The United Parcel Service (UPS) says fraudsters have been harvesting phone numbers and other information from its online shipment tracking tool in Canada to send highly targeted SMS phishing (a.k.a. “smishing”) messages that spoofed UPS and other top brands. The missives addressed recipients by name, included details about recent orders, and warned that those orders wouldn’t be shipped unless the customer paid an added delivery fee.
In a snail mail letter sent this month to Canadian customers, UPS Canada Ltd. said it is aware that some package recipients have received fraudulent text messages demanding payment before a package can be delivered, and that it has been working with partners in its delivery chain to try to understand how the fraud was occurring.

The recent letter from UPS about SMS phishers harvesting shipment details and phone numbers from its website.
“During that review, UPS discovered a method by which a person who searched for a particular package or misused a package look-up tool could obtain more information about the delivery, potentially including a recipient’s phone number,” the letter reads. “Because this information could be misused by third parties, including potentially in a smishing scheme, UPS has taken steps to limit access to that information.”
The written notice goes on to say UPS believes the data exposure “affected packages for a small group of shippers and some of their customers from February 1, 2022 to April 24, 2023.”
As early as April 2022, KrebsOnSecurity began receiving tips from Canadian readers who were puzzling over why they’d just received one of these SMS phishing messages that referenced information from a recent order they’d legitimately placed at an online retailer.
In March, 2023, a reader named Dylan from British Columbia wrote in to say he’d received one of these shipping fee scam messages not long after placing an order to buy gobs of building blocks directly from Lego.com. The message included his full name, phone number, and postal code, and urged him to click a link to mydeliveryfee-ups[.]info and pay a $1.55 delivery fee that was supposedly required to deliver his Legos.
“From searching the text of this phishing message, I can see that a lot of people have experienced this scam, which is more convincing because of the information the phishing text contains,” Dylan wrote. “It seems likely to me that UPS is leaking information somehow about upcoming deliveries.”
Josh is a reader who works for a company that ships products to Canada, and in early January 2023 he inquired whether there was any information about a breach at UPS Canada.
“We’ve seen many of our customers targeted with a fraudulent UPS text message scheme after placing an order,” Josh said. “A link is provided (often only after the customer responds to the text) which takes you to a captcha page, followed by a fraudulent payment collection page.”
Pivoting on the domain in the smishing message sent to Dylan shows the phishing domain shared an Internet host in Russia [91.215.85-166] with nearly two dozen other smishing related domains, including upsdelivery[.]info, legodelivery[.]info, adidascanadaltd[.]com, crocscanadafee[.]info, refw0234apple[.]info, vista-printcanada[.]info and telus-ca[.]info.
The inclusion of big-name brands in the domains of these UPS smishing campaigns suggests the perpetrators had the ability to focus their lookups on UPS customers who had recently ordered items from specific companies.
Attempts to visit these domains with a web browser failed, but loading them in a mobile device (or in my case, emulating a mobile device using a virtual machine and Developer Tools in Firefox) revealed the first stage of this smishing attack. As Josh mentioned, what first popped up was a CAPTCHA; after the visitor solved the CAPTCHA, they were taken through several more pages that requested the user’s full name, date of birth, credit card number, address, email and phone number.
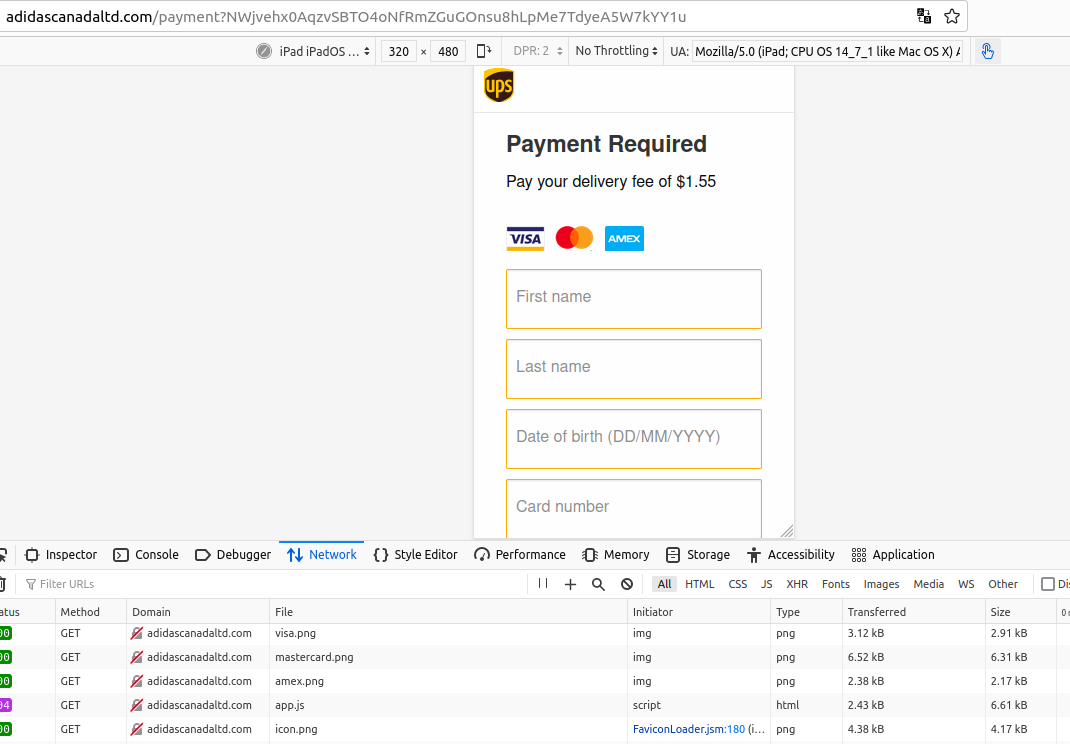
A smishing website targeting Canadians who recently purchased from Adidas online. The site would only load in a mobile browser.
In April 2022, KrebsOnSecurity heard from Alex, the CEO of a technology company in Canada who asked to leave his last name out of this story. Alex reached out when he began receiving the smishing messages almost immediately after ordering two sets of Airpods directly from Apple’s website.
What puzzled Alex most was that he’d instructed Apple to send the Airpods as a gift to two different people, and less than 24 hours later the phone number he uses for his Apple account received two of the phishing messages, both of which contained salutations that included the names of the people for whom he’d bought Airpods.
“I’d put the recipient as different people on my team, but because it was my phone number on both orders I was the one getting the texts,” Alex explained. “That same day, I got text messages referring to me as two different people, neither of whom were me.”
Alex said he believes UPS Canada either doesn’t fully understand what happened yet, or it is being coy about what it knows. He said the wording of UPS’s response misleadingly suggests the smishing attacks were somehow the result of hackers randomly looking up package information via the company’s tracking website.
Alex said it’s likely that whoever is responsible figured out how to query the UPS Canada website for only pending orders from specific brands, perhaps by exploiting some type of application programming interface (API) that UPS Canada makes or made available to its biggest retail partners.
“It wasn’t like I put the order through [on Apple.ca] and some days or weeks later I got a targeted smishing attack,” he said. “It was more or less the same day. And it was as if [the phishers] were being notified the order existed.”
The letter to UPS Canada customers does not mention whether any other customers in North America were affected, and it remains unclear whether any UPS customers outside of Canada may have been targeted.
In a statement provided to KrebsOnSecurity, Sandy Springs, Ga. based UPS [NYSE:UPS] said the company has been working with partners in the delivery chain to understand how that fraud was being perpetrated, as well as with law enforcement and third-party experts to identify the cause of this scheme and to put a stop to it.
“Law enforcement has indicated that there has been an increase in smishing impacting a number of shippers and many different industries,” reads an email from Brian Hughes, director of financial and strategy communications at UPS.
“Out of an abundance of caution, UPS is sending privacy incident notification letters to individuals in Canada whose information may have been impacted,” Hughes said. “We encourage our customers and general consumers to learn about the ways they can stay protected against attempts like this by visiting the UPS Fight Fraud website.”
from Krebs on Security https://ift.tt/9U1mZKV
via IFTTT