You may have heard that today’s phone fraudsters like to use use caller ID spoofing services to make their scam calls seem more believable. But you probably didn’t know that these fraudsters also can use caller ID spoofing to trick your bank into giving up information about recent transactions on your account — data that can then be abused to make their phone scams more believable and expose you to additional forms of identity theft.
Last week, KrebsOnSecurity told the harrowing tale of a reader (a security expert, no less) who tried to turn the tables on his telephonic tormentors and failed spectacularly. In that episode, the people impersonating his bank not only spoofed the bank’s real phone number, but they were also pretending to be him in a separate call at the same time with his bank.
This foiled his efforts to make sure it was really his bank that called him, because he called his bank with another phone and the bank confirmed they currently were in a separate call with him discussing fraud on his account (however, the other call was the fraudster pretending to be him).
Shortly after that story ran, I heard from another reader — we’ll call him “Jim” since he didn’t want his real name used for this story — whose wife was the target of a similar scam, albeit with an important twist: The scammers were armed with information about a number of her recent financial transactions, which he claims they got from the bank’s own automated phone system just by spoofing her phone number.
“When they originally called my wife, there were no fraudulent transactions on her account, but they were able to specify the last three transactions she had made, which combined with the caller-ID had mistakenly earned her trust,” Jim explained. “After we figured out what was going on, we were left asking ourselves how the crooks had obtained her last three transactions without breaking into her account online. As it turned out, calling the phone number on the back of the credit card from the phone number linked with the card provided the most recent transactions without providing any form of authentication.”
Jim said he was so aghast at this realization that he called the same number from his phone and tried accessing his account, which is also at Citi but wholly separate from his spouse’s. Sure enough, he said, as long as he was calling from the number on file for his account, the automated system let him review recent transactions without any further authentication.
“I confirmed on my separate Citi card that they often (but not quite always) were providing the transaction details,” Jim said. “I was appalled that Citi would do that. So, it seemed the crooks would spoof caller ID when calling Citibank, as well as when calling the target/victim.”
The incident Jim described happened in late January 2020, and Citi may have changed its procedures since then. The company has not yet responded to requests for comment.
But in a phone interview with KrebsOnSecurity earlier this week, Jim made a call to Citi’s automated system from his mobile phone on file with the bank, and I could hear Citi’s systems asking him to enter the last four digits of his credit card number before he could review recent transactions.
The request for the last four of the customer’s credit card number was consistent with my own testing, which relied upon on a caller ID spoofing service advertised in the cybercrime underground and aimed at a Citi account controlled by this author.
In one test, the spoofed call let KrebsOnSecurity hear recent transaction data — where and when the transaction was made, and how much was spent — after providing the automated system the last four digits of the account’s credit card number. In another test, the automated system asked for the account holder’s full Social Security number.
PREGNANT PAUSES AND BULGING EMAIL BOMBS
Jim said the fraudster who called his wife clearly already knew her mailing and email addresses, her mobile number and the fact that her card was an American Airlines-branded Citi card. The caller said there had been a series of suspicious transactions, and proceeded to read back details of several recent transactions to verify if those were purchases she’d authorized.
A list of services offered by one of several underground stores that sell caller ID spoofing and email bombing services.
Jim’s wife quickly logged on to her Citi account and saw that the amounts, dates and places of the transactions referenced by the caller indeed corresponded to recent legitimate transactions. But she didn’t see any signs of unauthorized charges.
After verifying the recent legitimate transactions with the caller, the person on the phone asked for her security word. When she provided it, there was a long hold before the caller came back and said she’d provided the wrong answer.
When she corrected herself and provided a different security word, there was another long pause before the caller said the second answer she provided was correct. At that point, the caller said Citi would be sending her a new card and that it had prevented several phony charges from even posting to her account.
She didn’t understand until later that the pauses were points at which the fraudsters had to put her on hold to relay her answers in their own call posing as her to Citi’s customer service department.
Not long after Jim’s spouse hung up with the caller, her inbox quickly began filling up with hundreds of automated messages from various websites trying to confirm an email newsletter subscription she’d supposedly requested.
As the recipient of several of these “email bombing” attacks, I can verify that crooks often will use services offered in the cybercrime underground to flood a target’s inbox with these junk newsletter subscriptions shortly after committing fraud in the target’s name when they wish to bury an email notification from a target’s bank.
‘OVERPAYMENT REIMBURSEMENT’
In the case of Jim’s wife, the inbox flood backfired, and only made her more suspicious about the true nature of the recent phone call. So she called the number on the back of her Citi card and was told that she had indeed just called Citi and requested what’s known as an “overpayment reimbursement.” The couple have long had their credit cards on auto-payment, and the most recent payment was especially high — nearly $4,000 — thanks to a flurry of Christmas present purchases for friends and family.
In an overpayment reimbursement, a customer can request that the bank refund any amount paid toward a previous bill that exceeds the minimum required monthly payment. Doing so causes any back-due interest on that unpaid amount to accrue to the account as well.
In this case, the caller posing as Jim’s wife requested an overpayment reimbursement to the tune of just under $4,000. It’s not clear how or where the fraudsters intended this payment to be sent, but for whatever reason Citi ended up saying they would cut a physical check and mail it to the address on file. Probably not what the fraudsters wanted, although since then Jim and his wife say they have been on alert for anyone suspicious lurking near their mailbox.
“The person we spoke with at Citi’s fraud department kept insisting that yes, it was my wife that called because the call came from her mobile number,” Jim said. “The Citi employee was alarmed because she didn’t understand the whole notion of caller ID spoofing. And we both found it kind of disturbing that someone in fraud at such a major bank didn’t even understand that such a thing was possible.”
SHOPPING FOR ‘CVVs’
Fraud experts say the scammers behind the types of calls that targeted Jim’s family are most likely fueled by the rampant sale of credit card records stolen from hacked online merchants. This data, known as “CVVs” in the cybercrime underground, is sold in packages for about $15 per record, and very often includes the customer’s name, address, phone number, email address and full credit or debit card number, expiration date, and card verification value (CVV) printed on the back of the card.
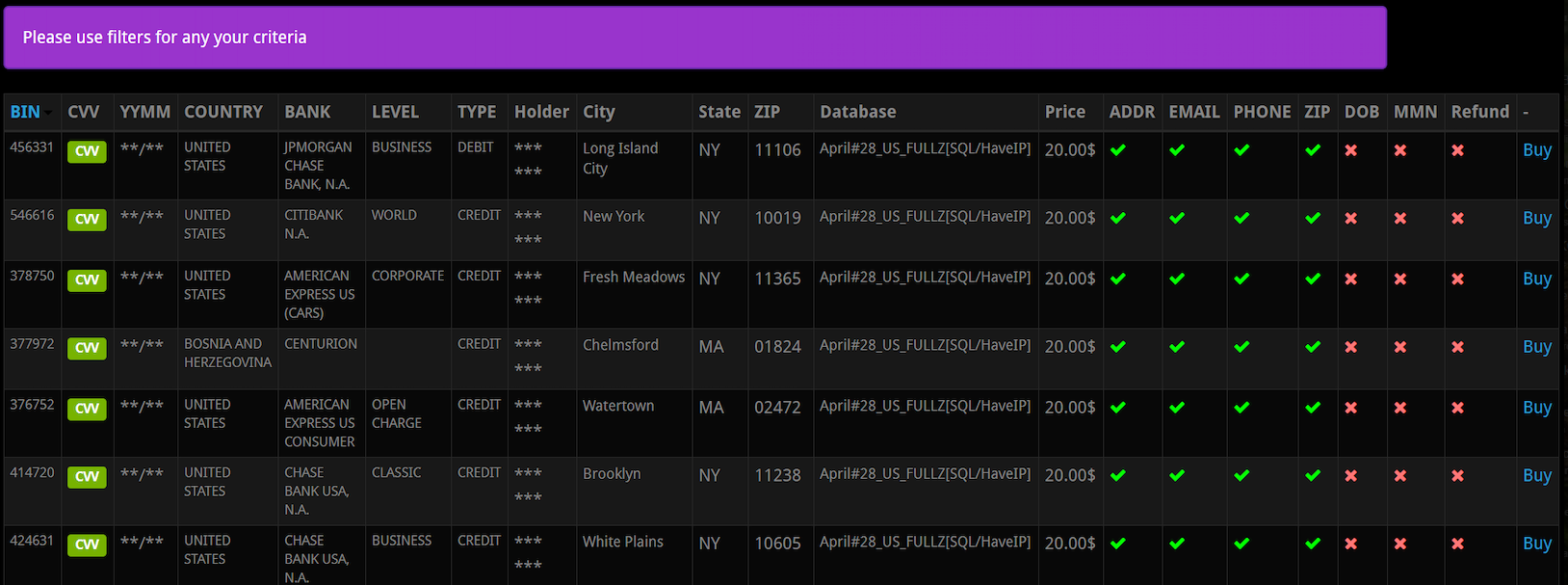
A screen shot from an underground store selling CVV records. Note that all of these records come with the cardholder’s address, email, phone number and zip code. Click to enlarge. Image: Gemini Advisory.
Dozens of cybercrime shops traffic in this stolen data, which is more traditionally used to defraud online merchants. But such records are ideally suited for criminals engaged in the type of phone scams that are the subject of this article.
That’s according to Andrei Barysevich, CEO and co-founder of Gemini Advisory, a New York-based company that monitors dozens of underground shops selling stolen card data.
“If the fraudsters already have the target’s cell phone number, in many cases they already have the target’s credit card information as well,” Barysevich said.
Gemini estimates there are currently some 13 million CVV records for sale across the dark web, and that more than 40 percent of these records put up for sale over the past year included the cardholder’s phone number.
Data from recent financial transactions can not only help fraudsters better impersonate your bank, it can also be useful in linking a customer’s account to another account the fraudsters control. That’s because PayPal and a number of other pure-play online financial institutions allow customers to link accounts by verifying the value of microdeposits.
For example, if you wish to be able to transfer funds between PayPal and a bank account, the company will first send a couple of tiny deposits — a few cents, usually — to the account you wish to link. Only after verifying those exact amounts will the account-linking request be granted.
JUST HANG UP
Both this and last week’s story illustrate why the only sane response to a call purporting to be from your bank is to hang up, look up your bank’s customer service number from their Web site or from the back of your card, and call them back yourself.
Meanwhile, fraudsters who hack peoples’ finances with nothing more than a telephone have been significantly upping the volume of attacks in recent months, new research suggests. Fraud prevention company Next Caller said this week it has tracked “massive increases in call volumes and high-risk calls across Fortune 500 companies as a result of COVID-19.”
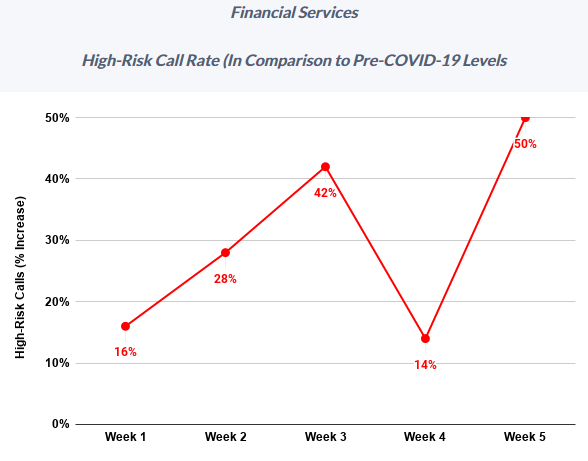
Image: Next Caller.
“After a brief reprieve in Week 4 (April 6-12), Week 5 (April 13-19) saw call volume across Next Caller’s clients in the telecom and financial services sectors spike 40% above previous highs,” the company found. “Particularly worrisome is the activity taking place in the financial services sector, where call traffic topped previous highs by 800%.”
Next Caller said it’s likely some of that increase was due to numerous online and mobile app outages for many major financial institutions at a time when more than 80 million Americans were simultaneously trying to track the status of their stimulus deposits. But it said that surge also brought with it an influx of fraudsters looking to capitalize on all the chaos.
“High-risk calls to financial services surged to 50% above pre-COVID levels, with one Fortune 100 bank suffering a high-risk increase of 60% during Week 5,” the company wrote in a recent report.
from Krebs on Security https://ift.tt/35evJ7L
via IFTTT