For at least the past decade, a computer crook variously known as “Yalishanda,” “Downlow” and “Stas_vl” has run one of the most popular “bulletproof” Web hosting services catering to a vast array of phishing sites, cybercrime forums and malware download servers. What follows are a series of clues that point to the likely real-life identity of a Russian man who appears responsible for enabling a ridiculous amount of cybercriminal activity on the Internet today.

Image: Intel471
KrebsOnSecurity began this research after reading a new academic paper on the challenges involved in dismantling or disrupting bulletproof hosting services, which are so called because they can be depended upon to ignore abuse complaints and subpoenas from law enforcement organizations. We’ll get to that paper in a moment, but for now I mention it because it prompted me to check and see if one of the more infamous bulletproof hosters from a decade ago was still in operation.
Sure enough, I found that Yalishanda was actively advertising on cybercrime forums, and that his infrastructure was being used to host hundreds of dodgy sites. Those include a large number of cybercrime forums and stolen credit card shops, ransomware download sites, Magecart-related infrastructure, and a metric boatload of phishing Web sites mimicking dozens of retailers, banks and various government Web site portals.
I first encountered Yalishanda back in 2010, after writing about “Fizot,” the nickname used by another miscreant who helped customers anonymize their cybercrime traffic by routing it through a global network of Microsoft Windows computers infected with a powerful malware strain called TDSS.
After that Fizot story got picked up internationally, KrebsOnSecurity heard from a source who suggested that Yalishanda and Fizot shared some of the same infrastructure.
In particular, the source pointed to a domain that was live at the time called mo0be-world[.]com, which was registered in 2010 to an Aleksandr Volosovyk at the email address stas_vl@mail.ru. Now, normally cybercriminals are not in the habit of using their real names in domain name registration records, particularly domains that are to be used for illegal or nefarious purposes. But for whatever reason, that is exactly what Mr. Volosovyk appears to have done.
WHO IS YALISHANDA?
The one or two domain names registered to Aleksandr Volosovyk and that mail.ru address state that he resides in Vladivostok, which is a major Pacific port city in Russia that is close to the borders with China and North Korea. The nickname Yalishanda means “Alexander” in Mandarin (亚历山大).
Here’s a snippet from one of Yalishanda’s advertisements to a cybercrime forum in 2011, when he was running a bulletproof service under the domain real-hosting[.]biz:
-Based in Asia and Europe.
-It is allowed to host: ordinary sites, doorway pages, satellites, codecs, adware, tds, warez, pharma, spyware, exploits, zeus, IRC, etc.
-Passive SPAM is allowed (you can spam sites that are hosted by us).
-Web spam is allowed (Hrumer, A-Poster ….)-Forbidden: Any outgoing Email spam, DP, porn, phishing (exclude phishing email, social networks)
There is a server with instant activation under botnets (zeus) and so on. The prices will pleasantly please you! The price depends on the specific content!!!!
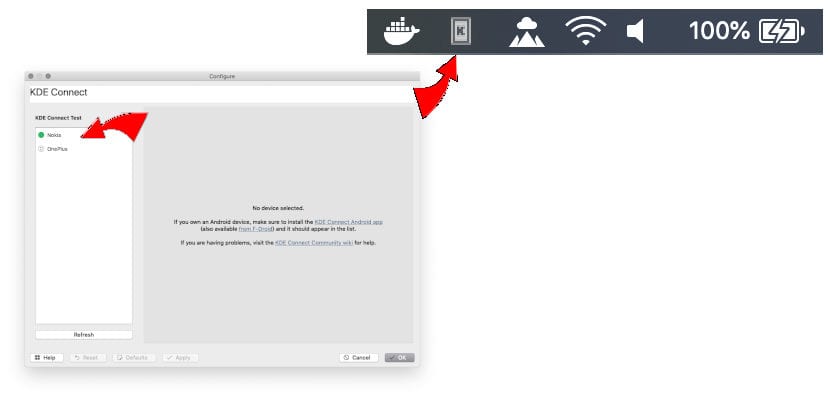
Yalishanda would re-brand and market his pricey bulletproof hosting services under a variety of nicknames and cybercrime forums over the years, including one particularly long-lived abuse-friendly project aptly named abushost[.]ru.
In a talk given at the Black Hat security conference in 2017, researchers from cyber intelligence firm Intel471 labeled Yalishanda as one the “top tier” bulletproof hosting providers worldwide, noting that in just one 90-day period in 2017 his infrastructure was seen hosting sites tied to some of the most advanced malware contagions at the time, including the Dridex and Zeus banking trojans, as well as a slew of ransomware operations.
“Any of the actors that can afford his services are somewhat more sophisticated than say the bottom feeders that make up the majority of the actors in the underground,” said Jason Passwaters, Intel471’s chief operating officer. “Bulletproof hosting is probably the biggest enabling service that you find in the underground. If there’s any one group operation or actor that touches more cybercriminals, it’s the bulletproof hosters.”
Passwaters told Black Hat attendees that Intel471 wasn’t convinced Alex was Yalishanda’s real name. I circled back with Intel471 this week to ask about their ongoing research into this individual, and they confided that they knew at the time Yalishanda was in fact Alexander Volosovyk, but simply didn’t want to state his real name in a public setting.
KrebsOnSecurity uncovered strong evidence to support a similar conclusion. In 2010, this author received a massive data dump from a source that had hacked into or otherwise absconded with more than four years of email records from ChronoPay — at the time a major Russian online payment provider whose CEO and co-founders were the chief subjects of my 2014 book, Spam Nation: The Inside Story of Organized Cybercrime.
Querying those records on Yalishanda’s primary email address — stas_vl@mail.ru — reveal that this individual in 2010 sought payment processing services from ChronoPay for a business he was running which sold counterfeit designer watches.
As part of his application for service, the person using that email address forwarded six documents to ChronoPay managers, including business incorporation and banking records for companies he owned in China, as well as a full scan of his Russian passport.
That passport, pictured below, indicates that Yalishanda’s real name is Alexander Alexandrovich Volosovik. The document shows he was born in Ukraine and is approximately 36 years old.

The passport for Alexander Volosovyk, a.k.a. “Yalishandra,” a major operator of bulletproof hosting services.
According to Intel471, Yalishanda lived in Beijing prior to establishing a residence in Vladivostok (that passport above was issued by the Russian embassy in Beijing). The company says he moved to St. Petersburg, Russia approximately 18 months ago.
His current bulletproof hosting service is called Media Land LLC. This finding is supported by documents maintained by Rusprofile.ru, which states that an Alexander Volosovik is indeed the director of a St. Petersburg company by the same name.
ARMOR-PIERCING BULLETS?
Bulletproof hosting administrators operating from within Russia probably are not going to get taken down or arrested, provided they remain within that country (or perhaps within the confines of the former republics of the Soviet Union, known as the Commonwealth of Independent States).
That’s doubly so for bulletproof operators who are careful to follow the letter of the law in those regions — i.e., setting up official companies that are required to report semi-regularly on various aspects of their business, as Mr. Volosovik clearly has done.
However, occasionally big-time bulletproof hosters from those CIS countries do get disrupted and/or apprehended. On July 11, law enforcement officials in Ukraine announced they’d conducted 29 searches and detained two individuals in connection with a sprawling bulletproof hosting operation.
The press release from the Ukrainian prosecutor general’s office doesn’t name the individuals arrested, but sources tell KrebsOnSecurity that one of them was Mikhail Rytikov, a man U.S. authorities say was a well-known bulletproof hoster who operated under the nickname “AbdAllah.”

Servers allegedly tied to AbdAllah’s bulletproof hosting network. Image: Gp.gov.ua.
In 2015, the U.S. Justice Department named Rytikov as a key infrastructure provider for two Russian hackers — Vladimir Drinkman and Alexandr Kalinin — in a cybercrime spree the government called the largest known data breach at the time.
According to the Justice Department, Drinkman and his co-defendants were responsible for hacks and digital intrusions against NASDAQ, 7-Eleven, Carrefour, JCP, Hannaford, Heartland, Wet Seal, Commidea, Dexia, JetBlue, Dow Jones, Euronet, Visa Jordan, Global Payment, Diners Singapore and Ingenicard.
Whether AbdAllah ever really faces justice for his alleged crimes remains to be seen. Ukraine does not extradite citizens, as the U.S. authorities have requested in this case. And we have seen time and again how major cybercriminals get raided and detained by local and federal authorities there, only to quickly re-emerge and resume operations shortly thereafter, while the prosecution against them goes nowhere.
Some examples of this include several Ukrainian men arrested in 2010 and accused of running an international crime and money laundering syndicate that used a custom version of the Zeus trojan to siphon tens of millions of dollars from hacked small businesses in the U.S. and Europe. To my knowledge, none of the Ukrainian men that formed the core of that operation were ever prosecuted, reportedly because they were connected to influential figures in the Ukrainian government and law enforcement.
Intel471’s Passwater said something similar happened in December 2016, when authorities in the U.S., U.K. and Europe dismantled Avalanche, a distributed, cloud-hosting network that was rented out as a bulletproof hosting enterprise for countless malware and phishing attacks.
Prior to that takedown, Passwater said, somehow the core actor behind the Avalanche hosting network — an individual who went by the nickname “Sosweet” — got a tip about an impending raid.
“Sosweet was raided in December right before Avalanche was taken down, [and] we know that he was tipped off because of corruption [because] 24 hours later the guy was back in service and has all his stuff back up,” Passwater said.
The same also appears to be true for several Ukrainian men arrested in 2011 on suspicion of building and disseminating Conficker, a malware strain that infected millions of computers worldwide and prompted an unprecedented global response from the security industry.
So if a majority of bulletproof hosting businesses operate primarily out of countries where the rule of law is not strong and/or where corruption is endemic, is there any hope for disrupting these dodgy businesses?
Here we come full circle to the academic report mentioned briefly at the top of this story: The answer seems to be — like most things related to cybercrime — “maybe,” provided the focus is on attempting to interfere with their ability to profit from such activities.
That paper, titled Platforms in Everything: Analyzing Ground-Truth Data on the Anatomy and Economics of Bulletproof Hosting, was authored by researchers at New York University, Delft University of Technology, King Saud University and the Dutch National High-Tech Crimes Unit. Unfortunately, it has not yet been released publicly, and KrebsOnSecurity does not have permission yet to publish it.
The study examined the day-to-day operations of MaxiDed, a bulletproof hosting operation based in The Netherlands that was dismantled last summer after authorities seized its servers. The paper’s core findings suggest that because profit margins for bulletproof hosting (BPH) operations are generally very thin, even tiny disruptions can quickly push these businesses into the red.
“We demonstrate the BPH landscape to have further shifted from agile resellers towards marketplace platforms with an oversupply of resources originating from hundreds of legitimate upstream hosting providers,” the researchers wrote. “We find the BPH provider to have few choke points in the supply chain amenable to intervention, though profit margins are very slim, so even a marginal increase in operating costs might already have repercussions that render the business unsustainable.”
from Krebs on Security https://ift.tt/2lJZpqP
via IFTTT

 En cuanto a un “ecosistema”, abro paraguas, creo que el mejor es el de Apple. La manera en la que se comunican su iPhone, iPad, Mac, Apple Watch, Apple TV y Homepod no tiene rival. Pero esto tiene un problema más que evidente: todos los dispositivos del ecosistema tienen que ser de la manzana. En Linux existe KDE Connect que, aunque es diferente, nos permite conectar nuestro teléfono Android con nuestro ordenador. Siempre ha sido compatible con Linux, más tarde lo fue (sigue en desarrollo) con Windows y ahora también es compatible con macOS.
En cuanto a un “ecosistema”, abro paraguas, creo que el mejor es el de Apple. La manera en la que se comunican su iPhone, iPad, Mac, Apple Watch, Apple TV y Homepod no tiene rival. Pero esto tiene un problema más que evidente: todos los dispositivos del ecosistema tienen que ser de la manzana. En Linux existe KDE Connect que, aunque es diferente, nos permite conectar nuestro teléfono Android con nuestro ordenador. Siempre ha sido compatible con Linux, más tarde lo fue (sigue en desarrollo) con Windows y ahora también es compatible con macOS.