ZOC Terminal v7.23.4 – ‘Private key file’ Denial of Service (PoC)
from Exploit-DB.com RSS Feed http://bit.ly/2YGV5qH
via IFTTT

ZOC Terminal v7.23.4 – ‘Private key file’ Denial of Service (PoC)
from Exploit-DB.com RSS Feed http://bit.ly/2YGV5qH
via IFTTT
ZOC Terminal 7.23.4 – ‘Script’ Denial of Service (PoC)
from Exploit-DB.com RSS Feed http://bit.ly/2HoDrBZ
via IFTTT
JetAudio jetCast Server 2.0 – ‘Log Directory’ Local SEH Alphanumeric Encoded Buffer Overflow
from Exploit-DB.com RSS Feed http://bit.ly/2Yy825V
via IFTTT
WeChat for Android 7.0.4 – ‘vcodec2_hls_filter’ Denial of Service
from Exploit-DB.com RSS Feed http://bit.ly/30tcgO4
via IFTTT
DeepSound 1.0.4 – SQL Injection
from Exploit-DB.com RSS Feed http://bit.ly/2YBcdhs
via IFTTT
VMware Workstation 15.1.0 – DLL Hijacking
from Exploit-DB.com RSS Feed http://bit.ly/2HnUPH3
via IFTTT
Ogusers[.]com — a forum popular among people involved in hijacking online accounts and conducting SIM swapping attacks to seize control over victims’ phone numbers — has itself been hacked, exposing the email addresses, hashed passwords, IP addresses and private messages for nearly 113,000 forum users.
On May 12, the administrator of OGusers explained an outage to forum members by saying a hard drive failure had erased several months’ worth of private messages, forum posts and prestige points, and that he’d restored a backup from January 2019. Little did the administrators of OGusers know at the time, but that May 12 incident coincided with the theft of the forum’s user database, and the wiping of forum hard drives.
On May 16, the administrator of rival hacking community RaidForums announced he’d uploaded the OGusers database for anyone to download for free.
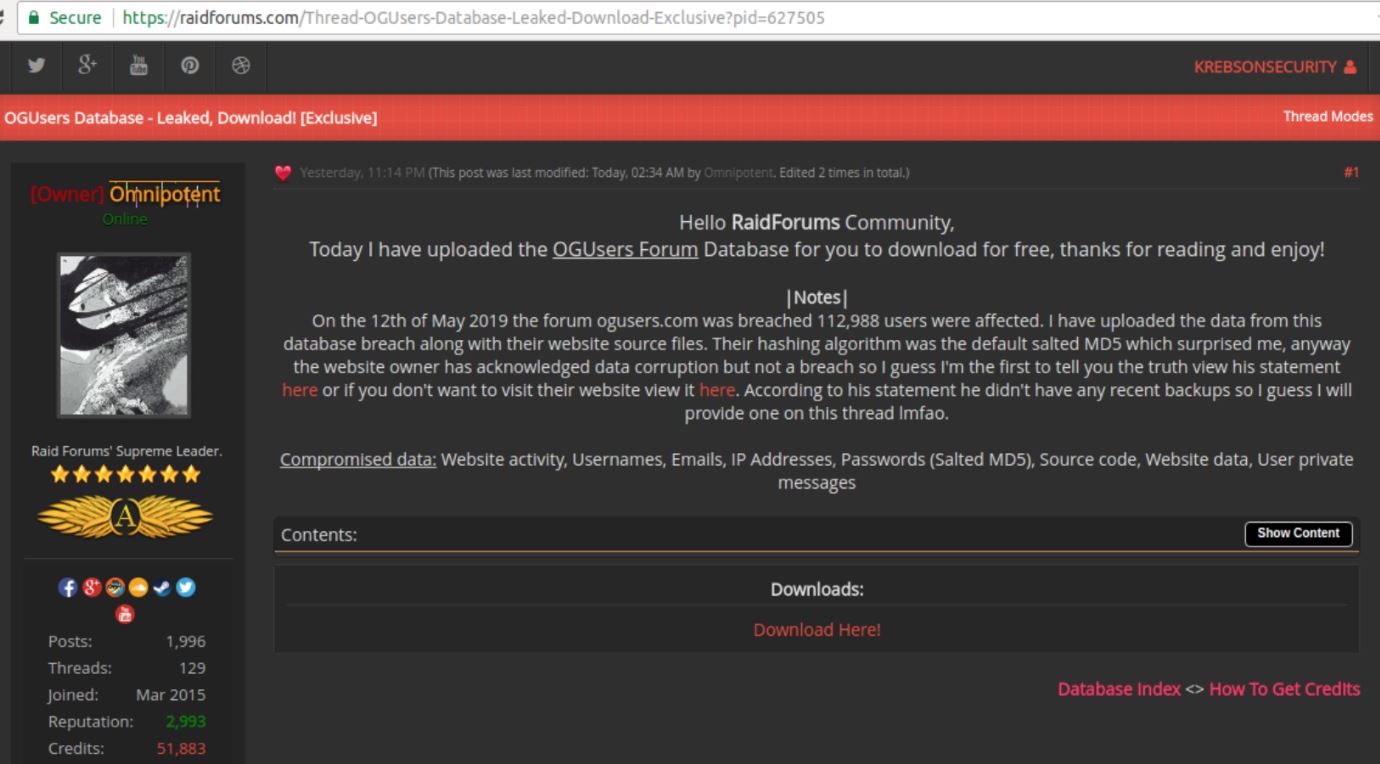
The administrator of the hacking community Raidforums on May 16 posted the database of passwords, email addresses, IP addresses and private messages of more than 113,000 users of Ogusers[.]com.
“On the 12th of May 2019 the forum ogusers.com was breached [and] 112,988 users were affected,” the message from RaidForums administrator Omnipotent reads. “I have uploaded the data from this database breach along with their website source files. Their hashing algorithm was the default salted MD5 which surprised me, anyway the website owner has acknowledged data corruption but not a breach so I guess I’m the first to tell you the truth. According to his statement he didn’t have any recent backups so I guess I will provide one on this thread lmfao.”
The database, a copy of which was obtained by KrebsOnSecurity, appears to hold the usernames, email addresses, hashed passwords, private messages and IP address at the time of registration for approximately 113,000 users (although many of these nicknames are likely the same people using different aliases).
The publication of the OGuser database has caused much consternation and drama for many in the community, which has become infamous for attracting people involved in hijacking phone numbers as a method of taking over the victim’s social media, email and financial accounts, and then reselling that access for hundreds or thousands of dollars to others on the forum.
Several threads on OGusers quickly were filled with responses from anxious users concerned about being exposed by the breach. Some complained they were already receiving phishing emails targeting their OGusers accounts and email addresses. 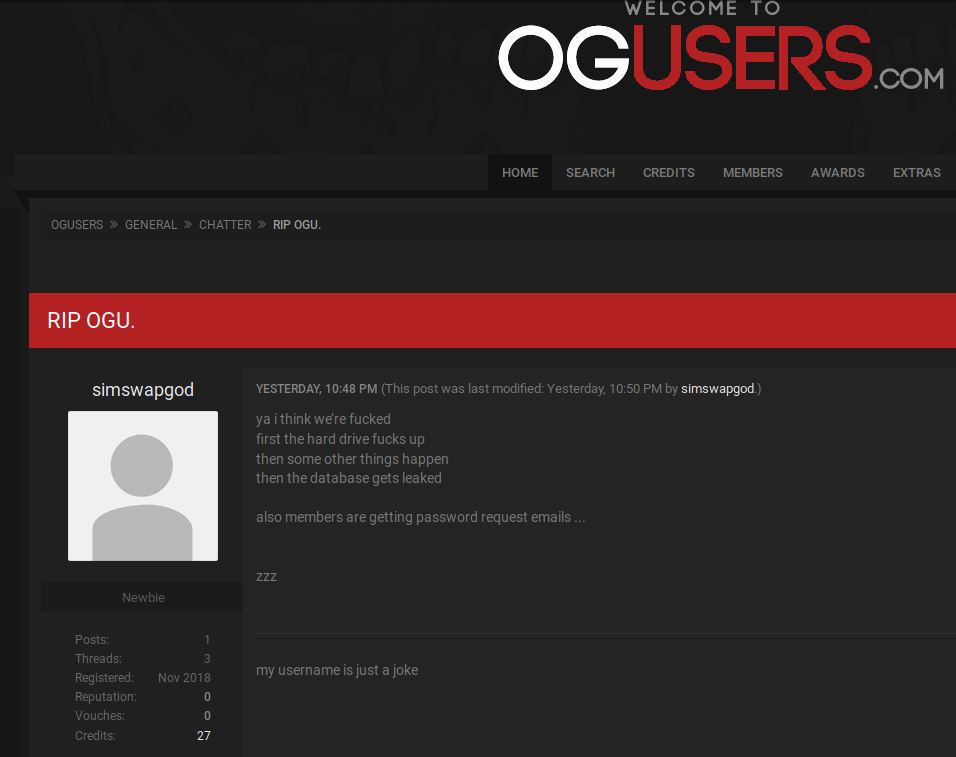
Meanwhile, the official Discord chat channel for OGusers has been flooded with complaints and expressions of disbelief at the hack. Members vented their anger at the main forum administrator, who uses the nickname “Ace,” claiming he altered the forum functionality after the hack to prevent users from removing their accounts. One user on the Discord chat summed it up:
“Ace be like:
-not replace broken hard drives, causing the site to time warp back four months
– not secure website, causing user info to be leaked
– disable selfban so people can’t leave”
It’s difficult not to admit feeling a bit of schadenfreude in response to this event. It’s gratifying to see such a comeuppance for a community that has largely specialized in hacking others. Also, federal and state law enforcement investigators going after SIM swappers are likely to have a field day with this database, and my guess is this leak will fuel even more arrests and charges for those involved.
from Krebs on Security http://bit.ly/2JMEyx6
via IFTTT
OnePlus dio a conocer su nuevo buque insignia hace unos días, el OnePlus 7 Pro que en Andro4all ya hemos analizado. Un teléfono inteligente que se presentó de forma oficial en un evento junto con el OnePlus 7 y los auriculares Bullet Wireless 2 de la firma. Ahora se ha dado a conocer que OnePlus cambia a Emily Ratajkowski por Robert Downey Jr. para promocionar su último terminal. Como informan
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
from Andro4all http://bit.ly/2WPTn5N
via IFTTT
Planificar tus viajes utilizando tu móvil es una tarea muy sencilla gracias a Google Trips, la app que la Gran G lanzó en español en septiembre de 2016. Utilizando la información de tu Gmail, Trips te informa sobre los viajes que vas a realizar en las próximas fechas y te permite organizarlos con sus múltiples funciones. La app de viajes de Google comenzó su andadura siendo bastante básica, pero la
Entra en Andro4all para leer el artículo completo
Puedes unirte a nosotros en Twitter, Facebook o en Google+
¡Suscríbete a nuestro canal de YouTube!
Publicado recientemente en Andro4all
from Andro4all http://bit.ly/2Ee2Uw0
via IFTTT
Newly famous after challenging Muhammad Ali for a championship title, boxer Chuck Wepner spirals down the slippery slope of being a celebrity.
from New On Netflix USA http://bit.ly/2VNm7zi
via IFTTT