The industry’s fixation on complex exploits has come at the expense of making fundamentals easy and intuitive for end users.
from Dark Reading: https://ift.tt/3341hKS
via IFTTT

The industry’s fixation on complex exploits has come at the expense of making fundamentals easy and intuitive for end users.
from Dark Reading: https://ift.tt/3341hKS
via IFTTT
Huawei es la segunda marca de móviles Android, por detrás de Samsung, que domina con mano de hierro el mercado. Y la evolución de la marca china ha sido más que notable durante los últimos años. Y como consecuencia de esto, Su subempresa, honor, ha ido por el mismo camino, y lo cierto es que ahora mismo se trata de dos grandes exponentes en el mercado, independientemente de su gama.
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
La entrada Ofertas de Huawei en Amazon: desde el P30 hasta el Mate 20 rebajados se publicó primero en Andro4all.
from Andro4all https://ift.tt/37d5Be6
via IFTTT
National Veterinary Associates (NVA), a California company that owns more than 700 animal care facilities around the globe, is still working to recover from a ransomware attack late last month that affected more than half of those properties, separating many veterinary practices from their patient records, payment systems and practice management software. NVA says it expects to have all facilities fully back up and running normally within the next week.
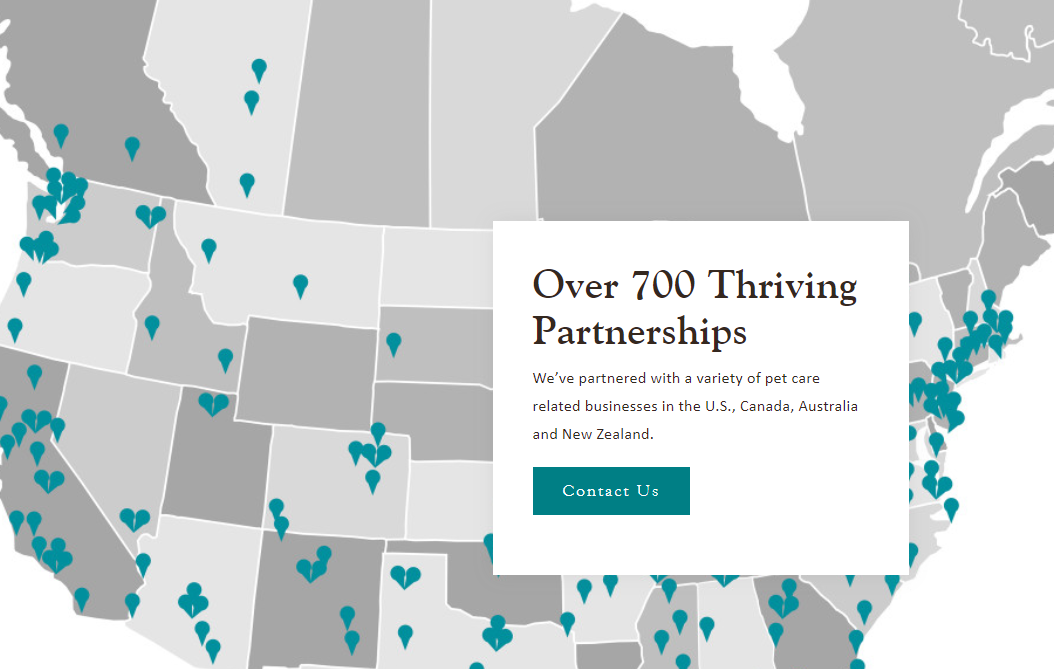
Agoura Hills, Calif.-based NVA bills itself as is the largest private owner of freestanding veterinary hospitals in the United States. The company’s Web site says it currently owns roughly 700 veterinary hospitals and animal boarding facilities in the United States, Canada, Australia and New Zealand.
NVA said it discovered the ransomware outbreak on the morning of Sunday, Oct. 27, and soon after hired two outside security firms to investigate and remediate the attack. A source close to the investigation told KrebsOnSecurity that NVA was hit with Ryuk, a ransomware strain first spotted in August 2018 that targets mostly large organizations for a high-ransom return.
NVA declined to answer questions about the malware, or whether the NVA paid the ransom demand.
“It was ransomware, but we’ve been referring to it as a malware incident,” said Laura Koester, NVA’s chief marketing officer.
Koester said because every NVA hospital runs their IT operations as they see fit, not all were affected. More importantly, she said, all of the NVA’s hospitals have remained open and able to see clients (animals in need of care), and access to patient records has been fully restored to all affected hospitals.
“For a few days, some [pet owners] couldn’t do online bookings, and some hospitals had to look at different records for their patients,” Koester said. “But throughout this whole thing, if there was a sick animal, we saw them. No one closed their doors.”
The source close to the investigation painted a slight less rosy picture of the situation at NVA, and said the company’s response has been complicated by the effects of wildfires surrounding its headquarters in Los Angeles County: A year ago, a destructive wildfire in Los Angeles and Ventura Counties burned almost 100,00 acres, destroyed more than 1,600 structures, killed three people and prompted the evacuation of nearly 300,000 people — including all residents of Agoura Hills.
“The support center was scheduled to be closed on Friday Oct 25, 2019 due to poor air quality caused by wildfires to the north,” said the source, who asked to remain anonymous. “Around 2 am PT [Oct. 27], the Ryuk virus was unleashed at NVA. Approximately 400 locations were infected. [Microsoft] Active Directory and Exchange servers were infected. Many of the infected locations immediately lost access to their Patient Information Management systems (PIMs). These locations were immediately unable to provide care.”
The source shared internal communications from different NVA executives to their hospitals about the extent of the remediation efforts and possible source of the compromise, which seemed to suggest that at least some NVA properties have been struggling to accommodate patients.
A missive from NVA’s Director of Operations Robert Hill on Oct. 30 acknowledged that “we continue to be faced with a monumental effort to restore IT service [to] nearly 400 of our hospitals.”
“This really hit home for me Saturday,” Hill wrote. “One of my best friends had to take his Yellow Lab into Conejo Valley for urgent care. Thankfully CV was able to provide care as their [systems] were up and running, but many of our hospitals are not in as good shape.”
In an update sent to NVA hospitals on Nov. 6, the company’s new head of technology Greg Hartmann said its security system successfully blocked the ransomware from infiltrating its systems — at least at first.
“Because of the scale of the attack, the virus eventually found three smaller points of entry through accounts that were unaffiliated with NVA, but unfortunately opened within our network,” Hartmann said. “Upon discovery of the incident, our technology team immediately implemented procedures to prevent the malware from spreading; however, many local systems were affected. Still, we have many hospitals whose systems are not recovered. The technology team continues to set up interim workstations at each affected hospital while they prepare to rebuild servers.”
The source told KrebsOnSecurity that NVA suffered a separate ransomware infestation earlier this summer that also involved Ryuk, and they expressed concern that the first incident may not have been fully remediated — potentially letting the attackers maintain a foothold within the organization.
“This is the second time this year Ryuk struck NVA,” the source said. “The first time, NVA was rather open to all facilities about what happened. This time, however, they are simply referring to it as a ‘system outage.’”
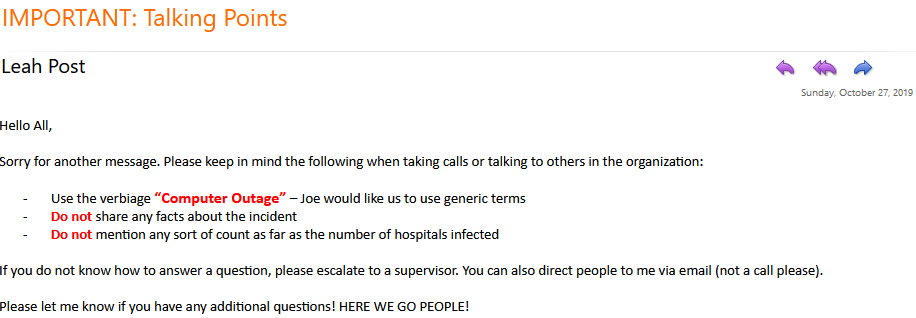
A set of talking points NVA distributed to staff on Oct. 27, the day some 400 veterinary hospitals were hit with the Ryuk ransomware.
Koester said some NVA facilities did get hit with a malware incident earlier this year, but that she did not believe ransomware was involved in that intrusion.
The Ryuk ransomware has made a name for itself going after businesses that supply services to other companies — particularly cloud-data firms — with the ransom demands set according to the victim’s perceived ability to pay. In February, payroll software provider Apex Human Capital Management chose to pay the ransom demand after a Ryuk infection severed payroll management services for hundreds of the company’s customers. And on Christmas Eve 2018, cloud hosting provider Dataresolution.net suffered a multi-week outage after a Ryuk attack.
According to a bulletin released by the FBI in May, cybercriminals had targeted over 100 U.S. and international businesses with Ryuk since August 2018. Security firm CrowdStrike estimated that attackers deploying Ryuk had netted over $3.7 million in bitcoin ransom payments between Aug. 2018 and January 2019.
Many people and organizations may be under the impression that ransomware attacks like Ryuk can appear at a moment’s notice merely from someone clicking a malicious link or opening a booby-trapped email attachment. While the latter appears to be the most common vector for ransomware infestations, an advisory released in September by the U.K’s National Cyber Security Centre suggests most Ryuk victims are compromised weeks or months before the ransomware is actually deployed inside the victim’s network.
“The Ryuk ransomware is often not observed until a period of time after the initial infection – ranging from days to months – which allows the actor time to carry out
reconnaissance inside an infected network, identifying and targeting critical network systems and therefore maximizing the impact of the attack,” reads the NCSC advisory, which includes tips on spotting signs of a Ryuk infection. “But it may also offer the potential to mitigate against a ransomware attack before it occurs, if the initial infection is detected and remedied.”
As for what changes NVA will be making to prevent yet another ransomware outbreak, an internal update on Nov. 7 from NVA’s chief information officer Joe Leggio said NVA was investing in software from Carbon Black, a cloud-based security solution that will be installed on all NVA property computers.
“Throughout my career, I have witnessed incredible advances in technology making our lives better,” Leggio wrote. “At nearly the same rate, the bad guys have been increasing the aggressiveness and sophistication of their attacks. As we rebuild, we are also thinking of the future. That is why we are investing in cybersecurity talent, new infrastructure, and better software.”
from Krebs on Security https://ift.tt/2QuMBSx
via IFTTT

Los teléfonos plegables han sido los más destacados este año, aunque por el momento tan solo el Samsung Galaxy Fold se encuentra a la venta. El próximo curso aterrizarán en el mercado el Huawei Mate X y el Motorola Razr, y se espera que otros fabricantes sigan por el mismo camino. Ante su desembarco, un estudio apunta que los móviles plegables interesan a los usuarios, que ven algo excesivos sus
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
La entrada Los móviles plegables interesan… pero no sus precios se publicó primero en Andro4all.
from Andro4all https://ift.tt/2CZTFhS
via IFTTT
El Black Friday, una de las fechas más señaladas del año, está a la vuelta de la esquina. Se celebrará el próximo viernes 29 de noviembre y tanto internet como los comercios tradicionales se llenarán de todo tipo de ofertas y atractivos descuentos. Sin embargo, no hace falta esperar hasta el día 29, las mejores ofertas ya están disponibles. Hoy te traemos los descuentos más atractivos que hemos encontrado en
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
La entrada El Black Friday se adelanta en El Corte Inglés con estos móviles en oferta se publicó primero en Andro4all.
from Andro4all https://ift.tt/2Om2Iz6
via IFTTT
If you think brand new, just-out-of-the-box Android smartphones are immune from security vulnerabilities – think again.
from Naked Security https://ift.tt/2rbPm0f
via IFTTT

Hace escasos minutos hemos publicado un artículo en el que decíamos que no existe el software perfecto. Y es que navegadores como Chrome, Edge o Safari son “fáciles” de hackear. En el artículo, decíamos que el software es imperfecto, y lo es tanto en programas/apps como en sistemas operativos, pero se hablaba de vulnerabilidades encontradas en programas. Ahora nos toca hacer lo mismo, pero sobre sistemas operativos: se ha descubierto un nuevo malware que afecta a Linux y Windows y su nombre es ACBackdoor.
Tal y como ha informado Bleeping Computer, investigadores de seguridad han descubierto un nuevo backdoor multiplataforma que afecta sistemas operativos Windows y Linux. Este malware podría ser usado para ejecutar código malicioso y binarios en los equipos comprometidos. Por lo que parece, está desarrollado por un grupo con experiencia en desarrollar herramientas maliciosas para Linux, todo según palabras de Ignacio Sanmillan de Intenzer.
(adsbygoogle = window.adsbygoogle || []).push({});
Hay dos variantes y las dos comparten el mismo servidor de órdenes y control (C2). Las vías de infección que usan son diferentes: la versión de Windows se está promoviendo mediante publicidad maliciosa con la ayuda del Fallout Exploit Kit, mientras que la carga útil de Linux se deja caer a través de un sistema de entrega aún desconocido.
La última versión del malware tiene como objetivo las vulnerabilidades CVE-2018-15982, relacionada con Flash Player, y la CVE-2018-8174, relacionada con el motor VBScript de Internet explorer. En ambos casos, la intención es infectar a los visitantes de páginas web controladas por el atacante. Podríamos decir que, aunque insistimos en que no existe el software perfecto, en el caso de Flash Player llueve sobre mojado.
Lo más extraño, o digamos menos habitual, es que la versión de Windows no representa una amenaza compleja. La versión de ACBackdoor de Windows es un “port” de la de Linux:
(adsbygoogle = window.adsbygoogle || []).push({});
El implante de Linux se ha escrito notablemente mejor que el implante de Windows, destacando la implementación del mecanismo de persistencia junto con los diferentes comandos de puerta trasera y características adicionales que no se ven en la versión de Windows, como la creación de procesos independientes y el cambio de nombre de procesos.
Después de infectar un ordenador, el malware empezará a recoger información del sistema, lo que incluye su arquitectura y dirección MAC. Para conseguirlo, usa herramientas específicas de la plataforma, con funciones Windows API en Windows y el programa uname UNIX usado comúnmente para imprimir información del sistema en Linux. Una vez termina con las tareas de recolección de información, ACBackdoor añadirá una entrada en el registro de Windows y creará varios enlaces simbólicos, mientras que en Linux creará un script initrd para conseguir persistencia y lanzarse automáticamente en cada reinicio.
En Windows, el backdoor también intentará camuflarse como un proceso MsMpEng.exe, la utilidad antimalware y spyware Windows Defender de Microsoft. En Linux se camuflará emulando la utilidad de notificaciones de nuevas actualizaciones (UpdateNotifier) de Ubuntu y renombrará su proceso como [kworker/u8:7-ev], lo que está relacionado con el kernel de Linux.
Para comunicarse con el servidor C2, ambas variantes del malware usan HTTPS como canal de comunicación, enviando toda la información recogida como una carga codificada BASE64. Por otra parte, ACBackdoor puede recibir información, ejecutar y actualizar comandos desde dicho servidor C2, lo que permite a sus dueños ejecutar comandos de Shell, binarios y actualizar el malware ya presente en un sistema infectado.
La mejor manera de evitar este y otros problemas con software malicioso es el sentido común. Lo primero es no visitar páginas webs de dudosa procedencia, algo a lo que ayuda un navegador moderno que nos avisa si una web es/puede ser peligrosa. Por otra parte, y esto vale para cualquier sistema operativo, merece la pena tener siempre bien actualizado el software que estamos usando. No existe el software perfecto, lo que incluye los sistemas operativos, y ACBackdoor es la última prueba de ello.
from Linux Adictos https://ift.tt/2CTzaUf
via IFTTT
El Realme X2 Pro es uno de los nuevos terminales de la compañía china que han llegado ha España, y que parece que vienen a ponerle las cosas difíciles a Xiaomi en el segmento de la gama media y de la gama alta barata. Y todo en base a lo de siempre: una excepcional relación calidad-precio. Hoy, vamos a enseñarte dónde puedes comprar el Realme X2 Pro rebajado a menos
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
La entrada El Realme X2 Pro a precio mínimo por tiempo limitado se publicó primero en Andro4all.
from Andro4all https://ift.tt/341J0PP
via IFTTT
Beware, holiday shoppers! The phishers hiding under typosquatting domains are waiting for your keyboard fumbles.
from Naked Security https://ift.tt/2QIewi7
via IFTTT