A movie stuntman will stop at nothing to get revenge on the thugs who murdered his fiancée.
from New On Netflix USA https://ift.tt/LpJYkyr
via IFTTT

A movie stuntman will stop at nothing to get revenge on the thugs who murdered his fiancée.
from New On Netflix USA https://ift.tt/LpJYkyr
via IFTTT

(adsbygoogle = window.adsbygoogle || []).push({});
Que el sistema operativo perfecto no existe es algo bien sabido. Cada uno tiene sus puntos fuertes y puntos débiles, y uno de los buenos que mencionamos los usuarios de Linux es que los sistemas basados en su kernel son seguros. ¿Es esto cierto? Bueno, hay que tener en cuenta varios puntos: sí está diseñado para ser seguro, pero si podemos dormir más tranquilos que los usuarios de Windows, por ejemplo, es en realidad porque somos tan pocos que no interesamos a los usuarios malintencionados. Por eso y porque en Linux se corrigen los fallos de seguridad muy rápido.
¿Cuántas veces habéis leído una noticia sobre un fallo de seguridad en Linux, habéis encendido vuestro PC y ya teníais el parche esperando como actualización? Está claro que no siempre es así. A principios de este mes publicamos un artículo sobre un fallo que estuvo presente nada menos que 12 años, pero eso no es lo habitual. Aún contando con esos fallos, la media de días que pasan entre el descubrimiento de la vulnerabilidad y su parche es de 25 días.
(adsbygoogle = window.adsbygoogle || []).push({});
Estos datos los ha publicado Google a través de su Project Zero. En la lista también aparecen compañías como Samsung, Oracle o Mozilla, pero si nos centramos en las que desarrollan sistemas operativos, Linux los corrige en (de media) 25 días, Google, quien además de Chrome también es el responsable de Android, en 44, Apple en 69 y Microsoft en 83.
En cuanto a cantidad de bugs, quien sale peor parado de los anteriores es Apple, con 84, seguido de cerca por Microsoft, con 80. No está de más recordar aquí que Microsoft no desarrolla tantos sistemas como Apple, quien trabaja en macOS, iOS, iPadOS, tvOS… Pero los datos son los que son. Ya lejos de Apple y Microsoft está Google, con 56 fallos, y en Linux se encontraron menos de la mitad, 25.
Estos datos corresponden a lo encontrado entre 2019 y 2021, y creo que lo importante aquí es la velocidad. La comunidad Linux es muy activa, y cuando descubren un fallo importante pueden solucionarlo en horas. No tendremos un sistema operativo perfecto, como nadie, pero creo que sí podemos estar más tranquilos que los usuarios de Microsoft y Apple.
(adsbygoogle = window.adsbygoogle || []).push({});
from Linux Adictos https://ift.tt/Mg2UWXw
via IFTTT
(adsbygoogle = window.adsbygoogle || []).push({});
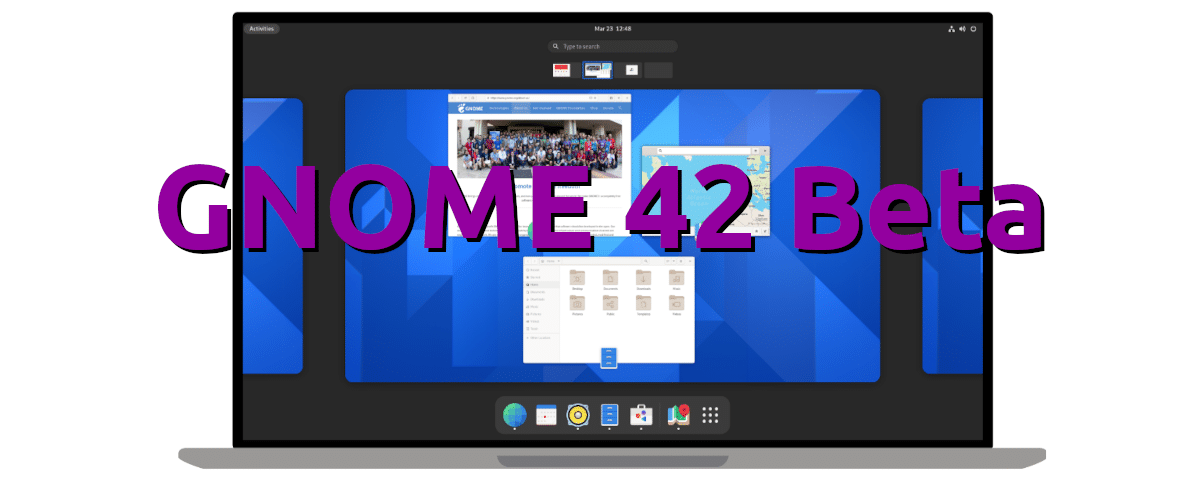
Poco más de un mes después de entregarnos la Alfa, el proyecto que hay detrás del escritorio más usado en Linux ha lanzado GNOME 42 Beta. Además de que el software ya está más pulido que hace cuatro semanas, esta beta marca el inicio de la congelación de interfaz, funciones y APIs, es decir, que aún se podrán introducir retoques, pero ya se centrarán más en corregir bugs que en cambios importantes y visibles.
Lo que no menciona la nota de este lanzamiento es que ya está disponible la nueva herramienta de capturas de pantalla de pantalla. Algunos usuarios de GNOME saben que, además de la que hace «fotos», GNOME tiene una función nativa para grabar el escritorio, pero su uso es de todo menos sencillo. Hace tiempo que aceptaron su integración en la próxima versión de GNOME, por lo que es lógico pensar que ya se podrá probar en GNOME 42 beta.
(adsbygoogle = window.adsbygoogle || []).push({});
Entre las novedades que llegan junto a GNOME 42 Beta, que se esperan también en la versión estable, tenemos que la aplicación de llamadas puede gestionar URIs tel:// y puede añadir contactos desde el historial de llamadas, Epiphany ha actualizado su código de PDF.js y readability.js, GJS usa ahora SpiderMonkey 91, lo que lo hace compatible con nuevas funciones de JavaScript, se han añadido nuevos fondos de pantalla para los temas claros y oscuros, y una transición para pasar entre ellos, el Bluetooth ahora muestra información sobre la batería en dispositivos compatibles, Archivos (Nautilus) ahora soporta el modo oscuro, como GNOME Software, mucho software ha pasado a usar GTK4 y libadwaita, y mi función favorita, la aplicación de capturas de pantalla que ahora permite grabar el escritorio.
Tal y como explica Project GNOME, la mejor y más segura manera de probar GNOME 42 Beta es usando la imagen de su OS, disponible en este enlace. Aunque lo llaman GNOME OS, no es un sistema operativo completo, sino una imagen para probar todas las novedades antes de tiempo. En unas semanas lanzarán la Release Candidate, y GNOME 42 llegará en forma de versión estable el 23 de marzo.
from Linux Adictos https://ift.tt/I0CbVO8
via IFTTT

By BY SHIRA OVIDE
Apple is making a stink over a Dutch regulator’s effort to change its app store. Here’s why the tech giant cares.
Published: February 22, 2022 at 11:40AM
from NYT Technology https://ift.tt/9YPjqvH
via IFTTT

By BY KELLEN BROWNING
Even as they allow some employees to change how often they come into the office, tech companies are rapidly buying and leasing properties around the country.
Published: February 22, 2022 at 02:00AM
from NYT Technology https://ift.tt/BjhZXme
via IFTTT

The U.S. Internal Revenue Service (IRS) said Monday that taxpayers are no longer required to provide facial scans to create an account online at irs.gov. In lieu of providing biometric data, taxpayers can now opt for a live video interview with ID.me, the privately-held Virginia company that runs the agency’s identity proofing system. The IRS also said any biometric data already shared with ID.me would be permanently deleted over the next few weeks, and any biometric data provided for new signups will be destroyed after an account is created.
“Taxpayers will have the option of verifying their identity during a live, virtual interview with agents; no biometric data – including facial recognition – will be required if taxpayers choose to authenticate their identity through a virtual interview,” the IRS said in a Feb. 21 statement.
“Taxpayers will still have the option to verify their identity automatically through the use of biometric verification through ID.me’s self-assistance tool if they choose,” the IRS explained. “For taxpayers who select this option, new requirements are in place to ensure images provided by taxpayers are deleted for the account being created. Any existing biometric data from taxpayers who previously created an IRS Online Account that has already been collected will also be permanently deleted over the course of the next few weeks.”
In addition, the IRS said it planned to roll out Login.gov as an authentication tool for those seeking access to their tax records online. Login.gov is a single sign-on solution already used to access 200 websites run by 28 federal agencies.
“The General Services Administration is currently working with the IRS to achieve the security standards and scale required of Login.Gov, with the goal of moving toward introducing this option after the 2022 filing deadline,” the agency wrote.
The IRS first announced its partnership with ID.me in November, but the press release received little public attention. On Jan. 19, KrebsOnSecurity published the story IRS Will Soon Require Selfies for Online Access, detailing a rocky experience signing up for IRS access via ID.me.
The IRS says it will require ID.me for all logins later this summer.
That story went viral, and the ensuing media coverage forced the IRS to answer questions about why it was incentivizing the collection and storage of biometric data by a private company. On Feb. 7, the IRS announced its intention to transition away from requiring biometric data from taxpayers who wish to access their records at the agency’s website, but it left unanswered the question of what would happen with the facial recognition data already collected by ID.me on behalf of the IRS.
In a letter to the IRS this month, Senate Finance Committee Chairman Ron Wyden (D-Ore.) challenged the Treasury Department and IRS to reconsider the biometric requirements, saying login.gov is perfectly up to the task if given all of the resources and funding it deserves.
“Unfortunately, login.gov has not yet reached its full potential, in part because many agencies have flouted the Congressional mandate that they use it, and because successive Administrations have failed to prioritize digital identity,” Wyden wrote. “The cost of this inaction has been billions of dollars in fraud, which has in turn fueled a black market for stolen personal data, and enabled companies like ID.me to commercialize what should be a core government service.”
from Krebs on Security https://ift.tt/KCjQtbl
via IFTTT
A straight-talking bug report written in plain English by an actual expert – there’s a teachable moment in this cybersecurity story!
from Naked Security https://ift.tt/2H6UsKc
via IFTTT
Missouri Governor Mike Parson made headlines last year when he vowed to criminally prosecute a journalist for reporting a security flaw in a state website that exposed personal information of more than 100,000 teachers. But Missouri prosecutors now say they will not pursue charges following revelations that the data had been exposed since 2011 — two years after responsibility for securing the state’s IT systems was centralized within Parson’s own Office of Administration.

Missouri Gov. Mike Parson (R), vowing to prosecute the St. Louis Post-Dispatch for reporting a security vulnerability that exposed teacher SSNs.
In October 2021, St. Louis Post-Dispatch reporter Josh Renaud alerted Missouri education department officials that their website was exposing the Social Security numbers of more than 100,000 primary and secondary teachers in the state. Renaud found teachers’ SSNs were accessible in the HTML source code of some Missouri education department webpages.
After confirming that state IT officials had secured the exposed teacher data, the Post-Dispatch ran a story about their findings. Gov. Parson responded by holding a press conference in which he vowed his administration would seek to prosecute and investigate “the hackers” and anyone who aided the publication in its “attempt to embarrass the state and sell headlines for their news outlet.”
“The state is committed to bringing to justice anyone who hacked our systems or anyone who aided them to do so,” Parson said in October. “A hacker is someone who gains unauthorized access to information or content. This individual did not have permission to do what they did. They had no authorization to convert or decode, so this was clearly a hack.”
Parson tasked the Missouri Highway Patrol to produce a report on their investigation into “the hackers.” On Monday, Feb. 21, The Post-Dispatch published the 158-page report (PDF), which concluded after 175 hours of investigation that Renaud did nothing wrong and only accessed information that was publicly available.
Emails later obtained by the Post-Dispatch showed that the FBI told state cybersecurity officials that there was “not an actual network intrusion” and the state database was “misconfigured.” The emails also revealed the proposed message when education department leaders initially prepared to respond in October:
“We are grateful to the member of the media who brought this to the state’s attention,” was the proposed quote attributed to the state’s education commissioner before Parson began shooting the messenger.
The Missouri Highway Patrol report includes an interview with Mallory McGowin, the chief communications officer for the state’s Department of Elementary and Secondary Education (DESE). McGowin told police the website weakness actually exposed 576,000 teacher Social Security numbers, and the data would have been publicly exposed for a decade.
McGowin also said the DESE’s website was developed and maintained by the Office of Administration’s Information Technology Services Division (ITSD) — which the governor’s office controls directly.
“I asked Mrs. McGowin if I was correct in saying the website was for DESE but it was maintained by ITSD, and she indicated that was correct,” the Highway Patrol investigator wrote. “I asked her if the ITSD was within the Office of Administration, or if DESE had their on-information technology section, and she indicated it was within the Office of Administration. She stated in 2009, policy was changed to move all information technology services to the Office of Administration.”
The report was a vindication for Renaud and for University of Missouri-St. Louis professor Shaji Khan, who helped the Post-Dispatch verify that the security flaw existed. Khan was also a target of Parson’s vow to prosecute “the hackers.” Khan’s attorney Elad Gross told the publication his client was not being charged, and that “state officials committed all of the wrongdoing here.”
“They failed to follow basic security procedures for years, failed to protect teachers’ Social Security numbers, and failed to take responsibility, instead choosing to instigate a baseless investigation into two Missourians who did the right thing and reported the problem,” Gross told The Post-Dispatch. “We thank the Missouri State Highway Patrol and the Cole County Prosecutor’s Office for their diligent work on a case that never should have been sent to them.”
from Krebs on Security https://ift.tt/92sd4AL
via IFTTT
Don’t consider just the initial costs. Hidden factors include remediation, revenue loss, reputational harm, national security — even human life.
from Dark Reading https://ift.tt/LkKYhS5
via IFTTT
