Valentina is a young pianist starting over. Her neighbor David is an inventor who hates noise. And a paper-thin wall is about to become their matchmaker.
from New On Netflix USA https://ift.tt/GQB5EYp
via IFTTT

Valentina is a young pianist starting over. Her neighbor David is an inventor who hates noise. And a paper-thin wall is about to become their matchmaker.
from New On Netflix USA https://ift.tt/GQB5EYp
via IFTTT
A young woman from Sweden’s Indigenous Sámi community tracks down a killer to settle a personal score in this emotional drama inspired by real events.
from New On Netflix USA https://ift.tt/AseuFic
via IFTTT
Refusing treatment for her cancer, a woman goes on a road trip across Tasmania to check off items on her bucket list with her husband and best friend.
from New On Netflix USA https://ift.tt/bwlheWn
via IFTTT
A humble singer’s brash lyrics ignite fame and fury across Punjab as he grapples with soaring success and brutal criticism before his untimely death.
from New On Netflix USA https://ift.tt/qlwhkSb
via IFTTT

By Cade Metz
This year’s honor will go to Avi Wigderson, an Israeli-born mathematician and theoretical computer scientist who specializes in randomness.
Published: April 10, 2024 at 06:00PM
from NYT Technology https://ift.tt/9UsRSnd
via IFTTT
From dog beds to pup backpacks, we’ve had our furry best friends try it all. These gadgets lead the pack.
from Gear Latest https://ift.tt/4njodvL
via IFTTT
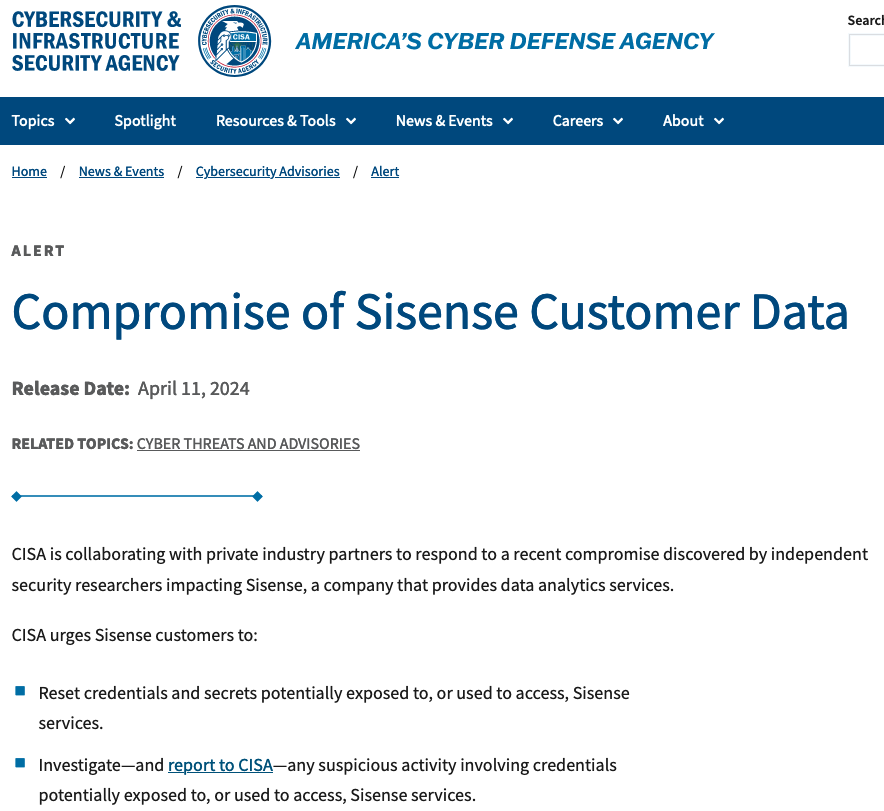
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) said today it is investigating a breach at business intelligence company Sisense, whose products are designed to allow companies to view the status of multiple third-party online services in a single dashboard. CISA urged all Sisense customers to reset any credentials and secrets that may have been shared with the company, which is the same advice Sisense gave to its customers Wednesday evening.
New York City based Sisense has more than 1,000 customers across a range of industry verticals, including financial services, telecommunications, healthcare and higher education. On April 10, Sisense Chief Information Security Officer Sangram Dash told customers the company had been made aware of reports that “certain Sisense company information may have been made available on what we have been advised is a restricted access server (not generally available on the internet.)”
“We are taking this matter seriously and promptly commenced an investigation,” Dash continued. “We engaged industry-leading experts to assist us with the investigation. This matter has not resulted in an interruption to our business operations. Out of an abundance of caution, and while we continue to investigate, we urge you to promptly rotate any credentials that you use within your Sisense application.”
In its alert, CISA said it was working with private industry partners to respond to a recent compromise discovered by independent security researchers involving Sisense.
“CISA is taking an active role in collaborating with private industry partners to respond to this incident, especially as it relates to impacted critical infrastructure sector organizations,” the sparse alert reads. “We will provide updates as more information becomes available.”
Sisense declined to comment when asked about the veracity of information shared by two trusted sources with close knowledge of the breach investigation. Those sources said the breach appears to have started when the attackers somehow gained access to the company’s code repository at Gitlab, and that in that repository was a token or credential that gave the bad guys access to Sisense’s Amazon S3 buckets in the cloud.
Both sources said the attackers used the S3 access to copy and exfiltrate several terabytes worth of Sisent customer data, which apparently included millions of access tokens, email account passwords, and even SSL certificates.
The incident raises questions about whether Sisense was doing enough to protect sensitive data entrusted to it by customers, such as whether the massive volume of stolen customer data was ever encrypted while at rest in these Amazon cloud servers.
It is clear, however, that unknown attackers now have all of the credentials that Sisense customers used in their dashboards.
The breach also makes clear that Sisense is somewhat limited in the clean-up actions that it can take on behalf of customers, because access tokens are essentially text files on your computer that allow you to stay logged in for extended periods of time — sometimes indefinitely. And depending on which service we’re talking about, it may be possible for attackers to re-use those access tokens to authenticate as the victim without ever having to present valid credentials.
Beyond that, it is largely up to Sisense customers to decide if and when they change passwords to the various third-party services that they’ve previously entrusted to Sisense.
Earlier today, a public relations firm working with Sisense reached out to learn if KrebsOnSecurity planned to publish any further updates on their breach (KrebsOnSecurity posted a screenshot of the CISO’s customer email to both LinkedIn and Mastodon on Wednesday evening). The PR rep said Sisense wanted to make sure they had an opportunity to comment before the story ran.
But when confronted with the details shared by my sources, Sisense apparently changed its mind.
“After consulting with Sisense, they have told me that they don’t wish to respond,” the PR rep said in an emailed reply.
Nicholas Weaver, a researcher at University of California, Berkeley’s International Computer Science Institute (ICSI) and lecturer at UC Davis, said a company entrusted with so many sensitive logins should absolutely be encrypting that information.
“If they are hosting customer data on a third-party system like Amazon, it better damn well be encrypted,” Weaver said. “If they are telling people to rest credentials, that means it was not encrypted. So mistake number one is leaving Amazon credentials in your Git archive. Mistake number two is using S3 without using encryption on top of it. The former is bad but forgivable, but the latter given their business is unforgivable.”
from Krebs on Security https://ift.tt/rlivaAQ
via IFTTT
The best gift idea for your dad is a nicer version of something he already owns. The second best is one of these things.
from Gear Latest https://ift.tt/RrlTvhW
via IFTTT

By Tripp Mickle and Brian X. Chen
This fall, the company will begin allowing customers to replace broken parts with used iPhone components without its previous software limits.
Published: April 11, 2024 at 12:50PM
from NYT Technology https://ift.tt/kj3CpXe
via IFTTT
The force has said there was nothing to suggest at the time that the messages were part of a wider pattern
The Metropolitan police first had reports of unsolicited messages targeting a number of MPs, staff and journalists in Westminster last year, but officers failed to notify politicians.
After the former Conservative MP William Wragg said he was manipulated into giving the personal phone numbers of colleagues to a man he met on a dating app, Scotland Yard said it was working with other police forces, alongside its own investigation, amid concerns many other MPs could have been targeted.
from Data and computer security | The Guardian https://ift.tt/KGkvTgA
via IFTTT