The North Korean operatives have attempted to steal more than $2 billion since 2015 in a series of ongoing campaigns.
from Dark Reading: https://ift.tt/3hwY7HJ
via IFTTT

The North Korean operatives have attempted to steal more than $2 billion since 2015 in a series of ongoing campaigns.
from Dark Reading: https://ift.tt/3hwY7HJ
via IFTTT
Discord te permite crear usuarios automatizados (bots) que cumplen funciones bastante útiles; aprende cómo.
from Tendencias – Digital Trends Español https://ift.tt/2XWlNMg
via IFTTT
Parece que Xiaomi sigue sumando éxitos a sus celebrados diez años de vida, y es que a la llegada de los nuevos Mi 10 Ultra y Redmi K30 Ultra tenemos que añadir un trofeo no menos importante otorgado por la propia Google y su programa Android Enterprise.
Y es que el gigante de Mountain View acaba de incluir al Redmi Note 9 Pro entre los Android Entreprise Recommended Phones convirtiéndolo en el primer móvil de Xiaomi no Android One -o lo que es lo mismo, con MIUI- que recibe esta recomendación de Google para empresas.

El Redmi Note 9 Pro es el primer móvil no Android One recomendado por Google para empresas
Nos lo contaban los chicos de xda-developers, comentando además que este programa Android Enterprise Recommended se creó en 2018 para certificar dispositivos que permitan una implementación más correcta en entornos de negocios o empresariales.
La idea de Google era facilitar a las empresas determinar qué dispositivos Android eran mejores como móviles o tabletas de empresa, teniendo que cumplir estos dispositivos unos requisitos mínimos de hardware, actualizaciones de seguridad como mínimo en períodos de 90 días durante 3 años o la posibilidad de adquirirlos desbloqueados, entre otras necesidades.
Siguiendo estas pautas Google ha certificado ya más de 150 dispositivos, tres ellos de Xiaomi, pero el Redmi Note 9 Pro será el primero con MIUI que reciba la certificación AER pues hasta la fecha sólo los Xiaomi Mi A2, Mi A2 Lite y Mi A3 la habían recibido todos ellos bajo el programa Android One ahora abandonado por Xiaomi.
Xiaomi ya disponía de tres móviles certificados para empresas por Google, pero todos ellos eran de la descatalogada serie Mi A con Android One, así que este Redmi Note 9 Pro es un pionero dentro de familia de móviles del gigante chino
Saber más: El Redmi K30 Ultra es oficial con pantalla a 120 Hz y procesador Dimensity 1000+

El sello Android Enterprise Recommended identifica a los mejores productos para empresas
Hablamos de un dispositivo con chipset Qualcomm Snapdragon 720G y firmware MIUI 11 bajo Android 10 como base, que cumple todos los requisitos a pesar de disponer de la personalización de Xiaomi y que además es uno de los móviles más atractivos que podemos encontrar en cuanto a su relación entre precio y prestaciones.
Dispone de un panel IPS de 6,67 pulgadas con resolución FHD+, configuraciones memoria de 6 GB de RAM y otros 64 ó 128 GB de almacenamiento, además de una batería de 5.020 mAh muy generosa, con soporte para carga rápida hasta 30W.
No falta un módulo fotográfico trasero de cuatro sensores para ponerse a la moda, con una cámara principal de 64 megapíxeles y lentes ultra gran angular, macro y profundidad para acompañar ofreciendo versatilidad. En el frontal hay otra cámara de 16 megapíxeles, y la conectividad es la esperada en cualquier móvil que se precie en 2020, incluyendo NFC y el lector dactilar para pagos móviles.
Con todo este arsenal es lógico que a Google le parezca un buen teléfono de empresa, sobre todo atendiendo a sus precios alrededor de los 225 euros que lo sitúan mejor en posición respecto a otros móviles también certificados como Android Enterprise Recommended como los OPPO Find X2, el OPPO Reno3 Pro o el OnePlus Nord, todos ellos también llegados desde China.
En Andro4all | Si eres fan de Xiaomi, estas son las figuras tipo Funko que te mereces
Más información | Android Enterprise Solutions Directory
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
La entrada Este es el primer móvil Xiaomi sin Android One que Google recomienda a las empresas se publicó primero en Andro4all.
from Andro4all https://ift.tt/32nC7IY
via IFTTT
Risk levels are not steady states. Here are six indications that the danger posed by your supply chain is headed in the wrong direction.
from Dark Reading: https://ift.tt/3gDF2m4
via IFTTT
Tormented by a demon and on the run from a Roman centurion, a 7-year-old Jesus and his parents, Mary and Joseph, flee Egypt for Nazareth.
from New On Netflix USA https://ift.tt/2G1Hcz9
via IFTTT
La temporada 9 ha llegado recientemente a Call of Duty: Mobile, esta vez con grandes cambios que sin duda mejoran la experiencia de los usuarios de diferentes formas. En este caso, la mayoría de las novedades se han enfocado en la interfaz de varios apartados y también en cambios para las armas en MJ y BR que han sido muy bien recibidos por los jugadores del título.
Esto es un paso más para hacer que Call of Duty: Mobile sea mucho más intuitivo y dinámico. Si todavía no te has enterado de todas las mejoras que han llegado, no te preocupes, a continuación te diremos cuáles han sido las más notables de todas y seguramente anteriormente tú también eras uno de esos usuarios que estaban esperando estos cambios.
Saber más: Estos son los requisitos que necesitas para jugar a Call of Duty: Mobile en tu Android

Call of Duty: Mobile – Armero
Las opciones de Armero son unas de las cosas más llamativas de la temporada 9, pues anteriormente, podíamos simplemente mejorar las armas con las Tarjetas XP de Armas, las cuales hacían que te dieran nuevos accesorios para modificar sus características. De hecho, muchas personas criticaban que no hacían nada con esas tarjetas porque habían muchas y nunca se acababan.
Finalmente, todas esas tarjetas que tenías guardadas, ahora las puedes usar y es más complicado hacer que tu arma aumente de nivel. Además, hay muchísimas más opciones para configurar las estadísticas, así también como la personalización de la apariencia.

Call of Duty: Mobile – Equipar accesorios MJ
El modo Multijugador contaba con variedad de accesorios para las armas, pero no eran tantos como ahorita. Ahora al entrar en el Armero, el jugador puede seleccionar entra una gran gama de miras, culatas, cañones, silenciadores, equipamiento de municiones, empuñaduras, acoples y bocas de cañones. Por otra parte, en la armería también se pueden conseguir Ventajas que le dan algún tipo de habilidad al arma.
Hay que considerar que estos accesorios se obtienen de la misma forma que se hacía anteriormente, haciendo que cada una de las armas suba de nivel.

Call of Duty: Mobile – Skins de armas
Al igual que los accesorios de la armería, también hay grandes cambios en la personalización de armas. Los desarrolladores han añadido muchas skins variadas que se dividen en las siguientes categorías:
Además de las skins, los jugadores también pueden ganar Amuletos, Retículas y Pegatinas para equiparlas al arma que deseen.

Call of Duty: Mobile – Nuevo selector de modo de juego
El selector del modo de juego ahora es más intuitivo y está mejor organizado con íconos en vertical. Cuando un jugador quiere seleccionar un modo, puede elegir entre los Principales, Destacados y Prácticas, así mismo también seleccionar el mapa donde quiere jugar.
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
La entrada Las 4 mejores novedades de la Temporada 9 de Call of Duty: Mobile se publicó primero en Andro4all.
from Andro4all https://ift.tt/2D6O11m
via IFTTT
Risk levels are not steady states. Here are six indications that the danger posed by your supply chain is headed in the wrong direction.
from Dark Reading: https://ift.tt/2Yx5xTV
via IFTTT
Los YouTubers son más grandes que las celebridades. Estos son los canales de YouTube que debes seguir.
from Redes sociales | Digital Trends Español https://ift.tt/35EQidw
via IFTTT
At the height of his cybercriminal career, the hacker known as “Hieupc” was earning $125,000 a month running a bustling identity theft service that siphoned consumer dossiers from some of the world’s top data brokers. That is, until his greed and ambition played straight into an elaborate snare set by the U.S. Secret Service. Now, after more than seven years in prison Hieupc is back in his home country and hoping to convince other would-be cybercrooks to use their computer skills for good.

Hieu Minh Ngo, in his teens.
For several years beginning around 2010, a lone teenager in Vietnam named Hieu Minh Ngo ran one of the Internet’s most profitable and popular services for selling “fullz,” stolen identity records that included a consumer’s name, date of birth, Social Security number and email and physical address.
Ngo got his treasure trove of consumer data by hacking and social engineering his way into a string of major data brokers. By the time the Secret Service caught up with him in 2013, he’d made over $3 million selling fullz data to identity thieves and organized crime rings operating throughout the United States.
Matt O’Neill is the Secret Service agent who in February 2013 successfully executed a scheme to lure Ngo out of Vietnam and into Guam, where the young hacker was arrested and sent to the mainland U.S. to face prosecution. O’Neill now heads the agency’s Global Investigative Operations Center, which supports investigations into transnational organized criminal groups.
O’Neill said he opened the investigation into Ngo’s identity theft business after reading about it in a 2011 KrebsOnSecurity story, “How Much is Your Identity Worth?” According to O’Neill, what’s remarkable about Ngo is that to this day his name is virtually unknown among the pantheon of infamous convicted cybercriminals, the majority of whom were busted for trafficking in huge quantities of stolen credit cards.
Ngo’s businesses enabled an entire generation of cybercriminals to commit an estimated $1 billion worth of new account fraud, and to sully the credit histories of countless Americans in the process.
“I don’t know of any other cybercriminal who has caused more material financial harm to more Americans than Ngo,” O’Neill told KrebsOnSecurity. “He was selling the personal information on more than 200 million Americans and allowing anyone to buy it for pennies apiece.”
Freshly released from the U.S. prison system and deported back to Vietnam, Ngo is currently finishing up a mandatory three-week COVID-19 quarantine at a government-run facility. He contacted KrebsOnSecurity from inside this facility with the stated aim of telling his little-known story, and to warn others away from following in his footsteps.
Ten years ago, then 19-year-old hacker Ngo was a regular on the Vietnamese-language computer hacking forums. Ngo says he came from a middle-class family that owned an electronics store, and that his parents bought him a computer when he was around 12 years old. From then on out, he was hooked.
In his late teens, he traveled to New Zealand to study English at a university there. By that time, he was already an administrator of several dark web hacker forums, and between his studies he discovered a vulnerability in the school’s network that exposed payment card data.
“I did contact the IT technician there to fix it, but nobody cared so I hacked the whole system,” Ngo recalled. “Then I used the same vulnerability to hack other websites. I was stealing lots of credit cards.”
Ngo said he decided to use the card data to buy concert and event tickets from Ticketmaster, and then sell the tickets at a New Zealand auction site called TradeMe. The university later learned of the intrusion and Ngo’s role in it, and the Auckland police got involved. Ngo’s travel visa was not renewed after his first semester ended, and in retribution he attacked the university’s site, shutting it down for at least two days.
Ngo said he started taking classes again back in Vietnam, but soon found he was spending most of his time on cybercrime forums.
“I went from hacking for fun to hacking for profits when I saw how easy it was to make money stealing customer databases,” Ngo said. “I was hanging out with some of my friends from the underground forums and we talked about planning a new criminal activity.”
“My friends said doing credit cards and bank information is very dangerous, so I started thinking about selling identities,” Ngo continued. “At first I thought well, it’s just information, maybe it’s not that bad because it’s not related to bank accounts directly. But I was wrong, and the money I started making very fast just blinded me to a lot of things.”
His first big target was a consumer credit reporting company in New Jersey called MicroBilt.
“I was hacking into their platform and stealing their customer database so I could use their customer logins to access their [consumer] databases,” Ngo said. “I was in their systems for almost a year without them knowing.”
Very soon after gaining access to MicroBilt, Ngo says, he stood up Superget[.]info, a website that advertised the sale of individual consumer records. Ngo said initially his service was quite manual, requiring customers to request specific states or consumers they wanted information on, and he would conduct the lookups by hand.
“I was trying to get more records at once, but the speed of our Internet in Vietnam then was very slow,” Ngo recalled. “I couldn’t download it because the database was so huge. So I just manually search for whoever need identities.”
But Ngo would soon work out how to use more powerful servers in the United States to automate the collection of larger amounts of consumer data from MicroBilt’s systems, and from other data brokers. As I wrote of Ngo’s service back in November 2011:
“Superget lets users search for specific individuals by name, city, and state. Each “credit” costs USD$1, and a successful hit on a Social Security number or date of birth costs 3 credits each. The more credits you buy, the cheaper the searches are per credit: Six credits cost $4.99; 35 credits cost $20.99, and $100.99 buys you 230 credits. Customers with special needs can avail themselves of the “reseller plan,” which promises 1,500 credits for $500.99, and 3,500 credits for $1000.99.
“Our Databases are updated EVERY DAY,” the site’s owner enthuses. “About 99% nearly 100% US people could be found, more than any sites on the internet now.”
Ngo’s intrusion into MicroBilt eventually was detected, and the company kicked him out of their systems. But he says he got back in using another vulnerability.
“I was hacking them and it was back and forth for months,” Ngo said. “They would discover [my accounts] and fix it, and I would discover a new vulnerability and hack them again.”
This game of cat and mouse continued until Ngo found a much more reliable and stable source of consumer data: A U.S. based company called Court Ventures, which aggregated public records from court documents. Ngo wasn’t interested in the data collected by Court Ventures, but rather in its data sharing agreement with a third-party data broker called U.S. Info Search, which had access to far more sensitive consumer records.
Using forged documents and more than a few lies, Ngo was able to convince Court Ventures that he was a private investigator based in the United States.
“At first [when] I sign up they asked for some documents to verify,” Ngo said. “So I just used some skill about social engineering and went through the security check.”
Then, in March 2012, something even more remarkable happened: Court Ventures was purchased by Experian, one of the big three major consumer credit bureaus in the United States. And for nine months after the acquisition, Ngo was able to maintain his access.

“After that, the database was under control by Experian,” he said. “I was paying Experian good money, thousands of dollars a month.”
Whether anyone at Experian ever performed due diligence on the accounts grandfathered in from Court Ventures is unclear. But it wouldn’t have taken a rocket surgeon to figure out that this particular customer was up to something fishy.
For one thing, Ngo paid the monthly invoices for his customers’ data requests using wire transfers from a multitude of banks around the world, but mostly from new accounts at financial institutions in China, Malaysia and Singapore.
O’Neill said Ngo’s identity theft website generated tens of thousands of queries each month. For example, the first invoice Court Ventures sent Ngo in December 2010 was for 60,000 queries. By the time Experian acquired the company, Ngo’s service had attracted more than 1,400 regular customers, and was averaging 160,000 monthly queries.
More importantly, Ngo’s profit margins were enormous.
“His service was quite the racket,” he said. “Court Ventures charged him 14 cents per lookup, but he charged his customers about $1 for each query.”
By this time, O’Neill and his fellow Secret Service agents had served dozens of subpoenas tied to Ngo’s identity theft service, including one that granted them access to the email account he used to communicate with customers and administer his site. The agents discovered several emails from Ngo instructing an accomplice to pay Experian using wire transfers from different Asian banks.
Working with the Secret Service, Experian quickly zeroed in on Ngo’s accounts and shut them down. Aware of an opportunity here, the Secret Service contacted Ngo through an intermediary in the United Kingdom — a known, convicted cybercriminal who agreed to play along. The U.K.-based collaborator told Ngo he had personally shut down Ngo’s access to Experian because he had been there first and Ngo was interfering with his business.
“The U.K. guy told Ngo, ‘Hey, you’re treading on my turf, and I decided to lock you out. But as long as you’re paying a vig through me, your access won’t go away’,” O’Neill recalled.
The U.K. cybercriminal, acting at the behest of the Secret Service and U.K. authorities, told Ngo that if he wanted to maintain his access, he could agree to meet up in person. But Ngo didn’t immediately bite on the offer.
Instead, he weaseled his way into another huge data store. In much the same way he’d gained access to Court Ventures, Ngo got an account at a company called TLO, another data broker that sells access to extremely detailed and sensitive information on most Americans.
TLO’s service is accessible to law enforcement agencies and to a limited number of vetted professionals who can demonstrate they have a lawful reason to access such information. In 2014, TLO was acquired by Trans Union, one of the other three big U.S. consumer credit reporting bureaus.
And for a short time, Ngo used his access to TLO to power a new iteration of his business — an identity theft service rebranded as usearching[.]info. This site also pulled consumer data from a payday loan company that Ngo hacked into, as documented in my Sept. 2012 story, ID Theft Service Tied to Payday Loan Sites. Ngo said the hacked payday loans site gave him instant access to roughly 1,000 new fullz records each day.
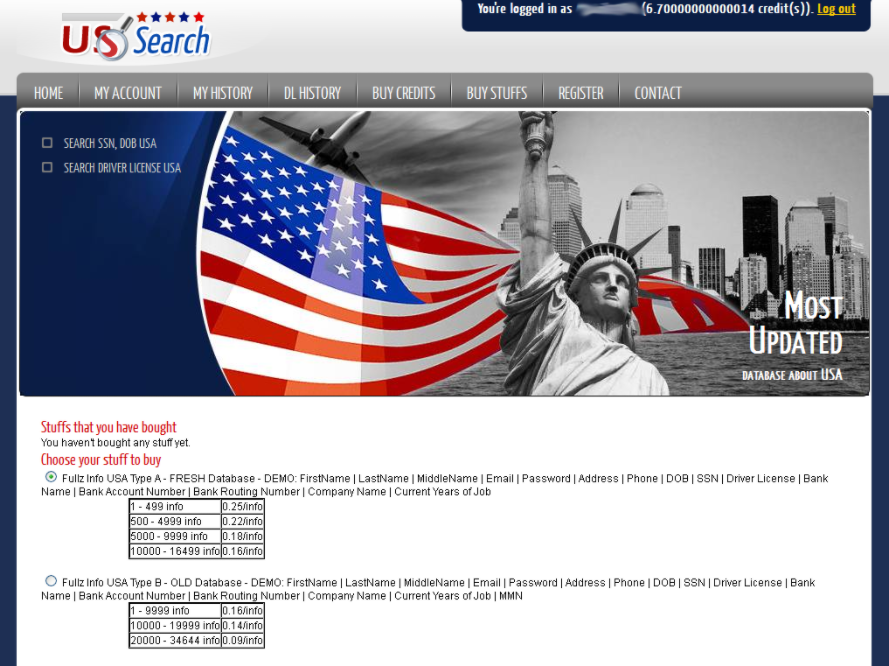
Ngo’s former ID theft service usearching[.]info.
By this time, Ngo was a multi-millionaire: His various sites and reselling agreements with three Russian-language cybercriminal stores online had earned him more than USD $3 million. He told his parents his money came from helping companies develop websites, and even used some of his ill-gotten gains to pay off the family’s debts (its electronics business had gone belly up, and a family member had borrowed but never paid back a significant sum of money).
But mostly, Ngo said, he spent his money on frivolous things, although he says he’s never touched drugs or alcohol.
“I spent it on vacations and cars and a lot of other stupid stuff,” he said.
When TLO locked Ngo out of his account there, the Secret Service used it as another opportunity for their cybercriminal mouthpiece in the U.K. to turn the screws on Ngo yet again.
“He told Ngo he’d locked him out again, and the he could do this all day long,” O’Neill said. “And if he truly wanted lasting access to all of these places he used to have access to, he would agree to meet and form a more secure partnership.”
After several months of conversing with his apparent U.K.-based tormentor, Ngo agreed to meet him in Guam to finalize the deal. Ngo says he understood at the time that Guam is an unincorporated territory of the United States, but that he discounted the chances that this was all some kind of elaborate law enforcement sting operation.
“I was so desperate to have a stable database, and I got blinded by greed and started acting crazy without thinking,” Ngo said. “Lots of people told me ‘Don’t go!,’ but I told them I have to try and see what’s going on.”
But immediately after stepping off of the plane in Guam, he was apprehended by Secret Service agents.
“One of the names of his identity theft services was findget[.]me,” O’Neill said. “We took that seriously, and we did like he asked.”
This is Part I of a multi-part series. Check back tomorrow (Aug. 27) for Part II, which will examine what investigators learned following Ngo’s arrest, and delve into his more recent effort to right the wrongs he’s done.
from Krebs on Security https://ift.tt/2EE63YW
via IFTTT
Aunque todavía no se ha instaurado completamente en la mayoría de países, sabemos que la conectividad 5G es el futuro. De hecho, numerosos fabricantes se han subido al barco con sus nuevos smartphones.
Estos son los mejores móviles con 5G baratos que puedes comprar. Los hay para todos los gustos y bolsillos, desde potentes dispositivos que incorporan procesadores de gama alta a otros más modestos y económicos.
El Xiaomi Mi 10 Lite es uno de los móviles con 5G más baratos que puedes comprar. Nos presenta un bonito diseño y una buena pantalla AMOLED de 6,57 pulgadas.
El Snapdragon 765G es su cerebro, un buen procesador al que podrás exigirle mucho. Además, tendrás la posibilidad de tomar muy buenas fotografías con sus 4 cámaras traseras. No nos olvidamos de su batería, con 4.160 mAh y carga rápida.
Todo es pantalla en este POCO F2 Pro, que no necesita de notch ni agujero gracias su cámara pop-up. Llega con una gran pantalla AMOLED de 6,67 pulgadas y resolución Full HD+.
Bajo su chasis, uno de los procesadores más potentes que hemos probado, el Qualcomm Snapdragon 865. Podrás exigirle el máximo, hasta los juegos más potentes se mueven sin ningún problema. El terminal chino también incorpora una cuádruple cámara trasera y una batería de 4.700 mAh.
El Samsung Galaxy A51 llega con una nueva versión 5G que mantiene su panel Super AMOLED de 6,5 pulgadas y resolución Full HD+. Sin embargo, sube el nivel en potencia incorporando el Exynos 980.
El dispositivo de la firma coreana cuenta además con 4 cámaras en su trasera, una notable batería de 4.500 mAh, conectividad NFC y, por supuesto, radio FM.
Este Huawei P40 Lite 5G es la nueva edición del popular gama media chino. Cuenta con una pantalla IPS de 6,5 pulgadas y resolución Full HD+, además de un cuerpo que cambia ligeramente respecto al Huawei P40 Lite original.
Saber más: Estos son los móviles 5G más ligeros que puedes comprar ahora mismo
El móvil de Huawei incorpora el Kirin 820 –que cuenta con módem 5G– y una cuádruple cámara liderada por un sensor de 64 megapíxeles. Su batería, por otro lado, alcanza unos nada despreciables 4.000 mAh.
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
La entrada 4 móviles 5G baratos que puedes comprar ahora mismo se publicó primero en Andro4all.
from Andro4all https://ift.tt/3gEtL4Z
via IFTTT