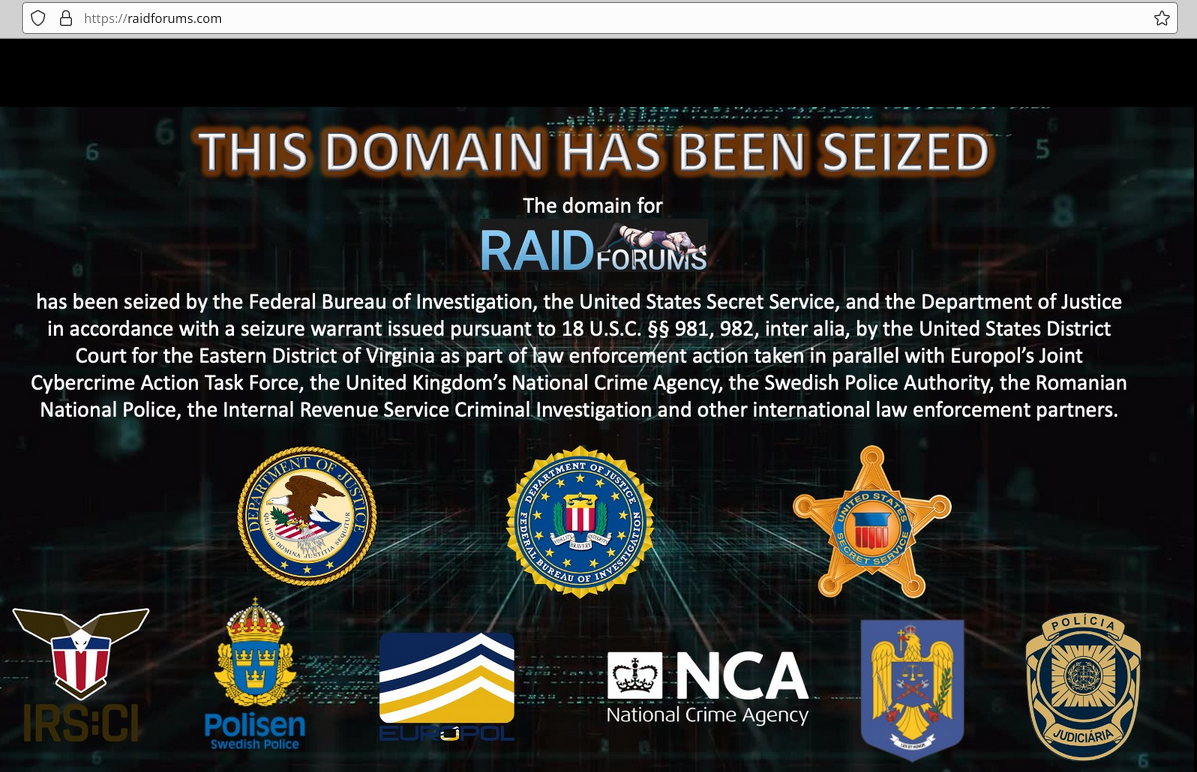
The “raid” in RaidForums is a nod to the community’s humble beginnings in 2015, when it was primarily an online venue for organizing and supporting various forms of electronic harassment. According to the DOJ, that early activity included ‘raiding‘ — posting or sending an overwhelming volume of contact to a victim’s online communications medium — and ‘swatting,’ the practice of making false reports to public safety agencies of situations that would necessitate a significant, and immediate armed law enforcement response.”
But over the years as trading in hacked databases became big business, RaidForums emerged as the go-to place for English-speaking hackers to peddle their wares. Perhaps the most bustling marketplace within RaidForums was its “Leaks Market,” which described itself as a place to buy, sell, and trade hacked databases and leaks.
The government alleges Coelho and his forum administrator identity “Omnipotent” profited from the illicit activity on the platform by charging “escalating prices for membership tiers that offered greater access and features, including a top-tier ‘God’ membership status.”
“RaidForums also sold ‘credits’ that provided members access to privileged areas of the website and enabled members to ‘unlock’ and download stolen financial information, means of identification, and data from compromised databases, among other items,” the DOJ said in a written statement. “Members could also earn credits through other means, such as by posting instructions on how to commit certain illegal acts.”
Prosecutors say Coelho also personally sold stolen data on the platform, and that Omnipotent directly facilitated illicit transactions by operating a fee-based “Official Middleman” service, a kind of escrow or insurance service that denizens of RaidForums were encouraged to use when transacting with other criminals.
Investigators described multiple instances wherein undercover federal agents or confidential informants used Omnipotent’s escrow service to purchase huge tranches of data from one of Coelho’s alternate user identities — meaning Coelho not only sold data he’d personally hacked but also further profited by insisting the transactions were handled through his own middleman service.
Not all of those undercover buys went as planned. One incident described in an affidavit by prosecutors (PDF) appears related to the sale of tens of millions of consumer records stolen last year from T-Mobile, although the government refers to the victim only as a major telecommunications company and wireless network operator in the United States.
On Aug. 11, 2021, an individual using the moniker “SubVirt” posted on RaidForums an offer to sell Social Security numbers, dates of birth and other records on more than 120 million people in the United States (SubVirt would later edit the sales thread to say 30 million records). Just days later, T-Mobile would acknowledge a data breach affecting 40 million current, former or prospective customers who applied for credit with the company.
The government says the victim firm hired a third-party to purchase the database and prevent it from being sold to cybercriminals. That third-party ultimately paid approximately $200,000 worth of bitcoin to the seller, with the agreement that the data would be destroyed after sale. “However, it appears the co-conspirators continued to attempt to sell the databases after the third-party’s purchase,” the affidavit alleges.
The FBI’s seizure of RaidForums was first reported by KrebsOnSecurity on Mar. 23, after a federal investigator confirmed rumors that the FBI had been secretly operating the RaidForums website for weeks.
Coelho landed on the radar of U.S. authorities in June 2018, when he tried to enter the United States at the Hartsfield-Jackson International Airport in Atlanta. The government obtained a warrant to search the electronic devices Coelho had in his luggage and found text messages, files and emails showing he was the RaidForums administrator Omnipotent.
“In an attempt to retrieve his items, Coelho called the lead FBI case agent on or around August 2, 2018, and used the email address unrivalled@pm.me to email the agent,” the government’s affidavit states. Investigators found this same address was used to register rf.ws and raid.lol, which Omnipotent announced on the forum would serve as alternative domain names for RaidForums in case the site’s primary domain was seized.
The DOJ said Coelho was arrested in the United Kingdom on January 31, at the United States’ request, and remains in custody pending the resolution of his extradition hearing. A statement from the U.K.’s National Crime Agency (NCA) said the RaidForum’s takedown was the result of “Operation Tourniquet,” which was carried out by the NCA in cooperation with the United Staes, Europol and four other countries, and resulted in “a number of linked arrests.”
A copy of the indictment against Coelho is available here (PDF).
from Krebs on Security https://ift.tt/KQZ4lGt
via IFTTT
Fortunately, we’re not talking about a robot revolution, or about hospital AI run amuck. But these bugs could lead to ransomware, or worse…
from Naked Security https://ift.tt/s6Mi987
via IFTTT

By BY DAISUKE WAKABAYASHI, ERIN GRIFFITH AND KATE CONGER
Tech companies really want their employees to be happy — or at least less annoyed — about returning. So they’re providing concerts, food trucks and other perks.
Published: April 12, 2022 at 11:00AM
from NYT Technology https://ift.tt/Qz65tMR
via IFTTT
(adsbygoogle = window.adsbygoogle || []).push({});
Para el uso que yo hago de la Rasperry Pi, que en parte hago pruebas y en parte la uso de Media Center y jugar, el mejor sistema operativo que existe es Twister OS. Aunque termina en «OS» (Operating System), lo que es en realidad es un Raspberry Pi OS vitaminado, con software útil y unos temas o «skins» especiales. Un software que tiene instalado y funcionando por defecto es RetroPie, y la experiencia es, hasta donde llega la placa, exquisita. ¿Se puede instalar RetroPie en ordenadores de escritorio? Pues sí, pero de manera oficial y para Linux sólo se soporta en sistemas basados en Debian. Por suerte, los usuarios de Arch Linux también tenemos ArchyPie-Setup.
Porque sí, está claro que en Arch Linux tenemos todo lo necesario para conseguir lo mismo que en RetroPie. De hecho, el software funciona en su mayoría con EmulationStation, RetroArch y otros emuladores, pero lo bueno de RetroPie es que es instalar y usar. Si un usuario de Arch Linux instala EmulationStation, se dará cuenta de que no puede hacer nada si no edita manualmente el archivo de configuración, demasiado tedioso para mi gusto (y supongo que no soy el único). Lo que hace ArchyPie-Setup es facilitar las cosas, y permitirnos tener «rpie» en Arch Linux.
(adsbygoogle = window.adsbygoogle || []).push({});
El uso de este script es muy sencillo, tal y como leemos en su página web oficial. Lo único es que, dependiendo del equipo en el que lo usemos, la instalación se tomará su tiempo, algo comprensible si tenemos en cuenta que va a instalar muchos emuladores «out of the box». Sólo necesitamos tener el equipo actualizado, git y ejecutar el script, lo que haremos con estos comandos:
Terminal
sudo pacman -Syyu sudo pacman -S git git clone --depth=1 https://github.com/V0rt3x667/ArchyPie-Setup.git cd ArchyPie-Setup sudo ./archypie_setup.sh
De lo anterior, el primero actualiza los repositorios, necesario para las dependencias; el segundo, si no lo tenemos, instala git; el tercero clona el repositorio; con el cuarto entramos en la carpeta de ArchyPie-Setup; y con el quinto lanzamos el script. Lo que veremos será poco más o menos lo que vemos al instalarlo en la Raspberry Pi: va construyendo y bajando todo lo necesario. Cuando deja de trabajar, sólo tenemos que ir al menú de inicio y buscar «rpie». Al lanzarlo entraremos en EmulationStation y podremos empezar a jugar.
Como RetroPie, ArchyPie-Setup no incluye ni juegos ni bios. Se los tenemos que añadir por nuestra cuenta. La carpeta se crea en nuestro directorio personal, y si queremos moverla hay que entrar en los ajustes para indicarle dónde tiene que buscar los juegos, roms y demás. «Peccata minuta» si tenemos en cuenta que podremos jugar a RetroPie, con todo configurado, en Arch Linux, del mismo modo que lo haríamos en Debian, Ubuntu o Linux Mint.
(adsbygoogle = window.adsbygoogle || []).push({});
from Linux Adictos https://ift.tt/qWFni0N
via IFTTT

Like zero trust, the cybersecurity mesh re-envisions the perimeter at the identity layer and centers upon unifying disparate security tools into a single, interoperable ecosystem.
from Dark Reading https://ift.tt/ZLOXPyw
via IFTTT
Gearing up to shred the slopes or dive into the seas? These photography tools are made for danger.
from Gear Latest https://ift.tt/wkBh0Qg
via IFTTT
This ICS-capable malware targets a Ukrainian energy company
The post Industroyer2: Industroyer reloaded appeared first on WeLiveSecurity
from WeLiveSecurity https://ift.tt/DYs4Jok
via IFTTT

(adsbygoogle = window.adsbygoogle || []).push({});
Ha pasado un tiempo sin noticias desde Slimbook. Y lo cierto es que cuando están «callados» están tramando «maldades», pero de esas maldades que tanto nos gustan a los linuxeros: con PCs de sobremesa, portátiles, miniPCs y AIOs que no solo pueden llevar una distro GNU/Linux, sino que pueden competir en calidad y rendimiento con los mejores.
Si estás impaciente por conocer todo lo que han estado tramando durante este tiempo, aquí tienes todas las novedades que tiene la firma española para este 2022:
(adsbygoogle = window.adsbygoogle || []).push({});
Eso en cuanto al apartado técnico, pero en Slimbook cuando se ponen, se ponen de verdad. Otra novedad a nivel corporativo es su nuevo logotipo:
![]()
Y eso no es todo, también hay cambios en algún software de los que desarrolla la valenciana. Se trata de su Slimbook Battery, que llega con una nueva versión con algunas novedades:
(adsbygoogle = window.adsbygoogle || []).push({});
from Linux Adictos https://ift.tt/crQhgM6
via IFTTT