Se trata de un producto limitado y exclusivo sólo para China: se venderán 400 mil unidades
from Tendencias – Digital Trends Español https://ift.tt/2J6Kgfk
via IFTTT

Se trata de un producto limitado y exclusivo sólo para China: se venderán 400 mil unidades
from Tendencias – Digital Trends Español https://ift.tt/2J6Kgfk
via IFTTT
Habría tenido “éxito parcial”, pero representa uno de los peores en la historia de Estados Unidos
from Tendencias – Digital Trends Español https://ift.tt/3gZ7CA1
via IFTTT
The operators behind DoppelPaymer have begun calling victims to pressure them into paying ransom, officials say.
from Dark Reading: https://ift.tt/3aqM8Lg
via IFTTT
Attack on thousands of other companies as “moment of reckoning” for governments and industry, company president says.
from Dark Reading: https://ift.tt/3awY8KS
via IFTTT
Lanzan un satélite que utiliza ecolocalización para ver a través de edificios
from Tendencias – Digital Trends Español https://ift.tt/2Wt8iUO
via IFTTT
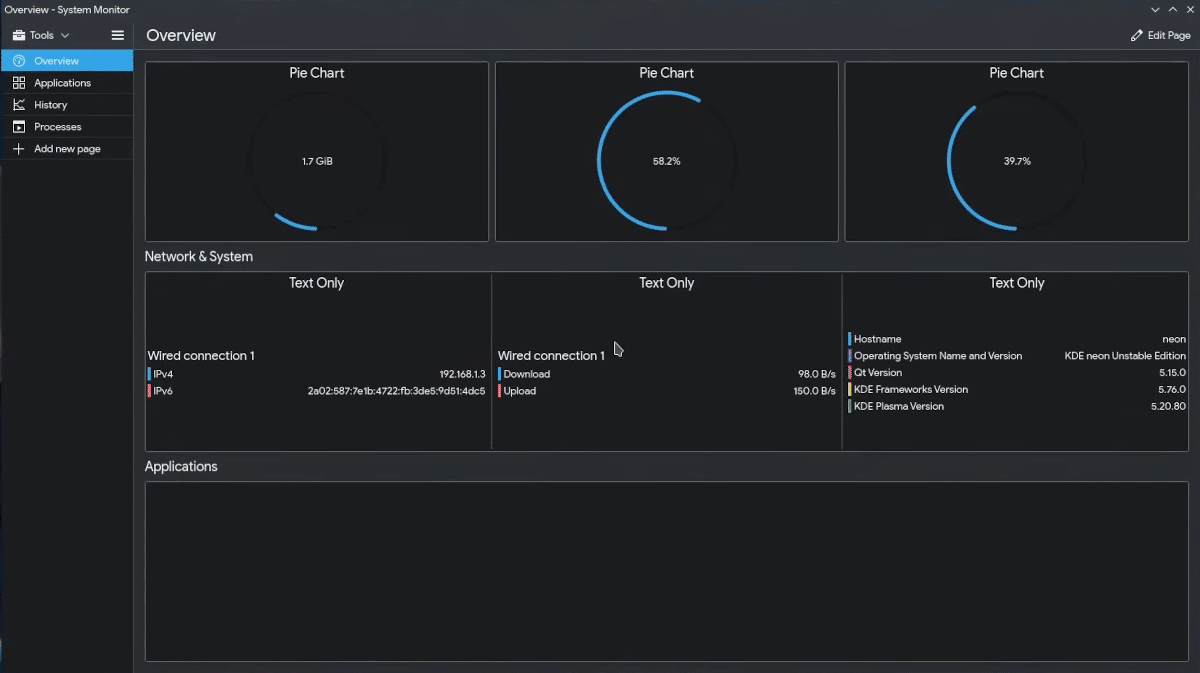
Ahora mismo, el escritorio KDE tiene como app de monitor del sistema KSysGuard. Es una herramienta de la que no creo que se haya quejado mucha gente, pero el proyecto KDE ha pensado que podía mejorarla y hace tiempo que está trabajando en Plasma System Monitor. En estos momentos, la app sigue en desarrollo, pero ya está disponible en Kubuntu 21.04 Hirsute Hippo, en parte porque estamos hablando de un sistema operativo 100% en desarrollo al que aún le faltan cuatro meses para que llegue a su versión estable.
La app ya tiene página en la tienda de KDE, disponible en este enlace, pero si intentamos instalarla en el Discover de Groovy Gorilla nos da error. En estos momentos, la única manera de probarla es consiguiendo el código y realizando la instalación manual o, y esto no lo he probado, en la versión Testing de KDE neon. Una cosa sí está clara: el diseño ha cambiado mucho, tanto que puede que a algunos usuarios nos cueste un poco hacernos a ella, aunque siempre se ha dicho que es fácil acostumbrarse a lo bueno.
Comparada con KSysGuard, lo que se espera que en castellano se llame Monitor del Sistema de Plasma parece una o dos generaciones más moderno. El panel lo tendremos a la izquierda, donde veremos una vista general, las aplicaciones que se están ejecutando, el historial y procesos activos, pero también podremos añadir más páginas. Como ya he mencionado, yo no me quejaba de KSysGuard, pero la nueva app está a otro nivel.
Por otra parte, algo que es menos emocionante pero no menos importante, también está disponible Plasma Disks, lo que es una herramienta que analizará la salud de nuestros discos duros y cuya página del proyecto tenéis en este enlace. Básicamente, empezando con el Plasma 5.20 que no llegará a Kubuntu hasta abril de 2021 por un tema de dependencias, el sistema operativo nos avisará si nuestro disco está fallando, lo que puede servirnos para empezar a tomar medidas o simplemente para plantearnos sustituirlo por otro.
Kubuntu ya ha anunciado que estas dos apps están disponibles en la última Daily Build de Hirsute Hippo, sistema que será lanzado oficialmente dentro de poco más de 4 meses.
from Linux Adictos https://ift.tt/3apjDgU
via IFTTT
TikTok elimina sin aviso previo las cuentas de varias trabajadoras sexuales
from Tendencias – Digital Trends Español https://ift.tt/3almR53
via IFTTT
Reunimos en una sola lista las 55 mejores series disponibles en Amazon Prime Video para disfrutar ahora mismo.
from Tendencias – Digital Trends Español https://ift.tt/2j6Vjam
via IFTTT
U.S. government cybersecurity agencies warned this week that the attackers behind the widespread hacking spree stemming from the compromise at network software firm SolarWinds used weaknesses in other, non-SolarWinds products to attack high-value targets. According to sources, among those was a flaw in software virtualization platform VMware, which the U.S. National Security Agency (NSA) warned on Dec. 7 was being used by Russian hackers to impersonate authorized users on victim networks.
On Dec. 7, 2020, the NSA said “Russian state-sponsored malicious cyber actors are exploiting a vulnerability in VMware Access and VMware Identity Manager products, allowing the actors access to protected data and abusing federated authentication.”
VMware released a software update to plug the security hole (CVE-2020-4006) on Dec. 3, and said it learned about the flaw from the NSA.
The NSA advisory (PDF) came less than 24 hours before cyber incident response firm FireEye said it discovered attackers had broken into its networks and stolen more than 300 proprietary software tools the company developed to help customers secure their networks.
On Dec. 13, FireEye disclosed that the incident was the result of the SolarWinds compromise, which involved malicious code being surreptitiously inserted into updates shipped by SolarWinds for users of its Orion network management software as far back as March 2020.
In its advisory on the VMware vulnerability, the NSA urged patching it “as soon as possible,” specifically encouraging the National Security System, Department of Defense, and defense contractors to make doing so a high priority.
The NSA said that in order to exploit this particular flaw, hackers would already need to have access to a vulnerable VMware device’s management interface — i.e., they would need to be on the target’s internal network (provided the vulnerable VMware interface was not accessible from the Internet). However, the SolarWinds compromise would have provided that internal access nicely.
In response to questions from KrebsOnSecurity, VMware said it has “received no notification or indication that the CVE 2002-4006 was used in conjunction with the SolarWinds supply chain compromise.”
VMware added that while some of its own networks used the vulnerable SolarWinds Orion software, an investigation has so far revealed no evidence of exploitation.
“While we have identified limited instances of the vulnerable SolarWinds Orion software in our environment, our own internal investigation has not revealed any indication of exploitation,” the company said in a statement. “This has also been confirmed by SolarWinds own investigations to date.”
On Dec. 17, DHS’s Cyber Security and Infrastructure Security Agency (CSIA) released a sobering alert on the SolarWinds attack, noting that CISA had evidence of additional access vectors other than the SolarWinds Orion platform.
CSIA’s advisory specifically noted that “one of the principal ways the adversary is accomplishing this objective is by compromising the Security Assertion Markup Language (SAML) signing certificate using their escalated Active Directory privileges. Once this is accomplished, the adversary creates unauthorized but valid tokens and presents them to services that trust SAML tokens from the environment. These tokens can then be used to access resources in hosted environments, such as email, for data exfiltration via authorized application programming interfaces (APIs).”
Indeed, the NSA’s Dec. 7 advisory said the hacking activity it saw involving the VMware vulnerability “led to the installation of a web shell and follow-on malicious activity where credentials in the form of SAML authentication assertions were generated and sent to Microsoft Active Directory Federation Services (ADFS), which in turn granted the actors access to protected data.”
Also on Dec. 17, the NSA released a far more detailed advisory explaining how it has seen the VMware vulnerability being used to forge SAML tokens, this time specifically referencing the SolarWinds compromise.
CSIA’s analysis suggested the crooks behind the SolarWinds intrusion were heavily focused on impersonating trusted personnel on targeted networks, and that they’d devised clever ways to bypass multi-factor authentication (MFA) systems protecting networks they targeted.
The bulletin references research released earlier this week by security firm Volexity, which described encountering the same attackers using a novel technique to bypass MFA protections provided by Duo for Microsoft Outlook Web App (OWA) users.
Duo’s parent Cisco Systems Inc. responded that the attack described by Volexity didn’t target any specific vulnerability in its products. As Ars Technica explained, the bypass involving Duo’s protections could have just as easily involved any of Duo’s competitors.
“MFA threat modeling generally doesn’t include a complete system compromise of an OWA server,” Ars’ Dan Goodin wrote. “The level of access the hacker achieved was enough to neuter just about any defense.”
Several media outlets, including The New York Times and The Washington Post, have cited anonymous government sources saying the group behind the SolarWinds hacks was known as APT29 or “Cozy Bear,” an advanced threat group believed to be part of the Russian Federal Security Service (FSB).
SolarWinds has said almost 18,000 customers may have received the backdoored Orion software updates. So far, only a handful of customers targeted by the suspected Russian hackers behind the SolarWinds compromise have been made public — including the U.S. Commerce, Energy and Treasury departments, and the DHS.
No doubt we will hear about new victims in the public and private sector in the coming days and weeks. In the meantime, thousands of organizations are facing incredibly costly, disruptive and time-intensive work in determining whether they were compromised and if so what to do about it.
The CSIA advisory notes the attackers behind the SolarWinds compromises targeted key personnel at victim firms — including cyber incident response staff, and IT email accounts. The warning suggests organizations that suspect they were victims should assume their email communications and internal network traffic are compromised, and rely upon or build out-of-band systems for discussing internally how they will proceed to clean up the mess.
“If the adversary has compromised administrative level credentials in an environment—or if organizations identify SAML abuse in the environment, simply mitigating individual issues, systems, servers, or specific user accounts will likely not lead to the adversary’s removal from the network,” CSIA warned. “In such cases, organizations should consider the entire identity trust store as compromised. In the event of a total identity compromise, a full reconstitution of identity and trust services is required to successfully remediate. In this reconstitution, it bears repeating that this threat actor is among the most capable, and in many cases, a full rebuild of the environment is the safest action.”
from Krebs on Security https://ift.tt/3mvmqYb
via IFTTT
Edwin Armstrong: 130 años del genio de la radio FM envuelto en tragedia
from Tendencias – Digital Trends Español https://ift.tt/37sMM90
via IFTTT