Te explicamos cómo utilizar un filtro de luz azul en PC, Mac y otros dispositivos para evitar problemas.
from Tendencias – Digital Trends Español https://ift.tt/2KHsmeI
via IFTTT

Te explicamos cómo utilizar un filtro de luz azul en PC, Mac y otros dispositivos para evitar problemas.
from Tendencias – Digital Trends Español https://ift.tt/2KHsmeI
via IFTTT
Security pros offer up their post-SolarWinds patch-management advice.
from Dark Reading: https://ift.tt/3elfQmw
via IFTTT
Sometimes when a complex story takes us by surprise or knocks us back on our heels, it pays to revisit the events in a somewhat linear fashion. Here’s a brief timeline of what we know leading up to last week’s mass-hack, when hundreds of thousands of Microsoft Exchange Server systems got compromised and seeded with a powerful backdoor Trojan horse program.
When did Microsoft find out about attacks on previously unknown vulnerabilities in Exchange?
Pressed for a date when it first became aware of the problem, Microsoft told KrebsOnSecurity it was initially notified “in early January.” So far the earliest known report came on Jan. 5, from a principal security researcher for security testing firm DEVCOR who goes by the handle “Orange Tsai.” DEVCOR is credited with reporting two of the four Exchange flaws that Microsoft patched on Mar. 2.
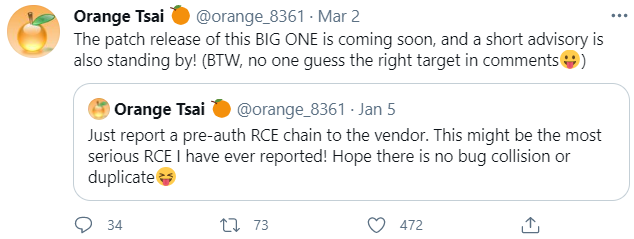
Reston, Va.-based Volexity first identified attacks on the flaws on Jan. 6, and officially informed Microsoft about it on Feb. 2. Volexity now says it can see attack traffic going back to Jan. 3. Microsoft credits Volexity with reporting the same two Exchange flaws as DEVCOR.
Danish security firm Dubex says it first saw clients hit on Jan. 18, and reported their incident response findings to Microsoft on Jan. 27.
In a blog post on their discovery, Please Leave an Exploit After the Beep, Dubex said the victims it investigated in January had a “web shell” backdoor installed via the “unifying messaging” module, a component of Exchange that allows an organization to store voicemail and faxes along with emails, calendars, and contacts in users’ mailboxes.
“A unified messaging server also allows users access to voicemail features via smartphones, Microsoft Outlook and Outlook Web App,” Dubex wrote. “Most users and IT departments manage their voicemail separately from their email, and voicemail and email exist as separate inboxes hosted on separate servers. Unified Messaging offers an integrated store for all messages and access to content through the computer and the telephone.”
Dubex says Microsoft “escalated” their issue on Feb. 8, but never confirmed the zero-day with Dudex prior to the emergency patch release on Mar. 2.
How long have the vulnerabilities exploited here been around?
Microsoft patched four flaws in Exchange Server 2013 through 2019. Exchange Server 2010 is no longer supported, but the software giant made a “defense in depth” exception and gave Server 2010 users a freebie patch, too. That means the vulnerabilities the attackers exploited have been in the Microsoft Exchange Server code base for more than ten years.
The timeline also means Microsoft had almost two months to push out the patch it ultimately shipped Mar. 2, or else help hundreds of thousands of Exchange customers mitigate the threat from this flaw before attackers started exploiting it indiscriminately.

Here’s a rough timeline as we know it so far:
from Krebs on Security https://ift.tt/3t0278R
via IFTTT

OPPO ha renovado su gama media en varios países con móviles que siguen la estética de la marca al tiempo que introducen prestaciones de suficiente nivel. Es el caso del OPPO F19 Pro+, un smartphone lanzado de momento para India que se presenta con la compatibilidad 5G como bandera.
Nuevos aires para el catálogo de móviles de OPPO. Después de haber presentado el OPPO A94 internacionalmente, el fabricante desveló ese mismo teléfono en India como OPPO F19 Pro. No contento con eso, la marca ha presentado allí un modelo superior, el OPPO F19 Pro+. Es bastante similar a su hermano menor, aunque hace gala de un mejor hardware que le abre la puerta a mayores velocidades en redes. No sólo eso.
I see you/And what you do – So be aware/Before you share – And if in doubt/Don’t give it out!
from Naked Security https://ift.tt/3ejMBk1
via IFTTT
The new administration is in an excellent position to make significant progress on data privacy — not just because it’s needed, but also because it’s time.
from Dark Reading: https://ift.tt/3rsjPlh
via IFTTT

Google TV está empezando a introducir los perfiles personalizados para niños, para que los padres puedan escoger a qué aplicaciones tienen acceso, entre otros. La compañía acaba de hacerlo oficial en su blog, mostrando capturas de cómo funcionará este modo.
La función está empezando a implementarse para los Chromecast con Google TV y otros dispositivos con Google TV, primero en Estados Unidos. No obstante, Google asegura que la expansión global llegará en los próximos meses, por lo que es cuestión de tiempo que recibamos esta actualización en nuestro territorio.
{“videoId”:”x7zngd8″,”autoplay”:true,”title”:”LAS MEJORES APPS PARA TU SMART TV: TOP 11 APLICACIONES PARA ANDROID TV GRATIS”}

En su Día Internacional, te damos aquí una muestra de algunas mujeres hispanas que sobresalen en tecnología.
from Tendencias – Digital Trends Español https://ift.tt/2FtoStK
via IFTTT
In the latest Assassin’s Creed installment, I’m playing a Viking during the Dark Ages. Why am I bored?
from Gear Latest https://ift.tt/3kXfDaM
via IFTTT