The New York Times last week ran an interview with several young men who claimed to have had direct contact with those involved in last week’s epic hack against Twitter. These individuals said they were only customers of the person who had access to Twitter’s internal employee tools, and were not responsible for the actual intrusion or bitcoin scams that took place that day. But new information suggests that at least two of them operated a service that resold access to Twitter employees for the purposes of modifying or seizing control of prized Twitter profiles.
As first reported here on July 16, prior to bitcoin scam messages being blasted out from such high-profile Twitter accounts @barackobama, @joebiden, @elonmusk and @billgates, several highly desirable short-character Twitter account names changed hands, including @L, @6 and @W.
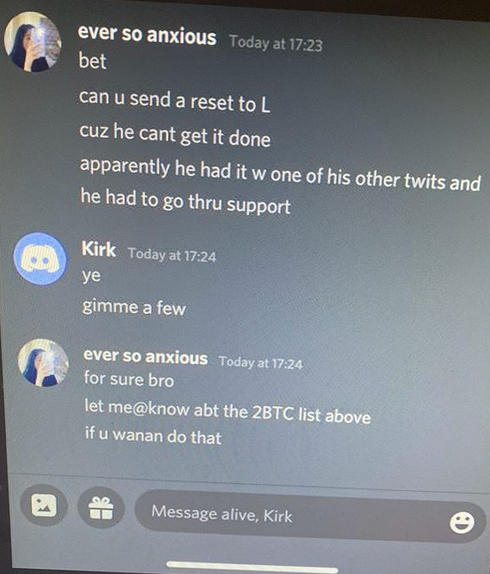
A screenshot of a Discord discussion between the key Twitter hacker “Kirk” and several people seeking to hijack high-value Twitter accounts.
Known as “original gangster” or “OG” accounts, short-character profile names confer a measure of status and wealth in certain online communities, and such accounts can often fetch thousands of dollars when resold in the underground.
The people involved in obtaining those OG accounts on July 15 said they got them from a person identified only as “Kirk,” who claimed to be a Twitter employee. According to The Times, Kirk first reached out to the group through a hacker who used the screen name “lol” on OGusers, a forum dedicated to helping users hijack and resell OG accounts from Twitter and other social media platforms. From The Times’s story:
“The hacker ‘lol’ and another one he worked with, who went by the screen name ‘ever so anxious,’ told The Times that they wanted to talk about their work with Kirk in order to prove that they had only facilitated the purchases and takeovers of lesser-known Twitter addresses early in the day. They said they had not continued to work with Kirk once he began more high-profile attacks around 3:30 p.m. Eastern time on Wednesday.
‘lol’ did not confirm his real-world identity, but said he lived on the West Coast and was in his 20s. “ever so anxious” said he was 19 and lived in the south of England with his mother.
Kirk connected with “lol” late Tuesday and then “ever so anxious” on Discord early on Wednesday, and asked if they wanted to be his middlemen, selling Twitter accounts to the online underworld where they were known. They would take a cut from each transaction.”
Twice in the past year, the OGUsers forum was hacked, and both times its database of usernames, email addresses and private messages was leaked online. A review of the private messages for “lol” on OGUsers provides a glimpse into the vibrant market for the resale of prized OG accounts.
On OGUsers, lol was known to other members as someone who had a direct connection to one or more people working at Twitter who could be used to help fellow members gain access to Twitter profiles, including those that had been suspended for one reason or another. In fact, this was how lol introduced himself to the OGUsers community when he first joined.
“I have a twitter contact who I can get users from (to an extent) and I believe I can get verification from,” lol explained.
In a direct message exchange on OGUsers from November 2019, lol is asked for help from another OGUser member whose Twitter account had been suspended for abuse.
“hello saw u talking about a twitter rep could you please ask if she would be able to help unsus [unsuspend] my main and my friends business account will pay 800-1k for each,” the OGUusers profile inquires of lol.
Lol says he can’t promise anything but will look into it. “I sent her that, not sure if I will get a reply today bc its the weekend but ill let u know,” Lol says.
In another exchange, an OGUser denizen quizzes lol about his Twitter hookup.
“Does she charge for escalations? And how do you know her/what is her department/job. How do you connect with them if I may ask?”
“They are in the Client success team,” lol replies. “No they don’t charge, and I know them through a connection.”
As for how he got access to the Twitter employee, lol declines to elaborate, saying it’s a private method. “It’s a lil method, sorry I cant say.”
In another direct message, lol asks a fellow OGUser member to edit a comment in a forum discussion which included the Twitter account “@tankska,” saying it was his IRL (in real life) Twitter account and that he didn’t want to risk it getting found out or suspended (Twitter says this account doesn’t exist, but a simple text search on Twitter shows the profile was active until late 2019).
“can u edit that comment out, @tankska is a gaming twitter of mine and i dont want it to be on ogu :D’,” lol wrote. “just dont want my irl getting sus[pended].”
Still another OGUser member would post lol’s identifying information into a forum thread, calling lol by his first name — “Josh” — in a post asking lol what he might offer in an auction for a specific OG name.
“Put me down for 100, but don’t note my name in the thread please,” lol wrote.
WHO IS LOL?
The information in lol’s OGUsers registration profile indicates he was probably being truthful with The Times about his location. The hacked forum database shows a user “tankska” registered on OGUsers back in July 2018, but only made one post asking about the price of an older Twitter account for sale.
The person who registered the tankska account on OGUsers did so with the email address jperry94526@gmail.com, and from an Internet address tied to the San Ramon Unified School District in Danville, Calif.
According to 4iq.com, a service that indexes account details like usernames and passwords exposed in Web site data breaches, the jperry94526 email address was used to register accounts at several other sites over the years, including one at the apparel store Stockx.com under the profile name Josh Perry.
Tankska was active only briefly on OGUsers, but the hacked OGUsers database shows that “lol” changed his username three times over the years. Initially, it was “freej0sh,” followed by just “j0sh.”
lol did not respond to requests for comment sent to email addresses tied to his various OGU profiles and Instagram accounts.
ALWAYS IN DISCORD
Last week’s story on the Twitter compromise noted that just before the bitcoin scam tweets went out, several OG usernames changed hands. The story traced screenshots of Twitter tools posted online back to a moniker that is well-known in the OGUsers circle: PlugWalkJoe, a 21-year-old from the United Kingdom.
Speaking with The Times, PlugWalkJoe — whose real name is Joseph O’Connor — said while he acquired a single OG Twitter account (@6) through one of the hackers in direct communication with Kirk, he was otherwise not involved in the conversation.
“I don’t care,” O’Connor told The Times. “They can come arrest me. I would laugh at them. I haven’t done anything.”
In an interview with KrebsOnSecurity, O’Connor likewise asserted his innocence, suggesting at least a half dozen other hacker handles that may have been Kirk or someone who worked with Kirk on July 15, including “Voku,” “Crim/Criminal,” “Promo,” and “Aqua.”
“That twit screenshot was the first time in a while I joke[d], and evidently I shouldn’t have,” he said. “Joking is what got me into this mess.”
O’Connor shared a number of screenshots from a Discord chat conversation on the day of the Twitter hack between Kirk and two others: “Alive,” which is another handle used by lol, and “Ever So Anxious.” Both were described by The Times as middlemen who sought to resell OG Twitter names obtained from Kirk. O’Connor is referenced in these screenshots as both “PWJ” and by his Discord handle, “Beyond Insane.”
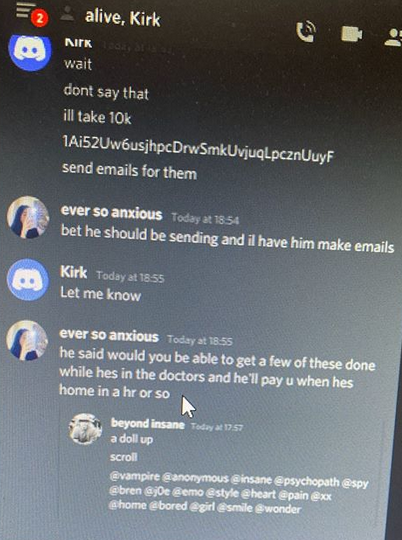
The negotiations over highly-prized OG Twitter usernames took place just prior to the hijacked celebrity accounts tweeting out bitcoin scams.
Ever So Anxious told Kirk his OGU nickname was “Chaewon,” which corresponds to a user in the United Kingdom. Just prior to the Twitter compromise, Chaewon advertised a service on the forum that could change the email address tied to any Twitter account for around $250 worth of bitcoin. O’Connor said Chaewon also operates under the hacker alias “Mason.”
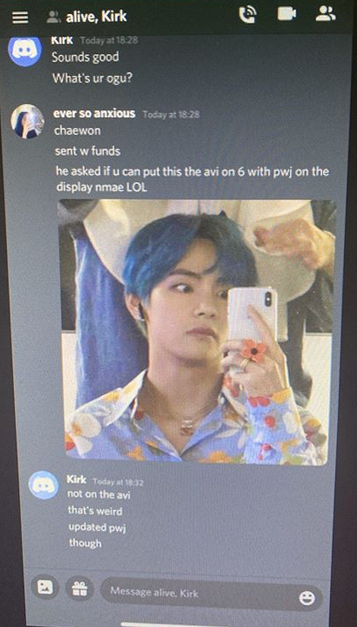
“Ever So Anxious” tells Kirk his OGUsers handle is “Chaewon,” and asks Kirk to modify the display names of different OG Twitter handles to read “lol” and “PWJ”.
At one point in the conversation, Kirk tells Alive and Ever So Anxious to send funds for any OG usernames they want to this bitcoin address. The payment history of that address shows that it indeed also received approximately $180,000 worth of bitcoin from the wallet address tied to the scam messages tweeted out on July 15 by the compromised celebrity accounts.
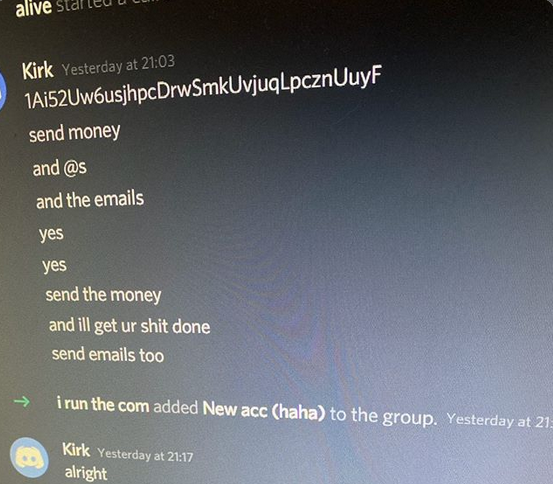
The Twitter hacker “Kirk” telling lol/Alive and Chaewon/Mason/Ever So Anxious where to send the funds for the OG Twitter accounts they wanted.
SWIMPING
My July 15 story observed there were strong indications that the people involved in the Twitter hack have connections to SIM swapping, an increasingly rampant form of crime that involves bribing, hacking or coercing employees at mobile phone and social media companies into providing access to a target’s account.
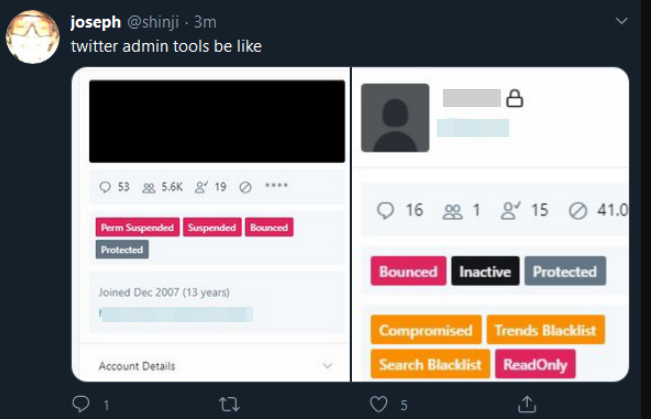
The account “@shinji,” a.k.a. “PlugWalkJoe,” tweeting a screenshot of Twitter’s internal tools interface.
SIM swapping was thought to be behind the hijacking of Twitter CEO Jack Dorsey‘s Twitter account last year. As recounted by Wired.com, @jack was hijacked after the attackers conducted a SIM swap attack against AT&T, the mobile provider for the phone number tied to Dorsey’s Twitter account.
Immediately after Jack Dorsey’s Twitter handle was hijacked, the hackers tweeted out several shout-outs, including one to @PlugWalkJoe. O’Connor told KrebsOnSecurity he has never been involved in SIM swapping, although that statement was contradicted by two law enforcement sources who closely track such crimes.
However, Chaewon’s private messages on OGusers indicate that he very much was involved in SIM swapping. Use of the term “SIM swapping” was not allowed on OGusers, and the forum administrations created an automated script that would watch for anyone trying to post the term into a private message or discussion thread.
The script would replace the term with “I do not condone illegal activities.” Hence, a portmanteau was sometimes used: “Swimping.”
“Are you still swimping?” one OGUser member asks of Chaewon on Mar. 24, 2020. “If so and got targs lmk your discord.” Chaewon responds in the affirmative, and asks the other user to share his account name on Wickr, an encrypted online messaging app that automatically deletes messages after a few days.
Chaewon/Ever So Anxious/Mason did not respond to requests for comment.
O’Connor told KrebsOnSecurity that one of the individuals thought to be associated with the July 15 Twitter hack — a young man who goes by the nickname “Voku” — is still actively involved in SIM-swapping, particularly against customers of AT&T and Verizon.
Voku is one of several hacker handles used by a Canton, Mich. youth whose mom turned him in to the local police in February 2018 when she overheard him talking on the phone and pretending to be an AT&T employee. Officers responding to the report searched the residence and found multiple cell phones and SIM cards, as well as files on the kid’s computer that included “an extensive list of names and phone numbers of people from around the world.”
The following month, Michigan authorities found the same individual accessing personal consumer data via public Wi-Fi at a local library, and seized 45 SIM cards, a laptop and a Trezor wallet — a hardware device designed to store crytpocurrency account data. In April 2018, Voku’s mom again called the cops on her son — identified only as confidential source #1 (“CS1”) in the criminal complaint against him — saying he’d obtained yet another mobile phone.
Voku’s cooperation with authorities led them to bust up a conspiracy involving at least nine individuals who stole millions of dollars worth of cryptocurrency and other items of value from their targets.
CONSPIRACY
Samy Tarazi, an investigator with the Santa Clara County District Attorney’s Office, has spent hundreds of hours tracking young hackers during his tenure with REACT, a task force set up to combat SIM swapping and bring SIM swappers to justice.
According to Tarazi, multiple actors in the cybercrime underground are constantly targeting people who work in key roles at major social media and online gaming platforms, from Twitter and Instagram to Sony, Playstation and Xbox.
Tarazi said some people engaged in this activity seek to woo their targets, sometimes offering them bribes in exchange for the occasional request to unban or change the ownership of specific accounts.
All too often, however, employees at these social media and gaming platforms find themselves the object of extremely hostile and persistent personal attacks that threaten them and their families unless and until they give in to demands.
“In some cases, they’re just hitting up employees saying, ‘Hey, I’ve got a business opportunity for you, do you want to make some money?’” Tarazi explained. “In other cases, they’ve done everything from SIM swapping and swatting the victim many times to posting their personal details online or extorting the victims to give up access.”
Allison Nixon is chief research officer at Unit 221B, a cyber investigations company based in New York. Nixon says she doesn’t buy the idea that PlugWalkJoe, lol, and Ever So Anxious are somehow less culpable in the Twitter compromise, even if their claims of not being involved in the July 15 Twitter bitcoin scam are accurate.
“You have the hackers like Kirk who can get the goods, and the money people who can help them profit — the buyers and the resellers,” Nixon said. “Without the buyers and the resellers, there is no incentive to hack into all these social media and gaming companies.”
Mark Rasch, Unit 221B’s general counsel and a former U.S. federal prosecutor, said all of the players involved in the Twitter compromise of July 15 can be charged with conspiracy, a legal concept in the criminal statute which holds that any co-conspirators are liable to the acts of any other co-conspirator in furtherance of the crime, even if they don’t know who those other people are in real life or what else they may have been doing at the time.
“Conspiracy has been called the prosecutor’s friend because it makes the agreement the crime,” Rasch said. “It’s a separate crime in addition to the underlying crime, whether it be breaking in to a network, data theft or account takeover. The ‘I just bought some usernames and gave or sold them to someone else’ excuse is wrong because it’s a conspiracy and these people obviously don’t realize that.”
In a statement on its ongoing investigation into the July 15 incident, Twitter said it resulted from a small number of employees being manipulated through a social engineering scheme. Twitter said at least 130 accounts were targeted by the attackers, who succeeded in sending out unauthorized tweets from 45 of them and may have been able to view additional information about those accounts, such as direct messages.
On eight of the compromised accounts, Twitter said, the attackers managed to download the account history using the Your Twitter Data tool. Twitter added that it is working with law enforcement and is rolling out additional company-wide training to guard against social engineering tactics.
from Krebs on Security https://ift.tt/3eYycXu
via IFTTT