
Taking to the Air and Sea to Study Ocean Eddies



Many online services allow users to reset their passwords by clicking a link sent via SMS, and this unfortunately widespread practice has turned mobile phone numbers into de facto identity documents. Which means losing control over one thanks to a divorce, job termination or financial crisis can be devastating.
Even so, plenty of people willingly abandon a mobile number without considering the potential fallout to their digital identities when those digits invariably get reassigned to someone else. New research shows how fraudsters can abuse wireless provider websites to identify available, recycled mobile numbers that allow password resets at a range of email providers and financial services online.

Researchers in the computer science department at Princeton University say they sampled 259 phone numbers at two major wireless carriers, and found 171 of them were tied to existing accounts at popular websites, potentially allowing those accounts to be hijacked.
The Princeton team further found 100 of those 259 numbers were linked to leaked login credentials on the web, which could enable account hijackings that defeat SMS-based multi-factor authentication.
“Our key finding is that attackers can feasibly leverage number recycling to target previous owners and their accounts,” the researchers wrote. “The moderate to high hit rates of our testing methods indicate that most recycled numbers are vulnerable to these attacks. Furthermore, by focusing on blocks of Likely recycled numbers, an attacker can easily discover available recycled numbers, each of which then becomes a potential target.”
The researchers located newly-recycled mobile numbers by browsing numbers made available to customers interested in signing up for a prepaid account at T-Mobile or Verizon (apparently AT&T doesn’t provide a similar interface). They said they were able to identify and ignore large blocks of new, unused numbers, as these blocks tend to be made available consecutively — much like newly printed money is consecutively numbered in stacks.
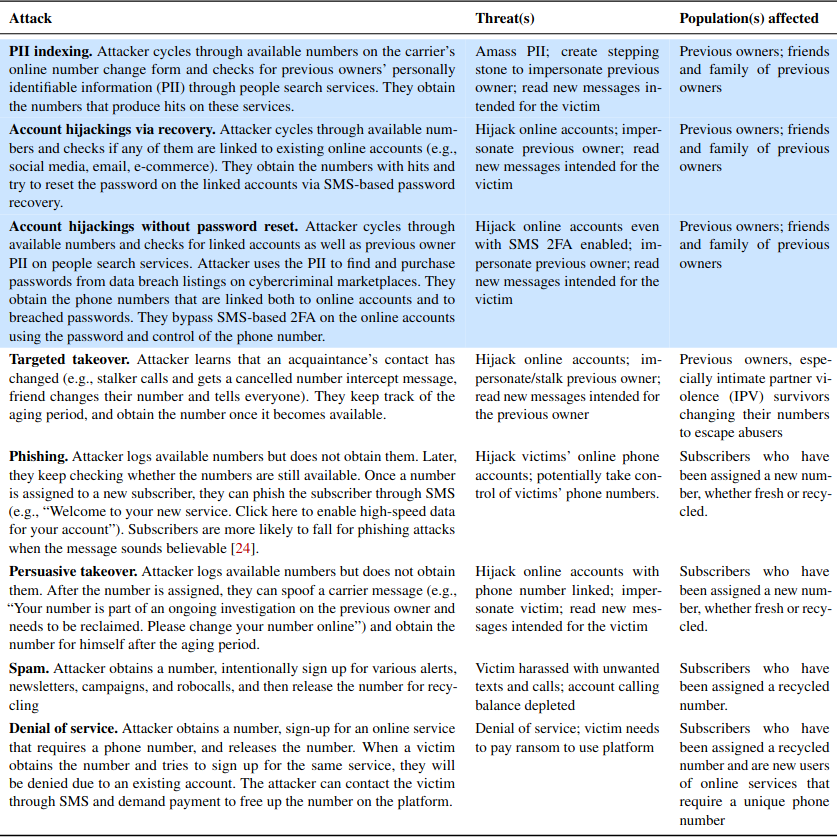
The Princeton team has a number of recommendations for T-Mobile and Verizon, noting that both carriers allow unlimited inquiries on their prepaid customer platforms online — meaning there is nothing to stop attackers from automating this type of number reconnaissance.
“On postpaid interfaces, Verizon already has safeguards and T-Mobile does not even support changing numbers online,” the researchers wrote. “However, the number pool is shared between postpaid and prepaid, rendering all subscribers vulnerable to attacks.”
They also recommend the carriers teach their support employees to remind customers about the risks of relinquishing a mobile number without first disconnecting it from other identities and sites online, advice they generally did not find was offered when interacting with customer support regarding number changes.
In addition, the carriers could offer their own “number parking” service for customers who know they will not require phone service for an extended period of time, or for those who just aren’t sure what they want to do with a number. Such services are already offered by companies like NumberBarn and Park My Phone, and they generally cost between $2-5 per month.
The Princeton study recommends consumers who are considering a number change instead either store the digits at an existing number parking service, or “port” the number to something like Google Voice. For a one-time $20 fee, Google Voice will let you port the number, and then you can continue to receive texts and calls to that number via Google Voice, or you can forward them to another number.
Porting seems like less of a hassle and potentially safer considering the average user has something like 150 accounts online, and a significant number of those accounts are going to be tied to one’s mobile number.
The full Princeton study is available here (PDF).
from Krebs on Security https://ift.tt/3yo6Kx6
via IFTTT

Aunque Google no nos ofreció uno de los datos más esperados de los últimos meses, el de la distribución del sistema operativo que acabó siendo movido a Android Studio y no volvió a actualizarse, en el Google I/O hubo sitio para una cifra, una cifra importante. En el mundo hay, en estos momentos, 3.000 millones de dispositivos Android activos según datos contabilizados a través de Google Play.
El dato llegó en el momento en que Sameer Samar, vicepresidente de gestión de producto de Google, tomó el escenario. Pero además hubo menciones a otros datos, como el hecho de que fue en 2017 cuando se superaron los 2.000 millones de dispositivos activos con Android. Otra cifra más que considerable que ha sido pulverizada tres temporadas más tarde, y que triplica la cifra ofrecida por la competencia directa, Apple, a primeros de año.
I made the audio recording shortly before she passed. I didn’t know that it would become a powerful tool to keep me motivated.
from Gear Latest https://ift.tt/3uWx7YR
via IFTTT
More attacks does not necessarily mean more threats, but all attacks types have increased, according to Akamai’s new ‘State of the Internet’ report.
from Dark Reading: https://ift.tt/3yoDZAj
via IFTTT
La organización ha tomado esta determinación debido a las “incertidumbres” de la pandemia
from Tendencias – Digital Trends Español https://ift.tt/3f0u4JJ
via IFTTT
And what’s needed to stop it: Better information sharing among private organizations and with law enforcement agencies.
from Dark Reading: https://ift.tt/2QC1wNi
via IFTTT
COVID19 Testing Management System 1.0 – ‘Admin name’ Cross-Site Scripting (XSS)
from Exploit-DB.com RSS Feed https://ift.tt/3u2BS1A
via IFTTT
COVID19 Testing Management System 1.0 – SQL Injection (Auth Bypass)
from Exploit-DB.com RSS Feed https://ift.tt/33XfagW
via IFTTT
The attack is a reminder of growing cyberthreats to critical infrastructure while also showing why providers of essential services are ripe targets for cybercriminals
The post Colonial Pipeline attack: Hacking the physical world appeared first on WeLiveSecurity
from WeLiveSecurity https://ift.tt/3fwnmu0
via IFTTT