Filling cybersecurity roles can be costly, slow, and chancy. More firms are working with third-party service providers to quickly procure needed expertise.
from Dark Reading https://ift.tt/GJsTl7b
via IFTTT

Filling cybersecurity roles can be costly, slow, and chancy. More firms are working with third-party service providers to quickly procure needed expertise.
from Dark Reading https://ift.tt/GJsTl7b
via IFTTT
[Streaming Again] This intense police procedural follows a group of extraordinary FBI profilers who spend their days getting into the minds of psychopathic criminals.
from New On Netflix USA https://ift.tt/WTts1LV
via IFTTT
The state-sponsored threat actor has switched up its tactics, also adding an automated SQL-injection tool to its bag of tricks for initial access.
from Dark Reading https://ift.tt/Jxleyap
via IFTTT
Lazarus continues to expand an aggressive, ongoing spy campaign, using fake Coinbase job openings to lure in victims.
from Dark Reading https://ift.tt/Dlmtpny
via IFTTT
Information on the attributed cyberattacks conducted since the beginning of the Russia-Ukraine war shows that a handful of groups conducted more than two dozen attacks.
from Dark Reading https://ift.tt/kYobV7N
via IFTTT

By BY SHIRA OVIDE
Sales are down, but there is no need to pity the Chromebook.
Published: August 18, 2022 at 11:34AM
from NYT Technology https://ift.tt/A7eOSjw
via IFTTT

Scammers are using invoices sent through PayPal.com to trick recipients into calling a number to dispute a pending charge. The missives — which come from Paypal.com and include a link at Paypal.com that displays an invoice for the supposed transaction — state that the user’s account is about to be charged hundreds of dollars. Recipients who call the supplied toll-free number to contest the transaction are soon asked to download software that lets the scammers assume remote control over their computer.
KrebsOnSecurity recently heard from a reader who received an email from paypal.com that he immediately suspected was phony. The message’s subject read, “Billing Department of PayPal updated your invoice.”
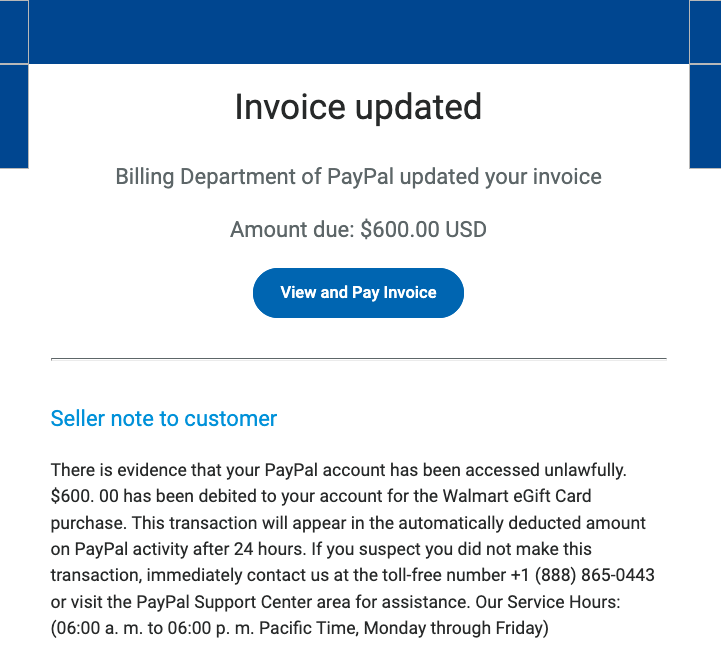
A copy of the phishing message included in the PayPal.com invoice.
While the phishing message attached to the invoice is somewhat awkwardly worded, there are many convincing aspects of this hybrid scam. For starters, all of the links in the email lead to paypal.com. Hovering over the “View and Pay Invoice” button shows the button indeed wants to load a link at paypal.com, and clicking that link indeed brings up an active invoice at paypal.com.
Also, the email headers in the phishing message (PDF) show that it passed all email validation checks as being sent by PayPal, and that it was sent through an Internet address assigned to PayPal.
Both the email and the invoice state that “there is evidence that your PayPal account has been accessed unlawfully.” The message continues:
“$600.00 has been debited to your account for the Walmart Gift Card purchase. This transaction will appear in the automatically deducted amount on PayPal activity after 24 hours. If you suspect you did not make this transaction, immediately contact us at the toll-free number….”
Here’s the invoice that popped up when the “View and Pay Invoice” button was clicked:
The reader who shared this phishing email said he logged into his PayPal account and could find no signs of the invoice in question. A call to the toll-free number listed in the invoice was received by a man who answered the phone as generic “customer service,” instead of trying to spoof PayPal or Walmart. Very quickly into the conversation he suggested visiting a site called globalquicksupport[.]com to download a remote administration tool. It was clear then where the rest of this call was going.
I can see this scam tricking a great many people, especially since both the email and invoice are sent through PayPal’s systems — which practically guarantees that the message will be successfully delivered. The invoices appear to have been sent from a compromised or fraudulent PayPal Business account, which allows users to send invoices like the one shown above. Details of this scam were shared Wednesday with PayPal’s anti-abuse (phish@paypal.com) and media relations teams.
It’s remarkable how well today’s fraudsters have adapted to hijacking the very same tools that financial institutions have long used to make their customers feel safe transacting online. It’s no accident that one of the most prolific scams going right now — the Zelle Fraud Scam — starts with a text message about an unauthorized payment that appears to come from your bank. After all, financial institutions have spent years encouraging customers to sign up for mobile alerts via SMS about suspicious transactions, and to expect the occasional inbound call about possibly fraudulent transactions.
Also, today’s scammers are less interested in stealing your PayPal login than they are in phishing your entire computer and online life with remote administration software, which seems to be the whole point of so many scams these days. Because why rob just one online account when you can plunder them all?
The best advice to sidestep phishing scams is to avoid clicking on links that arrive unbidden in emails, text messages and other mediums. Most phishing scams invoke a temporal element that warns of dire consequences should you fail to respond or act quickly. If you’re unsure whether the message is legitimate, take a deep breath and visit the site or service in question manually — ideally, using a browser bookmark to avoid potential typosquatting sites.
from Krebs on Security https://ift.tt/F4ZLxc9
via IFTTT
LinkedIn privacy settings are just as overwhelming as any other social media settings. There’s a lot of menus, a lot buttons to enable, select, accept or reject. To make sure you have control over your information we bring you a step-by-step guide on how to enjoy LinkedIn safely.
The post A step‑by‑step guide to enjoy LinkedIn safely appeared first on WeLiveSecurity
from WeLiveSecurity https://ift.tt/topKkiL
via IFTTT
How critical is that vulnerability? University researchers are improving predictions of which software flaws will end up with an exploit, a boon for prioritizing patches and estimating risk.
from Dark Reading https://ift.tt/zNE0hok
via IFTTT