QNAP and Synology say flaws in the Netatalk fileserver allow remote code execution and information disclosure.
from Dark Reading https://ift.tt/OhpNZYq
via IFTTT

QNAP and Synology say flaws in the Netatalk fileserver allow remote code execution and information disclosure.
from Dark Reading https://ift.tt/OhpNZYq
via IFTTT
This scale of this month’s encrypted DDoS attack over HTTPS suggests a well-resourced operation, analysts say.
from Dark Reading https://ift.tt/UzEgNWv
via IFTTT
Google said this week it is expanding the types of data people can ask to have removed from search results, to include personal contact information like your phone number, email address or physical address. The move comes just months after Google rolled out a new policy enabling people under the age of 18 (or a parent/guardian) to request removal of their images from Google search results.
Google has for years accepted requests to remove certain sensitive data such as bank account or credit card numbers from search results. In a blog post on Wednesday, Google’s Michelle Chang wrote that the company’s expanded policy now allows for the removal of additional information that may pose a risk for identity theft, such as confidential log-in credentials, email addresses and phone numbers when it appears in Search results.
“When we receive removal requests, we will evaluate all content on the web page to ensure that we’re not limiting the availability of other information that is broadly useful, for instance in news articles,” Chang wrote. “We’ll also evaluate if the content appears as part of the public record on the sites of government or official sources. In such cases, we won’t make removals.”
Google says a removal request will be considered if the search result in question includes the presence of “explicit or implicit threats” or “explicit or implicit calls to action for others to harm or harass.” The company says if it approves your request, it may respond by removing the provided URL(s) for all queries, or for only queries including your name.
While Google’s removal of a search result from its index will do nothing to remove the offending content from the site that is hosting it, getting a link decoupled from Google search results is going to make the content at that link far less visible. According to recent estimates, Google enjoys somewhere near 90 percent market share in search engine usage.
KrebsOnSecurity decided to test this expanded policy with what would appear to be a no-brainer request: I asked Google to remove search result for BriansClub, one of the largest (if not THE largest) cybercrime stores for selling stolen payment card data.
BriansClub has long abused my name and likeness to pimp its wares on the hacking forums. Its homepage includes a copy of my credit report, Social Security card, phone bill, and a fake but otherwise official looking government ID card.
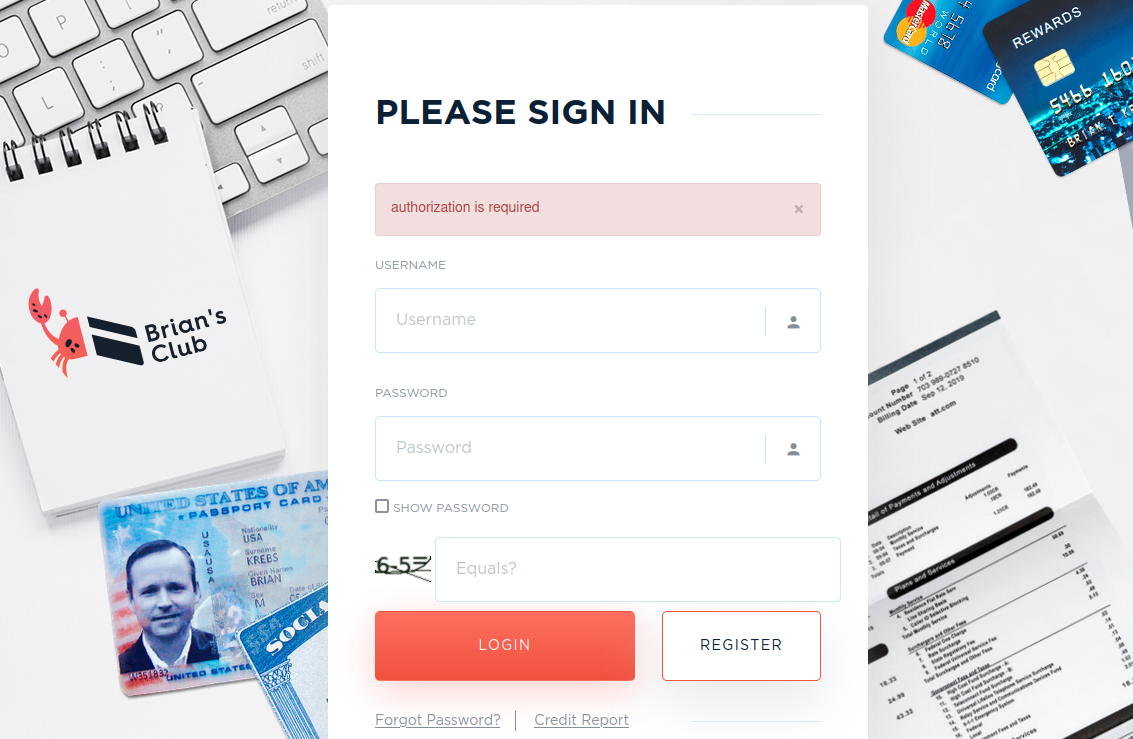
The login page for perhaps the most bustling cybercrime store for stolen payment card data.
Briansclub updated its homepage with this information in 2019, after it got massively hacked and a copy of its customer database was shared with this author. The leaked data — which included 26 million credit and debit card records taken from hacked online and brick-and-mortar retailers — was ultimately shared with dozens of financial institutions.
TechCrunch writes that the policy expansion comes six months after Google started allowing people under 18 or their parents request to delete their photos from search results. To do so, users need to specify that they want Google to remove “Imagery of an individual currently under the age of 18” and provide some personal information, the image URLs and search queries that would surface the results. Google also lets you submit requests to remove non-consensual explicit or intimate personal images from Google, along with involuntary fake pornography, TechCrunch notes.
This post will be updated in the event Google responds one way or the other, but that may take a while: Google’s automated response said: “Due to the preventative measures being taken for our support specialists in light of COVID-19, it may take longer than usual to respond to your support request. We apologize for any inconvenience this may cause, and we’ll send you a reply as soon as we can.”
from Krebs on Security https://ift.tt/qusomY5
via IFTTT

By BY KELLEN BROWNING AND ERIN GRIFFITH
The grocery delivery start-up changed its leadership, slashed its valuation and shifted its strategy after sales slowed.
Published: April 29, 2022 at 01:14PM
from NYT Technology https://ift.tt/MjhW5rs
via IFTTT
Learn how to find out which apps you’ve given access rights to, and how to revoke those rights immediately in an emergency.
from Naked Security https://ift.tt/yuTaqis
via IFTTT
Environmental surveillance – complementary tool for tracking COVID-19
Sebastian Oliel
29 Apr 2022
from PAHO/WHO | Pan American Health Organization https://ift.tt/o7pL0O3
via IFTTT
(adsbygoogle = window.adsbygoogle || []).push({});
Hay muchas cosas que en Windows y macOS son más sencillas, en parte porque no existe esa «fragmentación» que hay en Linux en la que cada maestrillo tiene su librillo, y cada desarrollador su manera de hacer las cosas. Cuando queremos actualizar el firmware en uno de esos sistemas operativos que vienen instalados por defecto en la mayoría de ordenadores solemos tirar de una herramienta que está bien a la vista, y lo más parecido a eso que hay en Linux es lo que se ha actualizado hace unas horas a fwupd 1.8.
Esta versión sucede a la v1.7 que se lanzó a mediados del octubre pasado, y llegó con soporte para hardware de Logitech, entre otros. fwupd 1.8 ha llegado con nuevas posibilidades, pero también ampliando el soporte para más hardware, entre lo que se incluye el Google Servo Dock.
(adsbygoogle = window.adsbygoogle || []).push({});
Añadido soporte a hardware como:
Y la lista de nuevas funciones (corrección de errores aparte):
Más información y descarga en este enlace.
(adsbygoogle = window.adsbygoogle || []).push({});
from Linux Adictos https://ift.tt/8lOEcsi
via IFTTT

Encryption will break, so it’s important to mix and layer different encryption methods.
from Dark Reading https://ift.tt/zml6Rcw
via IFTTT
Whether you want a backyard presenter or a theater-quality behemoth, our picks will help you upgrade your at-home movie nights.
from Gear Latest https://ift.tt/7yi8XKo
via IFTTT